CVE-2023-22527 poses a significant risk to enterprises and individuals relying on Atlassian Confluence. Understanding and addressing this vulnerability is essential to protecting sensitive data and maintaining the integrity of IT systems. In this blog, we will delve into the details of CVE-2023-22527, its potential impact, and the steps needed to mitigate this threat.
Here’s what you need to know:
What is CVE-2023-22527?
CVE-2023-22527 is a critical vulnerability identified in Atlassian Confluence Data Center and Server. This flaw is classified as a template injection vulnerability that permits remote code execution (RCE) without the need for authentication. It has been assigned the highest severity rating with a CVSS score of 10, indicating its potential to cause significant damage.
The vulnerability arises due to improper input validation, allowing attackers to execute arbitrary code on the Confluence server. This poses a severe risk to organizations as it can lead to unauthorized access and control over affected systems.
Does it affect me?
If your organization utilizes Atlassian Confluence Data Center or Server versions prior to 8.5.4, you are potentially at risk from CVE-2023-22527. This vulnerability specifically impacts these versions, making it critical for administrators and IT professionals to ascertain their current version.
Notably, Confluence Cloud users are not affected by this vulnerability.
Has CVE-2023-22527 been actively exploited in the wild?
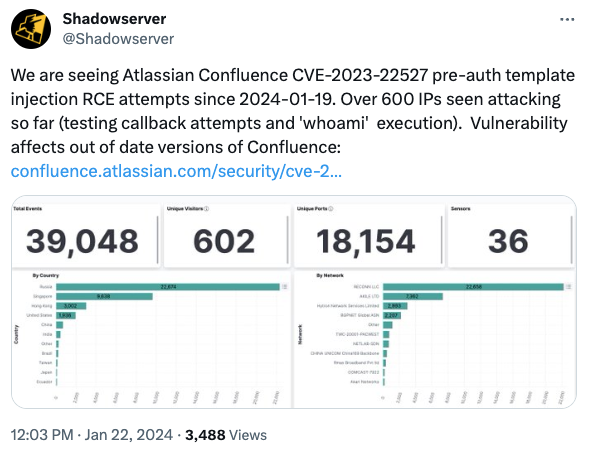
Yes, CVE-2023-22527 has been actively exploited. Reports indicate a significant number of attacks, highlighting the urgency of this threat. The data collected shows numerous exploit attempts, with attackers actively seeking to take advantage of this vulnerability.
Fixing CVE-2023-22527
To mitigate the risks associated with CVE-2023-22527, the immediate action is to update Atlassian Confluence to the latest version. Atlassian has released patches for the affected versions, and applying these updates is crucial to safeguarding your systems.
It’s essential to regularly monitor and install updates for all software, as they often include critical security fixes. Additionally, consider conducting a security audit to ensure no unauthorized access has occurred and reinforce overall cybersecurity practices.
Next steps
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:








