Atlassian is urging users to take action on a critical vulnerability found in its Questions for Confluence app – one of three major bugs announced last week.
With Confluence in use across millions of systems for project management and collaboration needs, a critical vulnerability in the product has the potential to cause huge damage if left unresolved.
Here’s everything you need to know about CVE-2022-26138.
What is the CVE-2022-26138 vulnerability?
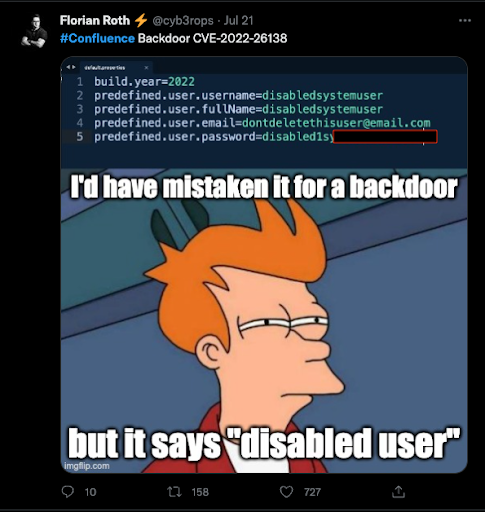
When the “Questions for Confluence” application is enabled on the Confluence Server or the Data Center, it creates a Confluence user account with the username “disabledsystemuser”.
The “disabledsystemuser” account is created with a hardcoded password and is added to the confluence-users group, which allows viewing and editing all non-restricted pages within Confluence by default.
An attacker could exploit this vulnerability in order to log into Confluence and access all the pages the “confluence-users” group has access to.
Does CVE-2022-26138 affect me?
Below are the versions of the app that create the “disabledsystemuser” account with a hardcoded password. Note that Confluence installations that do not actively have any of these versions of the app installed may still be affected.
- Questions for Confluence 2.7.34
- Questions for Confluence 2.7.35
- Questions for Confluence 3.0.2
Because the vulnerability still exists even if the application has been uninstalled, it is recommended that you verify whether you are vulnerable.
In order to do this, check if there is an active user account with the following information in your Confluence Server or Data Center Instance:
- User: disabledsystemuser
- Username: disabledsystemuser
- Email: [email protected]
If this account does not show up in the list of active users, the Confluence instance is not affected.
Has CVE-2022-26138 been actively exploited in the wild?
Yes,
The password was leaked and published on Twitter.
Fixing CVE-2022-26138
There are two options to mitigate this vulnerability:
1) Update to a non-vulnerable version of Questions for Confluence
2) Disable or delete the disabledsystemuser account
Imoportent Note: deleting the “Questions for Confluence” app will not resolve the issue and the user will still exist.
Next steps
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:
- https://vulcan.io/blog/the-most-common-cves-and-how-to-fix-them/
- https://vulcan.io/blog/fixing-cve-2021-34527/
- https://mitremapper.voyager18.io/
- https://cyber-risk-community.slack.com/ssb/redirect
- https://vulcan.io/remedy-cloud/
And finally…
Don’t get found out by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your threat environment and lets you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.