First Officer’s log, Terrestrial date, 20220822. Officer of the Deck reporting.
Several of the ship’s departments have been working diligently towards an updated communication interface, which will let the worlds we serve, and the ones we are ready to serve, better understand our mission and what we can do to improve their situations. It’s been a daunting task, but we are looking forward to the improvements once the new interface is available on the subspace network.
In the meantime, we continue our mission, helping worlds get the most of their own integrated defenses.
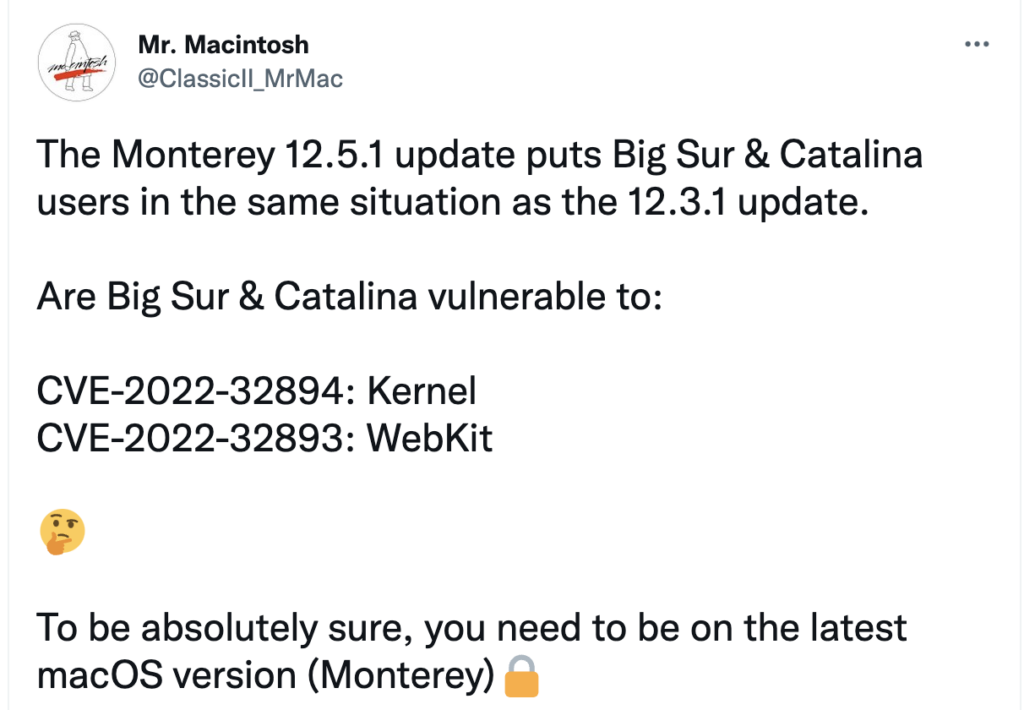
You can’t hack a Mac. Except when you can.
What happened
Back before Apple moved to Intel chips from PowerPC, the phrase “you can’t hack a Mac” had a kernel of truth. Now, while Apple’s products tend to be reasonably secure, they are still quite hackable. The issues here (CVE-2022-32893 and CVE-2022-32894) affect iOS, iPadOS, and MacOS. Fortunately, patches are already out for these. Apple’s hinted that these vulnerabilities have been exploited in the world already, so patches should go in sooner rather than later.
You do have automatic updates enabled, right?
Why it matters
Apple devices have a large market share and a huge number of devices installed, both in consumer and corporate spaces. Even before the current remote work situation, people were using their personal Macs and iPhones in Bring Your Own Device (BYOD) workplaces to get work done. That can make it a challenge for Enterprise environments that may not have as much control as they’d like over BYOD devices.
What they said
Vulnerabilities in Apple devices are thankfully not an everyday occurrence. But with Mac hacked, you can be sure there’ll be plenty of coverage. Here’s what people are saying.
No, really, I am the server you want.
What happened
A recently discovered vulnerability in the Windows Server Service could lead to a threat actor spoofing a legitimate server, with all the fun and games that implies. While there is no evidence that it’s been done in the wild and it does take some special circumstances, it’s just another reason to keep your Microsoft patches up to date.
Wasn’t there something about automatic updates?
Well, at least where they don’t break the change management process.
Why it matters
There’s no evidence this vulnerability has been exploited, and it will be a challenge for an attacker to get into the circumstances needed to exploit it. But server spoofing is problematic. There are a lot of interactions between systems that rely on some level of “trust” and spoofing can break that trust. How bad the situation becomes depends on the specifics but can range from “that’s bad” to “a newsworthy event.”
And, in this context, no one wants a newsworthy event.
What they said
It didn’t take long for people to start talking. Read more.
_______________________________________________________________________________________________________________________
Vulcan Cyber has a lot of SciFi Nerd culture at our core, and some of you may have noticed a bit of a Cali Class Cruiser vibe here in my blog. This is, of course, intentional. I see a parallel between what we do in Risk Management with what those fictional Lower Decks ships do. It’s not always glamorous, but it’s still vital. Unfortunately, I haven’t quite hit on the story to tell here.
To that end, I’d love to get input from our readers. There’s a thread on our public Slack community, and I’d like to invite anyone who finds the idea amusing to come and share in some fun.