The 2023 CWE Top 10 KEV Weaknesses list provides a critical overview of the most prevalent and severe software weaknesses that could lead to exploitable vulnerabilities. These weaknesses are evaluated based on their prevalence in reported vulnerabilities, potential for exploitation, and impact. This list is essential for developers, security professionals, and organizations to understand and prioritize security efforts in software development and maintenance, helping to prevent common and impactful security flaws in software systems.
The CWE top 10 KEV provides a different view than the commonly used OWASP top 10 or CWE top 25 which is centered on threats exploited in the wild, helping software developers utilize threat intelligence to prioritize remediation in a more effective way.
For more details, you can visit the CWE Top 10 KEV Weaknesses page.
Here’s everything we learned from this year’s list:
The 2023 CWE Top 10 KEV Weaknesses
|
KEV Weaknesses Rank |
CWE-ID |
Weakness Name |
Analysis Score |
Number of Mappings in the KEV Dataset |
Average CVSS |
|
1 |
Use After Free |
73.99 |
44 |
8.54 |
|
|
2 |
Heap-based Buffer Overflow |
56.56 |
32 |
8.79 |
|
|
3 |
Out-of-bounds Write |
51.96 |
34 |
8.19 |
|
|
4 |
Improper Input Validation |
51.38 |
33 |
8.27 |
|
|
5 |
Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) |
49.44 |
25 |
9.36 |
|
|
6 |
Deserialization of Untrusted Data |
29.00 |
16 |
9.06 |
|
|
7 |
Server-Side Request Forgery (SSRF) |
27.33 |
16 |
8.72 |
|
|
8 |
Access of Resource Using Incompatible Type (‘Type Confusion’) |
26.24 |
16 |
8.61 |
|
|
9 |
Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) |
19.90 |
14 |
8.09 |
|
|
10 |
Missing Authentication for Critical Function |
12.98 |
8 |
8.86 |
Insights on the 2023 CWE Top 10 KEV Weaknesses
In 2021, the Cybersecurity and Infrastructure Security Agency (CISA) introduced the “Known Exploited Vulnerabilities (KEV) Catalog,” which lists vulnerabilities reported through the Common Vulnerabilities and Exposures (CVE®) program that have been actively exploited. CISA advises organizations to use this catalog to prioritize fixing these vulnerabilities in their systems to reduce the risk of compromise.
The concept of a “weakness” refers to conditions in software, firmware, hardware, or services that can lead to vulnerabilities. The CWE List describes these weaknesses, and the CWE Top 25 annually ranks the most prevalent and severe weaknesses based on CVE Records. This ranking is based on the prevalence (the number of CVE Records with a particular weakness) and severity (the average CVSS score of these records). Notably, whether a vulnerability is actively exploited is not a mandatory part of the CVE reporting process.
By analyzing the CWE root causes of vulnerabilities known to be exploited, insights into the weaknesses that adversaries target are gained. This analysis includes all CVE Records from 2021 and 2022 in the KEV catalog, leading to the creation of the first ever Top 10 KEV Weaknesses List. This list, along with the 2023 CWE Top 25, helps organizations mitigate risks more effectively.
In early 2023, the CWE site published View-1400, categorizing entries for large-scale software assurance research. This aims to support efforts to eliminate weaknesses and track trends in public vulnerability data. The 2023 CWE Top 10 KEV Weaknesses list revealed that the top three entries are related to Memory Safety.
The CWE Top 10 KEV Weaknesses list shows notable differences from the 2023 CWE Top 25. Some weaknesses rank higher in the KEV list despite a lower ranking in the Top 25. For example, “Use After Free” and “Improper Input Validation” are more prominent in the KEV list. Conversely, weaknesses like “Cross-site Scripting” and “SQL Injection,” high on the Top 25, are absent from the KEV list. These differences highlight various factors, including ease of exploitation, impact desirability, and detection by code scanning tools. Understanding reported vulnerabilities along with knowledge of actual exploitation provides crucial insights for informing system development with practical security considerations.
Meanwhile, comparisons with the OWASP Top 10 vulnerabilities also yields some interesting insights. Based on our platform data, viewing risks through the lens of the CWE KEV top 10 can reduce the number of prioritized vulnerabilities to less than half of what the same analysis would bring using OWASP’s data.
Nex steps with Vulcan Cyber
At Vulcan Cyber, we are dedicated to championing efforts that bring to light vital cyber security concerns in our sector. Fulfilling our responsibility, we furnish our community with a wealth of resources and tools that are essential for a better grasp, effective prioritization, and minimization of cyber security risks.
And users of our platform can monitor and prioritize based on CWEs, CISA KEV, or proprietary threat intelligence:
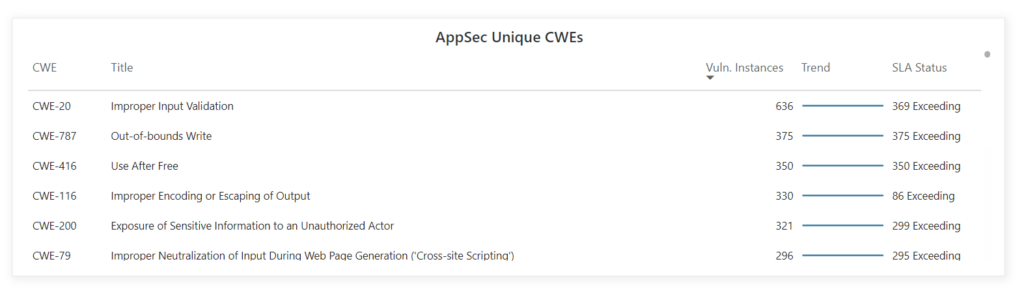
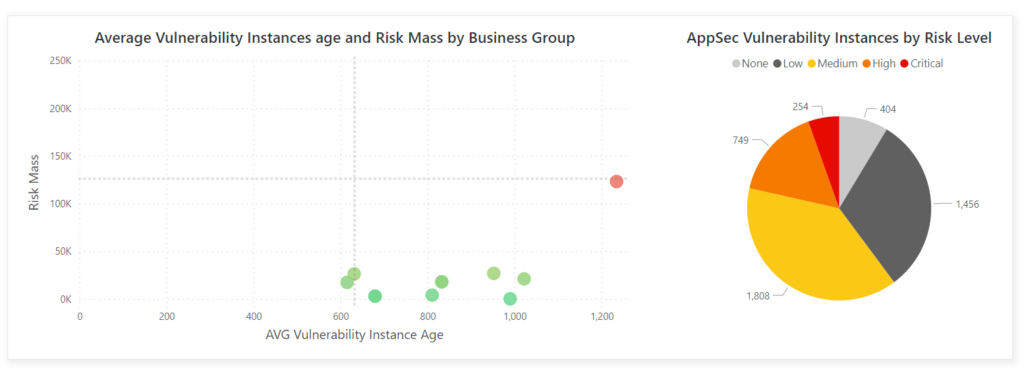
To learn how you can leverage the Vulcan Cyber exposure management platform to give you a unified view of your entire risk landscape, book your demo today.