Everyone depends on OpenSSL to secure Transport Layer Security (TLS) on Linux, Unix, Windows and many other operating systems. It’s also used to lock down pretty much every secure communications and networking application and device out there.
With it being so ubiquitous, the recent news of a critical Open SSL vulnerability demands our attention. Here’s what we know so far:
What is the OpenSSL vulnerability?
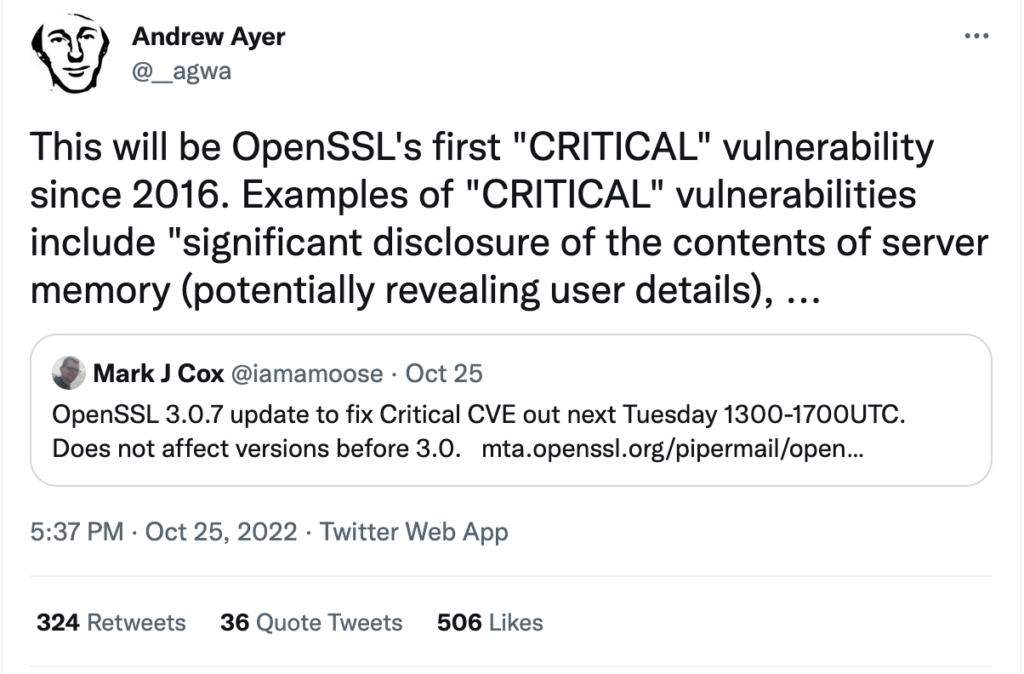
OpenSSL version 3.0.7 is scheduled to be released on Tuesday, November 1, between 13:00 and 17:00 UTC. Not many details have been provided yet, but this release has been described as a ‘security-fix release’ that will include a patch for a vulnerability rated ‘critical.’
Does it affect me?
In a twist to the usual protocol, the project is giving the world a week’s advance notice of the impending patch, and it is a good idea to prepare now. OpenSSL is widely considered to be a part of the critical infrastructure of the Internet – among other things generating the certificates that allow websites to run over HTTPS.
At the time of writing, it appears that only OpenSSL versions between 3.0-> 3.0.6 are affected, and this critical security vulnerability is fixed in the upcoming 3.0.7 release. OpenSSL 3 is widely adopted, but current surveys indicate that it’s still far outweighed by the OpenSSL 1.x distribution that is mostly out of LTS today – and entirely so after September 2023.
However, there are 62 wrapper packages distributed by the world’s largest Java Open Source ecosystem – Maven Central – that repackage OpenSSL. It is more often included in a project transitively or required from the system by a piece of software. Indeed, any application that provides a web server, or uses a web server, could run on server software that relies on an outdated version.
For Vulcan Cyber customers, and Vulcan Free users, we suggest to prepare now by identifying all your assets using the OpenSSL3 package with our clusters feature, which aggregates all your vulnerabilities by asset cluster based on the vulnerable item (package in this case).
Fixing the OpenSSL vulnerability
On Tuesday, November 1, the project will release a new version of OpenSSL (version 3.0.7) that will patch an as-yet-undisclosed flaw in current versions of the technology.
We recommend that you identify all your vulnerable assets running OpenSSL3 and be prepared for the update.
Next steps
Each new vulnerability is a reminder of where we stand, and that we need to do better. Check out the following resources to help you maintain cyber hygiene, reduce vulnerability risk exposure and stay ahead of threat actors:
- The most common CVEs (and how to fix them)
- Exploit maturity: an introduction
- Mapping CVEs to the MITRE ATT&CK framework
- The Vulcan Cyber community Slack channel
- Vulcan Remedy Cloud
And finally…
Don’t get caught unprepared by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your cyber risk security posture and helps you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.