Late last week we called attention to the fact that OpenSSL had identified (without any specific details) a critical OpenSSL3 vulnerability and was going to release an update to address it today. As of this morning, OpenSSL released the source code for version 3.0.7 which is designed to mitigate CVE-2022-3786 and CVE-2022-3602. Download OpenSSL 3.0.7 here.
CVEs for the OpenSSL3 vulnerability
CVE-2022-3786 and CVE-2022-3602 have been published with the following OpenSSL3 vulnerability descriptions:
“A buffer overrun can be triggered in X.509 certificate verification, specifically in name constraint checking,” meaning it is happening during the authentication phase, and can be triggered on both TLS client and server.
Both vulnerabilities occur after the certificate chain signature verification, and it “requires either a CA to have signed a malicious certificate or for an application to continue certificate verification despite failure to construct a path to a trusted issuer.”ֿ
The potential impact of CVE-2022-3786 is a denial-of-service (DoS) attack. It is critical, but is just a precursor to CVE-2022-3602 which can be even more severe and lead to remote code execution.
Fortunately these vulnerabilities come with a retraction of sorts from OpenSSL and they’ve said their first estimation of CVE-2022-3602 as “CRITICAL” was inaccurate after they researched stack overflow protection mechanisms in today’s compilers.
The risk was reduced to “HIGH” because, “The risk may be further mitigated based on stack layout for any given platform/compiler.”
A more in-depth explanation about the change to the vulnerability risk rating can be found here.
Act now to mitigate CVE-2022-3786 and CVE-2022-3602 by updating OpenSSL to version 3.0.7 and reduce the risk of a potential DoS or RCE attack.
Are there any known OpenSSL3 vulnerability exploits in the wild?
OpenSSL claims they have not seen any evidence of exploitation of the OpenSSL3 vulnerabilities in the wild.
How can I identify OpenSSL3 vulnerabilities in my environment?
Vulcan Cyber can be used to identify assets affected with the OpenSSL3 vulnerabilities even if your vulnerability scanners aren’t picking it up yet. If you are running Vulcan Enterprise or Vulcan Free, a new dashboard widget identifies assets that may be affected and vulnerable to older versions of OpenSSL3.
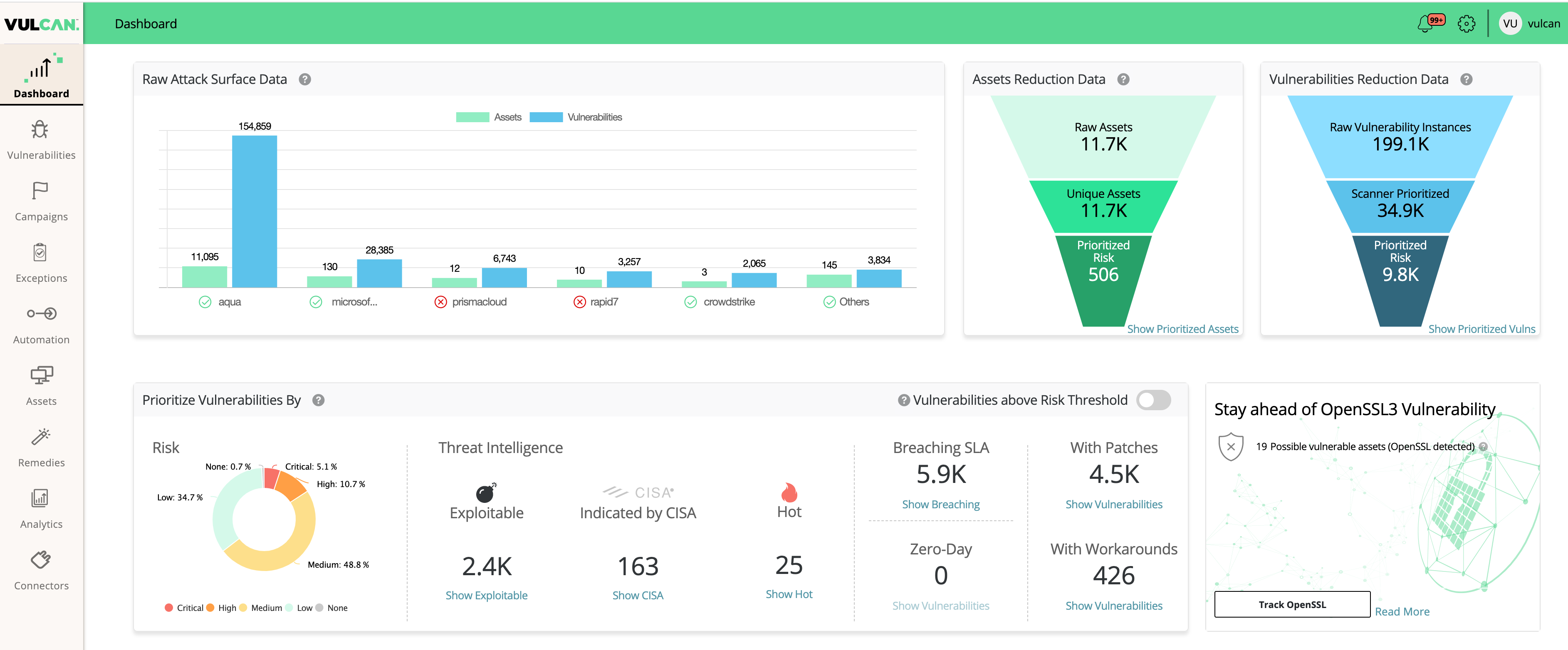
Next steps to mitigate the OpenSSL3 vulnerability
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: