-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Postman, a widely used API development and testing platform, has recently been at the center of a concerning data leak incident. This platform, relied upon by developers globally, inadvertently exposed sensitive information due to improper handling of API keys, tokens, and other secrets. In this blog post, we delve into the details of these leaks, the underlying causes, and the broader implications for security in API management tools.

The primary cause of these leaks lies in the improper use of Postman’s sharing features. Postman allows users to create and share workspaces for collaboration. However, without strict access controls, these workspaces can become publicly accessible, leading to the inadvertent exposure of sensitive data. Researchers highlighted several key issues:
1. Misconfigured Sharing Permissions – Developers often shared workspaces without understanding the visibility settings. Publicly shared workspaces could be indexed by search engines or accessed by anyone with the URL. These workspaces contained environment files with embedded API keys, tokens, and sometimes plaintext passwords.
2. Lack of Secrets Management – Many Postman users stored sensitive credentials directly in environment variables within the tool. While Postman offers features like secret management, not all users adopted them, leaving their data exposed.
3. Absence of Proper API Key Rotation – Even when API keys were leaked, organizations often failed to rotate them promptly. This oversight allowed attackers to exploit the exposed keys for extended periods, potentially leading to unauthorized access to services or databases.
4. Insufficient Awareness and Training – A significant contributing factor to these leaks was the lack of awareness among developers about the security implications of sharing Postman environments. Training gaps meant that best practices for secrets management and workspace sharing were often overlooked.
The researchers first found leaked refresh token with session secret and API Call: The team discovered a serious leak in a public Postman workspace where a refresh token and session secret of a major CRM software which they had exposed. Furthermore, the API endpoint for generating access tokens was included as well, allowing unauthorized users to potentially exploit the entire token lifecycle.
For POC purposes, the researchers also tried reproducing the query mentioned in the exposed Postman workspace – a query that generates a public URL for a given dashboard page entity GUID. The dashboard page can then be accessed in the form of a static snapshot in the resulting public URL.
curl --location 'https://api.newrelic.com/graphql' \ --header 'API-Key: NRAK-257VYH6ITPM09G0M71C6FX48J82' \ --header 'Content-Type: application/json' \ --header 'guid: MTcyMTQ0MnxWSVp8REFTSEJPQVJEfGRhOjQxMTM1' \ --data '{"query":"mutation ($guid: EntityGuid!) {\r\n dashboardCreateSnapshotUrl(guid: $guid, params: {timeWindow: {duration: 604800000}})\r\n}\r\n\r\n","variables":{"guid":"MTcyMTQ0MnxWSVp8REFTSEJPQVJEfDEyNTE1MTM"}}'
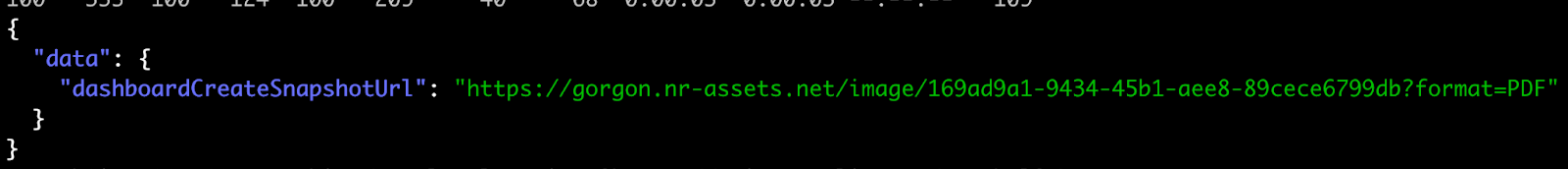
Public URL returned by the API, from: cloudsek.com/
The consequences of these leaks were far-reaching. In one instance, researchers found API keys that provided full administrative access to critical cloud resources. Such access could enable attackers to deploy malicious code, exfiltrate sensitive data, or disrupt services. Additionally, exposed credentials for payment gateways and third-party APIs posed financial risks, including unauthorized transactions and fraud.
The leaks also highlighted broader issues in the software development lifecycle. The over-reliance on manual processes for managing API security credentials and the lack of automated secrets scanning tools exacerbated the problem. Organizations affected by these leaks faced reputational damage, regulatory scrutiny, and significant remediation costs.
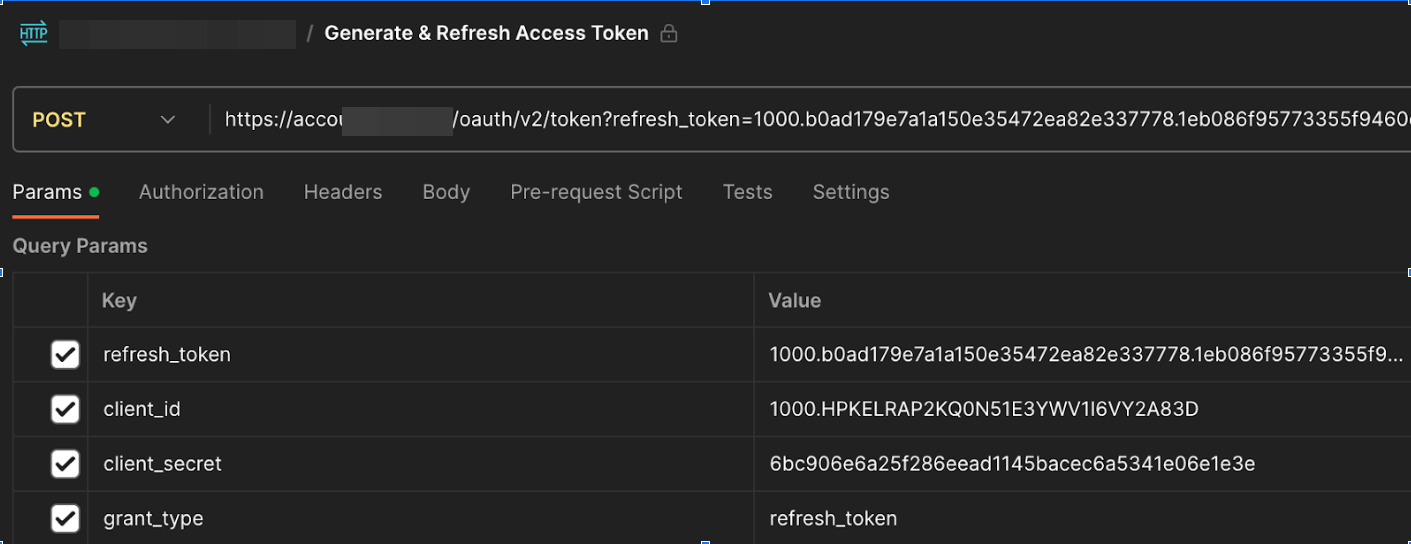
Leaked Credentials of postman in the public Postman workspace, from: cloudsek.com/
To prevent similar incidents, organizations and developers must adopt comprehensive security measures for API management tools like Postman. These include:
Following the disclosure of these findings, a new secret-protection policy has been implemented by Postman to prevent the exposure of sensitive data in public workspaces. In case secrets are detected, this new policy alerts users, offers resolutions, and facilitates transitions to private or team workspaces.
The company also stated: “Starting this month, we are removing public workspaces with known exposed secrets from the Public API Network. As we roll out this policy change, owners of public workspaces containing secrets will be notified and could remove their exposed secrets before that workspace is removed from the network”.
The Postman data leaks underscore the critical need for robust security practices in API development and management. While the platform itself provides numerous features to safeguard sensitive information, the onus remains on developers and organizations to use these features effectively.
The collaborative efforts of researchers have been instrumental in bringing these issues to light and driving the conversation around secure API practices.
As API usage continues to grow, so too must our vigilance in securing the tools and environments that power modern software development. By adopting the recommended best practices and fostering a culture of security awareness, we can mitigate the risks associated with API data leaks and ensure a safer digital ecosystem.
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: