First Officer’s log, Terrestrial date, 20221114. Officer of the Deck reporting.
We have arrived at Frontier Station [REDACTED] to participate in a series of infrastructure projects, with our part focused on coordinating communications across the different divisions. It’s a role we are well suited to as a support ship with an experienced crew.
What most of us had not realized at the time was that the station was playing host to a 3D Chess tournament while the projects were going on. Since the projects were mostly away from the publicly accessible parts of the station, it was a non-issue.
It also turned out that a newly assigned Ensign was not simply a 3D chess enthusiast but was something of a prodigy at the game. So much so, that he had brought with him a set that had evidently been aboard the Federation’s flagship a generation or so back, that was apparently used by the ship’s captain and first officer in their own frequent games.
Whether that bit of trivia was true or not didn’t matter, though the Ensign requested liberty to join the tournament as soon as we took up position near the facility
Given the Ensign’s enthusiasm, the positive attention it could bring to our mission, and the fact that competitors had arrived from multiple worlds, the captain agreed and allowed Ensign [REDACTED] to sign up for the tournament.
While there were a few serious players on the crew, 3D chess wasn’t usually considered a spectator sport. However, with one of our own on the roster and not much else to do on a Frontier class station during our downtime, a fan club was quickly forming around the event.
No one is surprised they attack the infrastructure
What happened
Microsoft’s 2022 Digital Defense Report pointed to a large rise in attacks against critical infrastructure, with the attacks largely led by state-level actors such as Russia, China, North Korea, and Iran. In particular, they noted that Russian attacks were reaching beyond the battlefields of Ukraine as a way to disrupt Western allies supporting Ukraine in the conflict.
Why it matters
Given the current geopolitical situation, it’s no surprise that cyberattacks are reaching far beyond the military combat zones. They are a form of asymmetric warfare that can interfere with an opponent without escalating to a more conventional fight. This sort of attack can also be used by antagonists that are not considered peer or near-peer to level the playing field against a much better-equipped adversary.
Add in the fact that these attacks can pose as cybercriminal attacks rather than the actions of a nation-state, and they become even more attractive.
What they said
Attacks from state-level actors often carry more significance than the average attack, so it’s no surprise to see this story getting attention.
Did the US election dodge a metaphorical bullet?
What happened
Both the FBI and CISA stated ahead of the November 8th US elections that it did not appear that local election stations had suffered cyber-attacks, or that any cybercriminal disruption was likely during the election itself. Attacks that were seen were either blocked or mitigated with minimal effect.
Why it matters
Election security has been a major concern since before the Presidental elections in 2016, which led to that, and subsequent elections, being some of the most secure in US history. In spite of loud claims to the contrary, there was no evidence of large-scale election tampering or fraud. Any irregularities that were seen were within the expected ranges and there were no instances in which the results of any election were swayed.
What has been seen are extensive misinformation campaigns, and efforts to cast doubt on the election’s integrity. While those do not qualify as “voter fraud” or direct tampering, it is obvious that widespread misinformation and outright fabrications have influenced some elements of the population.
What they said
With US politics more contentious than they’ve ever been, the idea of election tampering has no shortage of momentum.
The Raspberry Robin worm
What happened
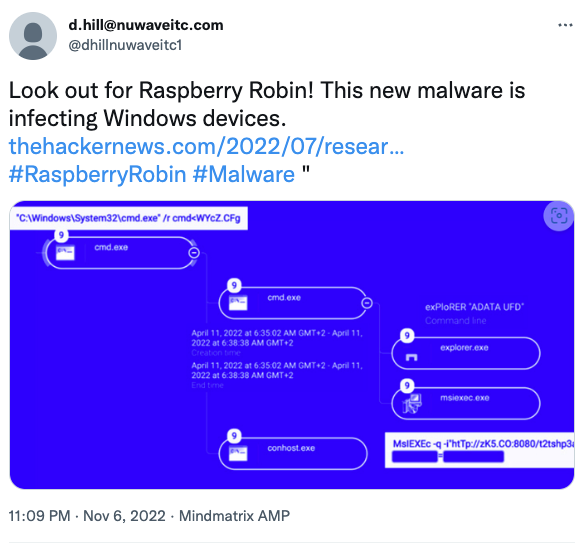
Recent research has shown that the Raspberry Robin Worm has evolved to become part of a much more complex and sophisticated malware ecosystem. The worm is still active in the wild and has shown signs of additional cybercriminal and malware activity along with it.
Why it matters
Cybercriminal organizations have evolved into complex ecosystems with specialized threat actors working together to engage with their victims, and this is certainly the case with Raspberry Robin. It doesn’t help that state-level actors are in the mix to further their own agendas by lending criminal actors’ resources or engaging in cybercriminal activities themselves either as cover, or as a way to help expand their own budgets.
This situation is not going to get better any time soon, as when it comes to this venue, crime very definitely pays and there is very little chance of getting caught.
What they said
Quickly becoming of growing concern to many, the Raspberry Robin worm is getting people talking.
___________________________________________________________________________________________________________________________
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel