It would be fair to say that the modern internet exists because the Domain Name System (DNS) has made it possible for people to easily find whatever it is they may be looking for. Over the years, everyone became familiar with the most common domains: .com, .net, .org, .edu, .gov., and the various state and national domains we know.
For many years, DNS had limited top-level domains (TLD), but that changed in 2000 with the introduction of seven new ones, then again in 2004 with the addition of even more. That all changed in 2012 when the Internet Corporation for Assigned Names and Numbers (ICANN) implemented a process where people could add arbitrary new TLDs, which is why .wtf and .ninja exist.
Now, in 2023, there are over 1500 registered top-level domains. From a business and marketing perspective, that’s a Good Thing.™ But from a cyber security perspective? Perhaps not so much.
The Wild West of TLD hacking
Some years ago, I taught a class on dealing with phishing emails and some of the techniques malicious actors were using to land their attacks. One of my colleagues added a slide where she pointed out that the Greek character Rho (ρ) looked a lot like a lower case “p” which made it great for an attacker to typosquat that particular misspelling.
Opening up the top level domains has only made things more complicated.
It’s not just that now threat actors can potentially typosquat entire TLDs, it’s that fact that the barrage of potential new domains has made it much harder for the average user to even know what they’re looking at. It’s also opened the possibility for some really confusing domain names. Like, ones that can be confused with common file extensions.
File this under controversial
For Microsoft users especially, file extensions have been “a thing” all along. You knew that a .txt extension was a text file, .doc was a document, .exe was an executable, etc. Even for operating systems that didn’t rely on extensions, there were still common naming conventions that people grew used to. They came to expect that a file with a given extension was, in fact, that kind of file.
Which is why Google letting people buy domains in the .zip and .mov TLDs are problematic.
While this isn’t the only case of overlap between domain names and file extensions – for example .com comes to mind as well, though most users only know the domain version – it’s adding a couple of domains that overlap file extensions that people are long familiar with. If you ask the average user what .com stands for, they’ll almost certainly reference the top-level domain. It’s only the technical folks who’ll mention the file extension, and only a few of them will know the origin.
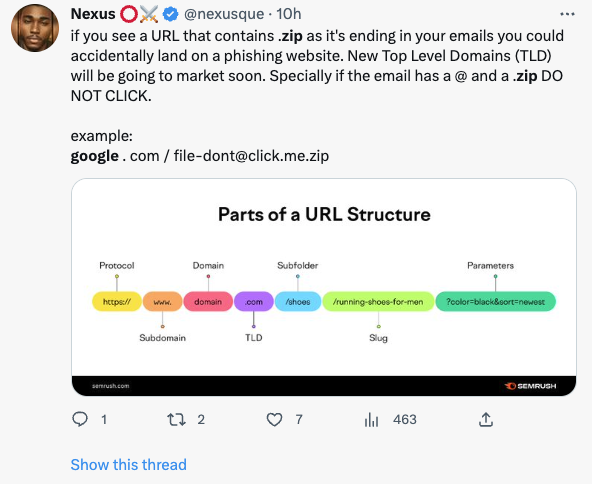
With .zip, and .mov, the first thought won’t be “that’s a website.” The first thought with .zip will be either “that’s a zip file” or “that’s a compressed archive” for people who want to be more technical. While a .mov is going to be a movie file in Apple’s format.
There are a couple of challenges with this. If people assume that a link to a .zip or .mov leads to a file they’ll download and then use normally, it becomes rather easy to trick them into following the link to a domain rather than a file. If that domain’s hosting malware? Yeah. You see where this can go.
TL;DR?
Whether this becomes widespread or not, only time will tell. But there are already reports of threat actors using the .zip TLD to host a phishing site targeting Microsoft Office users. This isn’t a theoretical issue. It’s a live one, which complicates our risk management efforts in respect to our users.
Now, combine this with Unicode naming to fool the user’s eye, and some Conversational AI to help write a convincing phishing email or other bait?
Our tools will catch up, of course, fairly quickly I’m sure. We already have tools that can filter out malicious links and DNS systems that can identify possibly hostile domains based on a range of parameters. But until those are fully in place, we have another potential threat vector we need to educate our users about, and possibly a new set of rules for our web gateways or internal DNS servers.







