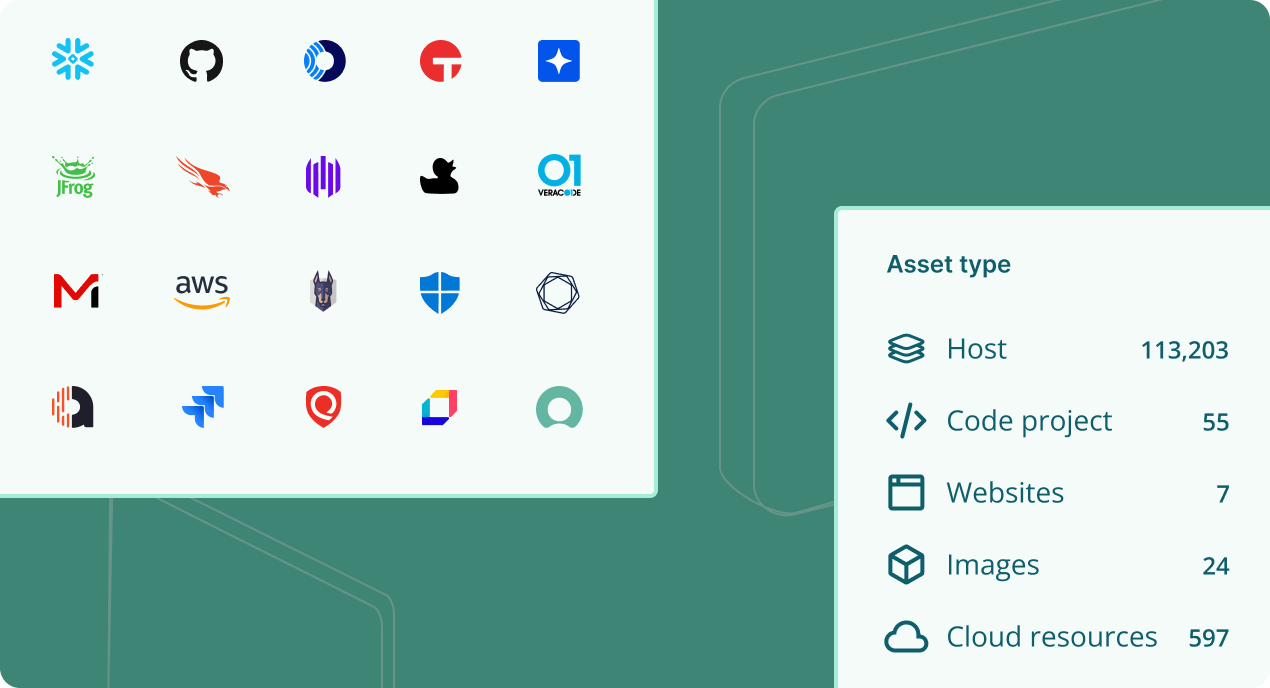
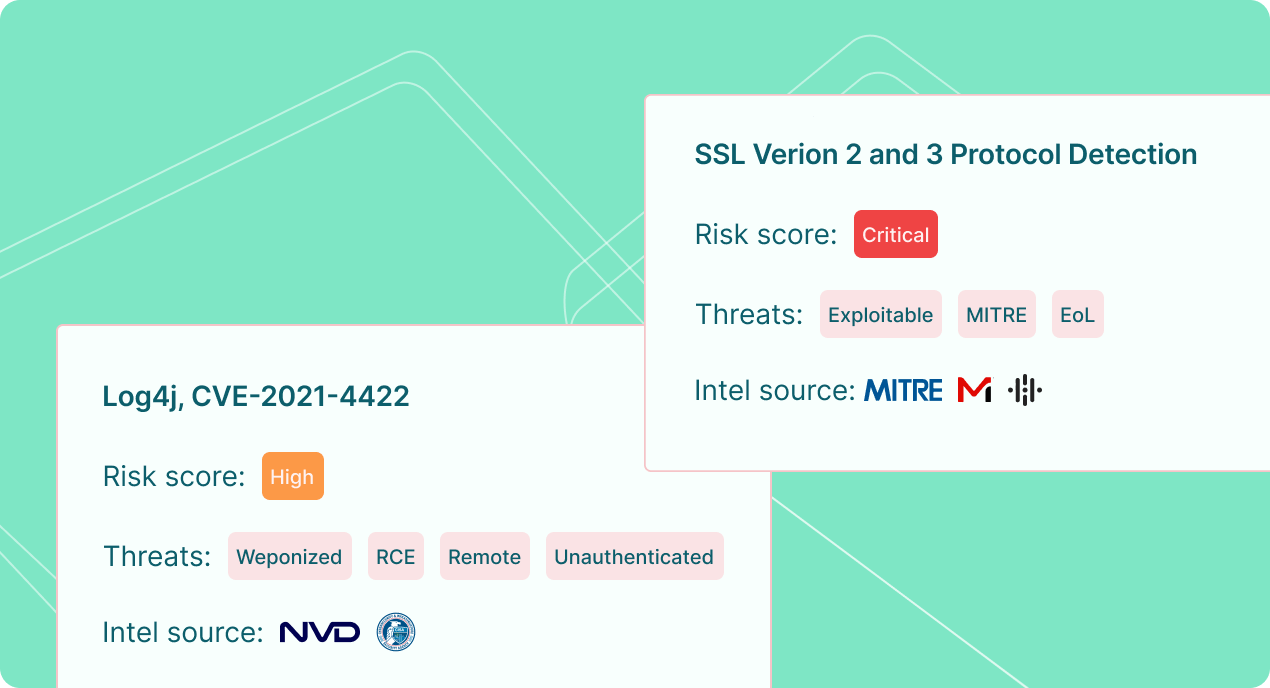
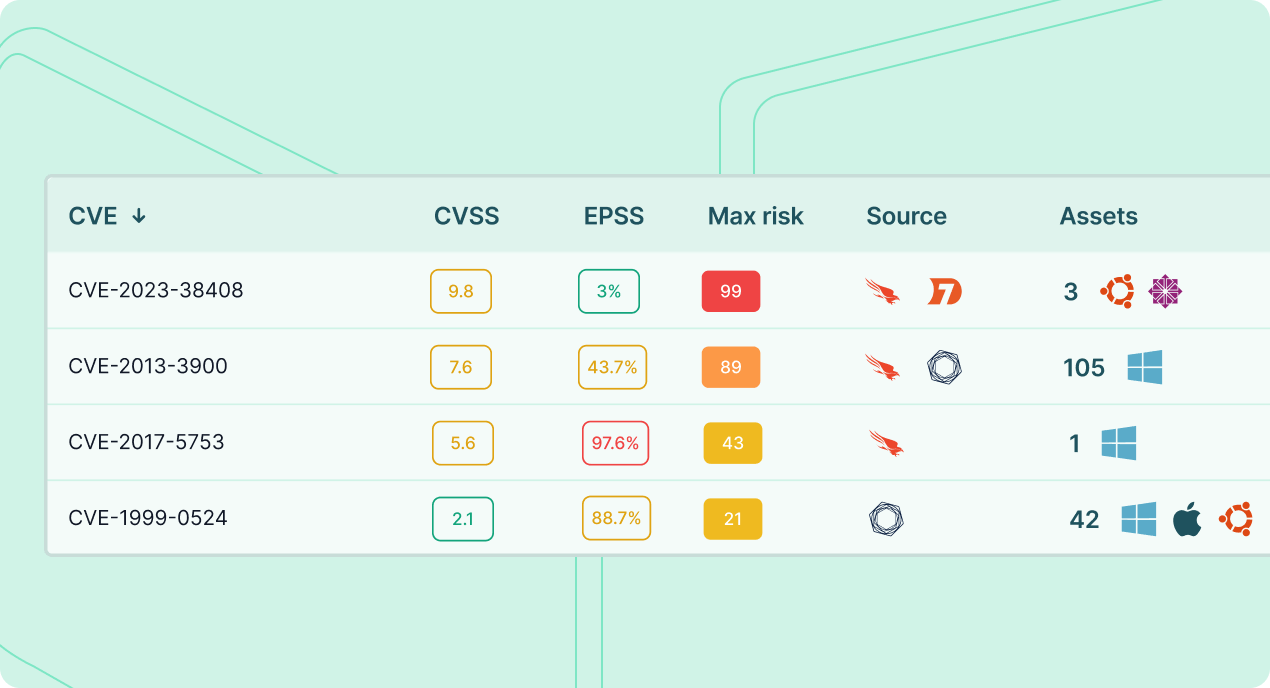
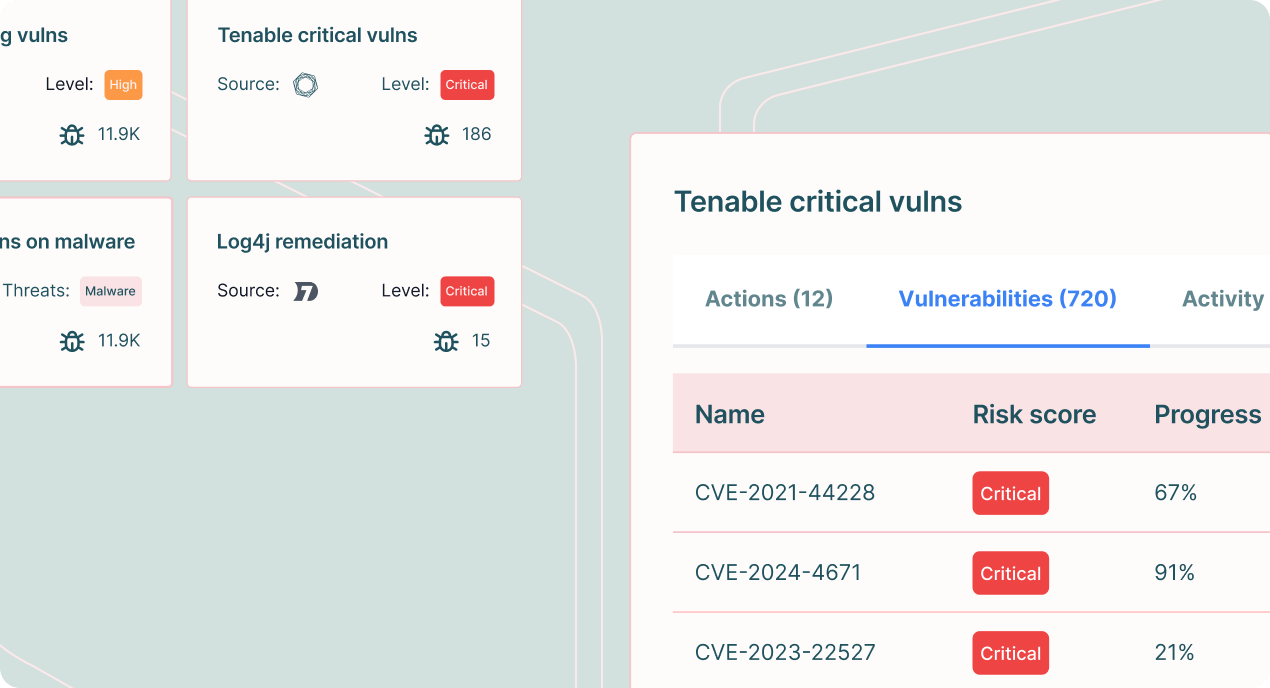
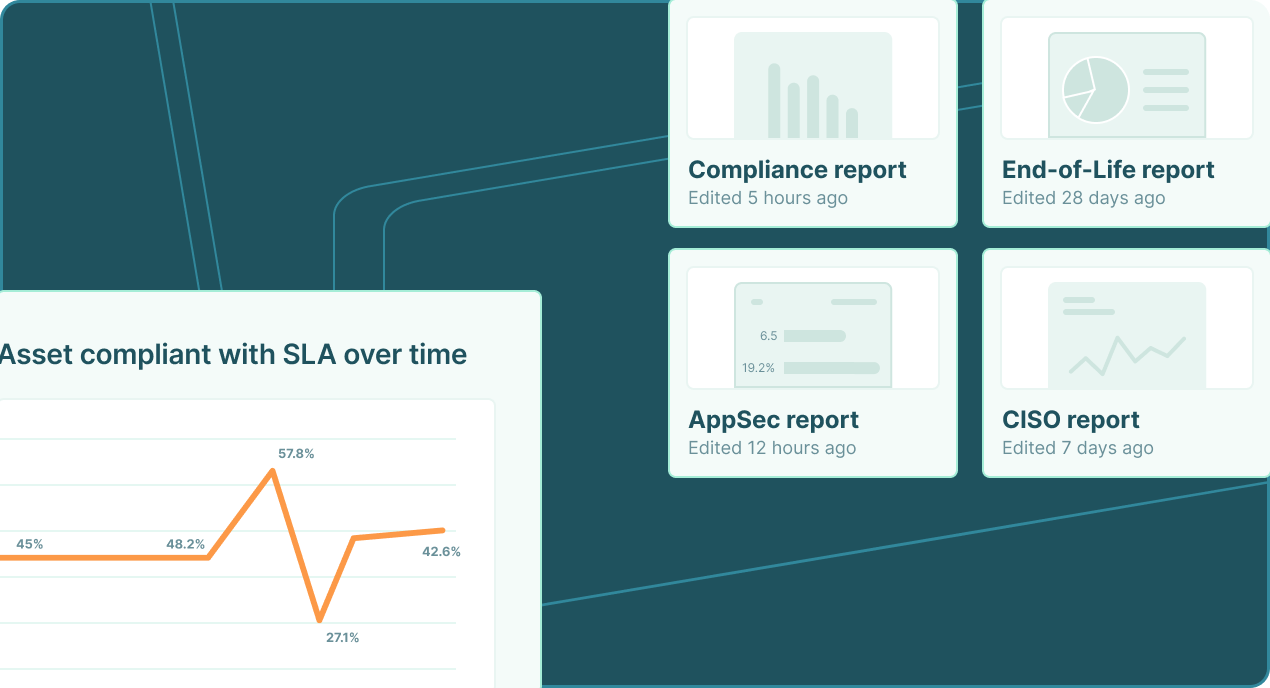
Risk-based vulnerability management
- Integrate with your network security tools including vulnerability scanners, asset data platforms and more.
- Prioritize vulnerabilities based on severity, threat intelligence, and actual business risk.
- Transform your security program into a measurable cyber risk management operation.