The Common Vulnerability Scoring System (CVSS) is a prevalent, standardized method for gauging digital systems’ severity of security vulnerabilities. Developed by the Forum of Incident Response and Security Teams (FIRST), it gives security professionals a consistent approach to assessing and prioritizing risks.
The current version, CVSS v3.0, has been operational for over a decade but has been criticized for its complexity and inflexibility. In response, FIRST has introduced CVSS v4.0, a significant revision that offers simpler, more flexible, and more accurate scoring. This version aims to mitigate previous limitations, providing a more realistic representation of risks and aiding organizations to prioritize vulnerabilities and allocate remediation resources more effectively.
As cyber threats evolve, so does the need for robust scoring systems. CVSS 4.0 is now better equipped to handle the complexities of IoT/OT/ICS environments, which are increasingly targeted by cyber attacks. This tailored approach ensures that the unique challenges of these technologies are accounted for in vulnerability assessments.
This blog will cover CVSS v4.0 in detail, elucidating its key features, improvements, and comparison with CVSS v3.0. It will also expound on the benefits and the process of adopting this new standard.
How the current CVSS scoring system works
The CVSS scoring system comprises three metric groups: base, temporal, and environmental metrics. These components play an essential role in assessing the severity of a vulnerability and its potential impact on an organization.
Base metrics
Base metrics help you understand the type of vulnerability, independent of any temporal or environmental factors. They consist of two subgroups:
- Exploitability metrics: These focus on the ease with which an attacker can exploit a vulnerability. They include Attack Vector (AV), Attack Complexity (AC), Privileges Required (PR), and User Interaction (UI).
- Impact metrics: These assess the potential consequences of a successful exploit. They include Confidentiality Impact (C), Integrity Impact (I), and Availability Impact (A).
Temporal metrics
These metrics account for factors that change over time, such as the existence of a patch or the availability of a working exploit. They include Exploit Code Maturity (E), Remediation Level (RL), and Report Confidence (RC).
Environmental metrics
These metrics allow organizations to customize the CVSS scores based on their specific environment and the potential impact on their systems. They include Modified Base metrics and Collateral Damage Potential (CDP).
Calculating the CVSS score
To calculate a CVSS score, the base, temporal, and environmental metrics are combined using a specific formula. The result is a numeric score ranging from 0 to 10, with higher scores indicating more severe vulnerabilities.
The CVSS scores are generally categorized into four severity levels:
- Low (0-3.9)
- Medium (4-6.9)
- High (7-8.9)
- Critical (9-10)
Understanding the CVSS scoring system is vital for security practitioners, as it provides a consistent method to prioritize vulnerabilities and allocate resources to address the most pressing issues. In the following sections, we will discuss the limitations and criticisms of the current CVSS version and explore the improvements and changes introduced in CVSS v4.0.
4 common problems with CVSS
Despite its widespread adoption, CVSS has faced several criticisms from security practitioners, shedding light on the need for revision. Some of the common issues associated with the current version of CVSS include:
1. Overemphasis on vulnerability exploitation
CVSS focuses on vulnerabilities’ exploitability and potential impact. This can lead to a mismatch between the theoretical severity of a vulnerability and the actual risk it poses in the real world. For instance, a vulnerability might have a high CVSS score because of its potential impact, but it may be unlikely to be exploited due to certain conditions. This mismatch can misdirect resources toward less critical vulnerabilities, inefficiently allocating valuable time and effort.
2. Inadequate representation of real-world risk
CVSS scores often lack a comprehensive view of the vulnerability context. They don’t consider crucial factors such as the asset’s value at risk or the motivations and capabilities of potential threat actors. This can lead to an under/or over-estimation of the real-world risk, skewing a vulnerability’s perceived severity and priority concerning the organization’s specific threat landscape.
3. Limited scope and lack of context
The current version of the CVSS scoring system operates within a somewhat narrow scope, primarily focusing on individual vulnerabilities. This can result in a lack of consideration for broader organizational contexts or unique environments. For example, CVSS does not typically factor in existing security controls that might mitigate a vulnerability or the potential for chained exploits where multiple vulnerabilities are used to breach a system. This lack of context can lead to an inaccurate assessment of a vulnerability’s true severity.
4. Complexity and subjectivity
Calculating CVSS scores involves numerous and complex variables. Additionally, the scores are partially subjective, as they depend on the assessor’s interpretation and understanding of the threat and its potential impact. This can make the scoring process inconsistent, leading to potential discrepancies in how vulnerabilities are ranked and prioritized across different organizations or even within the same organization over time.
Introduction to CVSS v4.0
The above-listed limitations underscore the urgent need to address the current version’s shortcomings. With this understanding, we focus on the latest revision, CVSS v4.0. This new version aims to rectify these issues, providing a more comprehensive, accurate, and contextually aware framework for assessing and prioritizing security vulnerabilities.
The development of CVSS v4.0 is complete and aims to address these concerns and improve the scoring system’s overall effectiveness.
The latest iteration of CVSS introduces a renewed focus on resiliency, particularly in the early stages of an exploit, addressing the increasing concerns around the security of operational technology (OT), industrial control systems (ICS), and the Internet of Things (IoT).
Key changes and improvements introduced in CVSS v4.0 include:
- Enhanced clarity and simplicity: CVSS v4.0 aims to provide a more streamlined scoring process, reducing subjectivity through clearer metric guidance and definitions. This update facilitates a more accurate assessment of vulnerabilities and promotes consistency across different organizations. Key to this is refining the concepts of “Attack Complexity” and “Attack Requirements,” which help elucidate the scoring process.
- Greater flexibility and adaptability: With the introduction of more detailed metrics and a modular approach, CVSS v4.0 allows organizations to tailor the scoring system to their unique needs and environments. This adaptability results in a more accurate risk representation of a vulnerability for a specific organization. The new framework includes operational technology and safety metrics, and distinguishes between active and passive user interaction—enabling a more precise vulnerability assessment in diverse contexts.
- Improved representation of real-world risk: CVSS v4.0 aims to encapsulate better the actual risk associated with a vulnerability. It achieves this by considering additional elements like the likelihood of exploitation and the potential aftermath of a successful attack. This new version emphasizes incorporating threat intelligence and environmental metrics into scoring, providing a more realistic risk assessment. This is further enhanced by the inclusion of new concepts such as “Automatable,” “Recovery,” and “Mitigation Effort,” etc., which add depth to the understanding of each vulnerability.
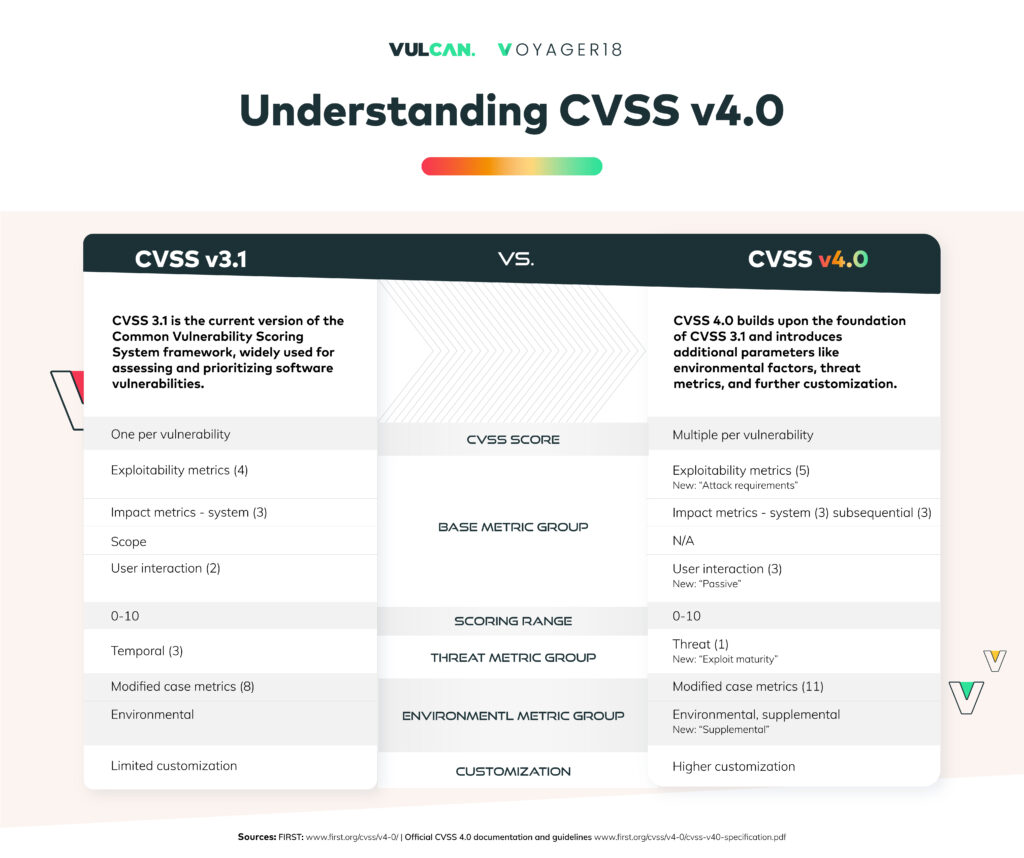
CVSS v4.0 makes significant adjustments to the framework, such as replacing the Temporal metric group with the Threat metric group and removing the Remediation Level and Report Confidence metrics. These threat metrics are both simplified and clarified; Remediation Level (RL) and Report Confidence (RC) are retired and Exploit “Code” Maturity has been renamed to Exploit Maturity (E) with clearer values. It also introduces combinations of Base (CVSS-B), Base + Threat (CVSS-BT), Base + Environmental (CVSS-BE), and Base + Threat + Environmental, CVSS-BTE, a new explicit nomenclature, and a new Supplemental metric group. These changes, among others, improve the standard’s accuracy, precision, and usability.
In addition, the New Supplemental Metric Group conveys additional extrinsic attributes of a vulnerability that do not affect the final CVSS-BTE score:
- Safety (S)
- Automatable (A)
- Recovery (R)
- Value Density (V)
- Vulnerability Response Effort (RE)
- Provider Urgency (U).
The new method also grants additional focus on OT/ICS/Safety using Consumer-assessed Safety (MSI:S, MSA:S) and provider-assessed Safety through the Safety (S) supplemental metrics
Moreover, CVSS v4.0 integrates vendor-supplied severity and impact scoring within its framework, accommodating a wider range of perspectives in vulnerability scoring. This feature improves the system’s inclusivity, aligning the scoring process more closely with real-world scenarios.
CVSS v4.0 is expected to significantly impact security practitioners, as it addresses many of the criticisms and limitations of the current version. By offering enhanced clarity, flexibility, and a more accurate representation of real-world risk, CVSS v4.0 will enable organizations to prioritize vulnerabilities better and allocate resources for remediation.
Comparison between CVSS v3.0 and v4.0
Gaining a comprehensive understanding of the contrasts between CVSS v3.0 and v4.0 is crucial for security practitioners to exploit the enhancements introduced in the latest version fully.
Key differences between the two versions include:
1. Scoring methodologies
CVSS v4.0 debuts a more sophisticated scoring methodology that aligns more closely with real-world risk. By considering a broader array of factors, including the likelihood of exploitation and the potential impact of a successful attack, CVSS v4.0 aims to offer a more holistic and accurate assessment of vulnerabilities. This refinement addresses the previous overemphasis on exploitability, resulting in a more balanced risk perspective.
2. Changes in metric groups and definitions and introducing novel concepts
CVSS v4.0 introduces updates to metric groups and definitions, ensuring clearer guidance and reducing subjectivity. For example, the Exploitability and Impact metric subgroups in the Base metrics have been revised to provide a more granular assessment of vulnerability characteristics. Furthermore, CVSS v4.0 introduces new metrics that capture additional aspects of risk, such as the potential consequences of a successful attack, including explicit assessment of impact to Vulnerable System (VC, VI, VA) and Subsequent Systems (SC, SI, SA). For instance, it replaces the Temporal metric group with the Threat metric group, eliminating the Remediation Level and Report Confidence metrics and bringing in the new Supplemental metric group.
3. How v4.0 addresses limitations of v3.0
CVSS v4.0 directly tackles many shortcomings of its predecessor by providing enhanced clarity, flexibility, and adaptability. The updated scoring system considers the broader organizational context and the specific environment in which vulnerabilities exist. By capturing the real-world risk more effectively, CVSS v4.0 enables more precise prioritization of vulnerabilities and efficient resource allocation for remediation efforts.
4. Integration of threat intelligence and environmental considerations
Emphasizing the significance of context, CVSS v4.0 mandates the inclusion of threat intelligence and environmental metrics in vulnerability scoring, again, something missing in v3.0. This way, users can understand risk in line with the organization’s specific threat environment. Introducing metrics for operational technology and safety and the differentiation between active and passive user interaction contribute to a more nuanced and realistic appraisal of vulnerabilities.
5. Accommodating vendor-supplied severity and impact scoring
CVSS v4.0 opens the door to incorporating vendor-provided severity and impact scores within the framework. Recognizing the value of diverse viewpoints, this feature enriches the scoring process and ensures a more holistic understanding of vulnerabilities. The standard also allows for vendor-created metrics that enable vendors to offer unique insights into the risk of their products or services. This inclusivity ensures a more comprehensive and practical approach to vulnerability scoring.
Alternatives to CVSS and their benefits
While CVSS is a widely adopted scoring system, other alternatives may better suit an organization’s needs.
Exploit Prediction Scoring System (EPSS)
Built upon machine learning algorithms, EPSS predicts the likelihood of a vulnerability being exploited in the wild. It considers broader factors, such as specific vulnerability attributes, threat actor behavior, and historical exploitation data—enabling a more holistic risk assessment.
Several advantages position EPSS as a strong contender to CVSS. Notably, it provides a more accurate depiction of real-world risk due to its emphasis on the likelihood of exploitation. Its capacity to prioritize vulnerabilities based on their potential impact on an organization’s unique environment enables organizations to optimize their resources effectively, addressing vulnerabilities with the highest potential for adverse impact.
Other alternatives
Apart from EPSS, other scoring systems can also be considered, depending on an organization’s requirements and objectives.
Microsoft’s DREAD model
The DREAD model is a risk-assessment methodology used to quantify, compare, and prioritize the risks of identified security vulnerabilities. An acronym for Damage potential, Reproducibility, Exploitability, Affected users, and Discoverability, this model helps organizations focus on the most significant risks by examining the following:
- Damage potential: Considers the maximum damage that could be caused if a vulnerability were exploited. This considers potential financial loss, reputational harm, or data loss that might occur.
- Reproducibility: Assesses how easy it would be for an attacker to reproduce the exploit. If the vulnerability is easily reproducible, it is more likely to be exploited, which raises the overall risk.
- Exploitability: Measures how simple it would be for an attacker to exploit the vulnerability. This could depend on the need for specialized knowledge, tools, or conditions for a successful exploit.
- Affected users: This element quantifies the portion of the system’s user base affected if the vulnerability were exploited. A higher number of affected users generally corresponds to a higher level of risk.
- Discoverability: This metric estimates how easy it would be for an attacker to discover the vulnerability. Some vulnerabilities may be hidden or require in-depth knowledge, while others may be more apparent.
The DREAD model helps organizations to focus on the most significant risks by examining the potential damage, the ease of exploiting the vulnerabilities, the impact on the user base, and the likelihood of an attacker discovering the vulnerability. This information is instrumental in formulating a risk response plan and deciding which vulnerabilities to address first based on their DREAD scores.
OWASP’s Risk Rating Methodology
The Open Web Application Security Project (OWASP) offers a risk rating methodology emphasizing web application security. It helps organizations identify, assess, and prioritize security risks in web applications. This methodology considers threat agent factors, vulnerability factors, impact metrics, and the likelihood of an attack. OWASP’s approach is highly customizable, allowing organizations to adjust the factors according to their specific operational environment and risk tolerance.
NIST’s Common Misuse Scoring System (CMSS)
The CMSS, developed by the National Institute of Standards and Technology (NIST), focuses on the misuse and abuse of software vulnerabilities. Unlike other models, it offers a more comprehensive analysis by considering the operational conditions that affect a misuse case, such as the level of access required and the potential impact on an organization’s operations and assets. This makes CMSS a valuable tool for organizations that want to take a broader view of their security posture, considering the vulnerabilities and how they could be misused.
MITRE ATT&CK
Also, we’d be remiss not to mention that while CVSS provides a standard measure for assessing vulnerability severity, the MITRE ATT&CK framework offers a detailed view of the tactics, techniques, and procedures (TTPs) that threat actors use to exploit these vulnerabilities.
By integrating CVSS scores with the ATT&CK framework, security practitioners can gain a more holistic understanding of vulnerabilities and the potential attack paths that could be used to exploit them. This integration can help identify the vulnerabilities most likely to be exploited based on the observed behaviors of threat actors and prioritize remediation efforts accordingly. Moreover, it provides valuable context informing proactive security measures, such as threat hunting and incident response planning, enhancing an organization’s overall cyber security posture.
Choosing a scoring system
Each of these scoring systems has its unique advantages and use cases. The goal is to find a scoring system with the most relevant and actionable insights for effective vulnerability management.
Security practitioners should evaluate various factors when selecting a scoring system. This includes the system’s ability to accurately mirror real-world risk, its adaptability to the organization’s specific context, the clarity of its methodology, and its compatibility with existing operational workflows and tools. The choice of a scoring system should align with the organization’s risk posture, cyber security strategy, and overall business objectives, ensuring the system serves as a tool that enhances—rather than hinders—effective vulnerability management.
The bottom line
CVSS v4.0 offers significant improvements over its predecessor, addressing many of the criticisms and limitations associated with CVSS v3.0. By providing enhanced clarity, flexibility, and a more accurate representation of real-world risk, CVSS v4.0 enables security practitioners to prioritize vulnerabilities better and allocate resources for remediation.
While CVSS is a widely adopted scoring system, organizations must evaluate alternative options like EPSS and consider accuracy, adaptability, and compatibility with their unique needs and environments. The right scoring system can significantly impact an organization’s ability to manage vulnerabilities and maintain a robust security posture effectively.
Security practitioners should stay informed about the latest developments in CVSS v4.0 and be prepared to embrace the new features and improvements, as this will be crucial to their continued success in identifying, assessing, and addressing the latest vulnerabilities in an ever-evolving threat landscape.
Prioritize vulnerabilities within critical business context. Vulcan Cyber® offers custom risk parameters and enhanced vulnerability prioritization scores weighted with business asset data. Plus, it integrates with your existing tool stack for better collaboration and faster remediation at scale. Schedule a live demo today.








