Vulnerability and risk data must be comprehensive, visible, and actionable in order to drive security improvements within your organization. However, with teams using disparate tools and platforms, it can be challenging to consolidate scan results and consistently interpret this data. As a result, threats are frequently forgotten, duplicated, outdated, or difficult to remediate—preventing you from properly protecting your asset inventory.
Addressing this problem requires a cohesive risk management solution like Vulcan Cyber that provides a holistic view of your threat landscape and integrates with your existing toolset and data providers. Moreover, data about affected assets (e.g., cloud accounts and code risks) should flow directly to a centralized dashboard, where you can track each issue and apply resolutions.
The challenges of managing vulnerability data
Vulnerability management is about more than just listing the threats you face. Most teams have multiple applications, source repositories, and cloud providers—all of which need to be continually scanned for threats. A vulnerability in any of these assets—such as an AWS account, GitHub repository, or outdated dependency—could give threat actors enough leverage to execute a successful attack.
Multiple security toolchains
Once a risk has been identified, it needs to pass through a security toolchain that validates the threat, assigns it a priority, and notifies relevant stakeholders for remediation. This step is crucial because it filters out detected threats that aren’t immediately actionable or relevant. You only need the data that will actually prompt a response; everything else is noise that makes it harder for security teams to identify what matters.
But organizations frequently rely on many different tools to implement this process, with individual teams, apps, and vulnerability types each using an independent solution. For example, some products might use Rapid7 for vulnerability assessment; in other cases, detection could be driven by Mandiant threat intelligence pipelines.
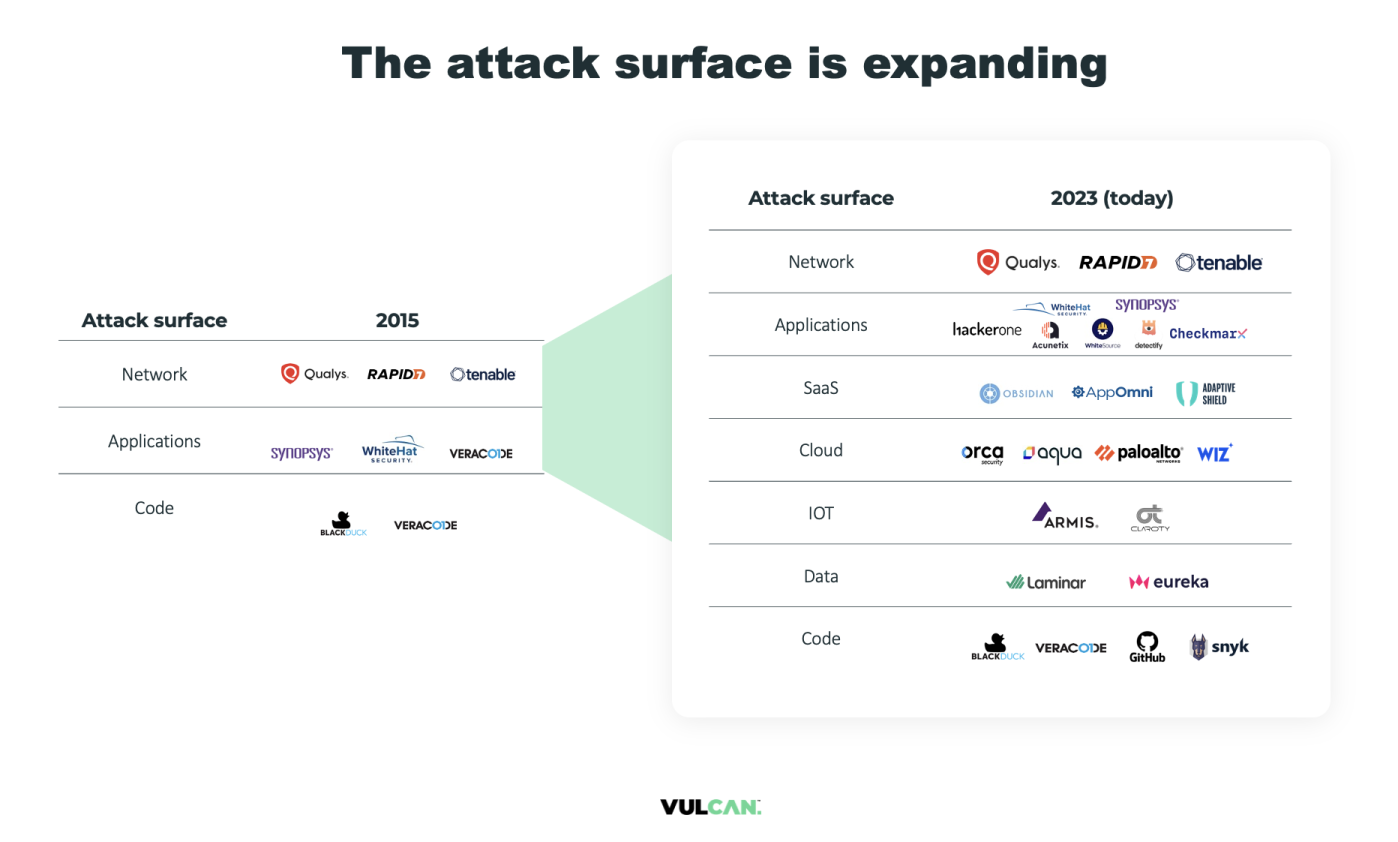
Lack of visibility into your threat landscape
After threats have been validated, teams can still struggle to keep tabs on them. You need to know which threats require action, which have been remediated, and which are no longer relevant in order to coordinate an effective security response.
But this data is often missing from scan results, as most tools focus on point-in-time coverage, without the ability to monitor identified threats or know when they’ve been resolved. As a result, teams end up having to use manual methods to import threat data into existing ticketing tools like GitHub Projects and JIRA.
Lack of threat consolidation due to poorly defined processes
Poorly defined vulnerability management processes make it harder to implement consolidated visibility and remediation workflows. Constant changes in tools, infrastructure, and security team personnel make it difficult to achieve consistency. And you can end up spending more time orchestrating the tools than the threats they’re supposed to be managing.
The use of multiple scanners also means threats can easily be duplicated when they’re detected by different tools or in several independent environments. This makes it harder to determine the extent to which you’re affected by each unique risk. Well-formed vulnerability data should therefore include links to the specific asset inventory items each threat has been found in.
How vulnerability data should work
But vulnerability data management doesn’t have to be difficult. Risk management platforms like Vulcan Cyber give you a consolidated view of the data that spans your entire asset inventory. You can see all the threats you face, track their status, and coordinate responses through a single solution—giving you the right data, in the right place.
1. Consolidate all data
Successfully managing your vulnerability data starts with the ability to collate results from all your scan tools and environments.
Threat data can be sourced from a variety of different endpoints—cloud provider APIs, source code analysis (SCA) tools, dynamic and static application security tests (DAST/SAST), and scans of infrastructure as code (IaC) provisioning files. Ensuring coverage of each asset type requires different tools. Because of this, most teams require multiple scanners to audit all the assets they own.
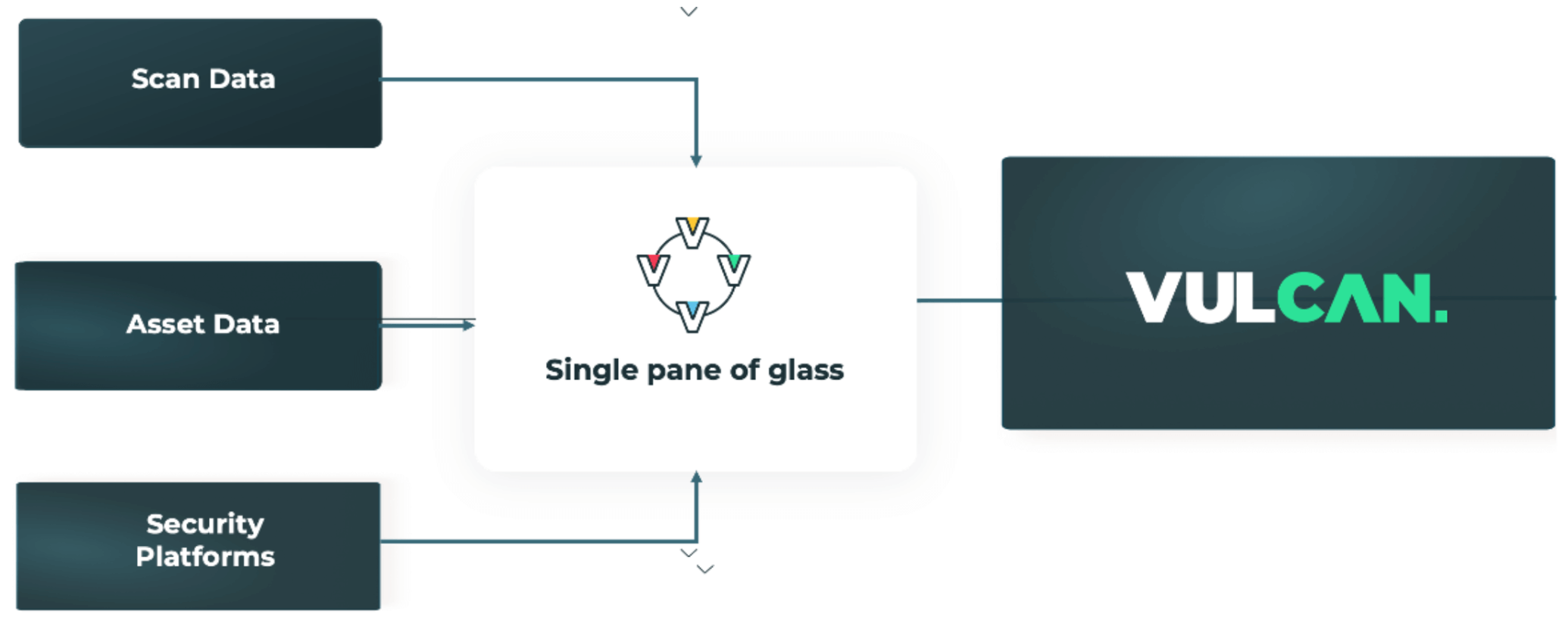
A cohesive cyber risk management strategy requires the data from these scanners to be unified so that you can identify recurring risks across your asset library. Vulcan Cyber supports dozens of direct data integrations, enabling you to connect and aggregate all your sources—from Microsoft Defender and Orca Security for cloud to Snyk and Sonatype for threats in your codebase.
2. Assess detected threats
Next, the scan results you have collated must be triaged and prioritized. Here, you determine whether each risk is relevant and then determine how it should be resolved, such as by searching for automated mitigations.
In this stage, you should also incorporate data from dedicated vulnerability assessment tools in this stage. These insights need to be directly visible in your cyber risk solution alongside each detected threat in order to ensure vital contextual information is available to support remediation efforts. Vulcan integrates with multiple threat intelligence and assessment tools so you can orchestrate insights from all your providers.
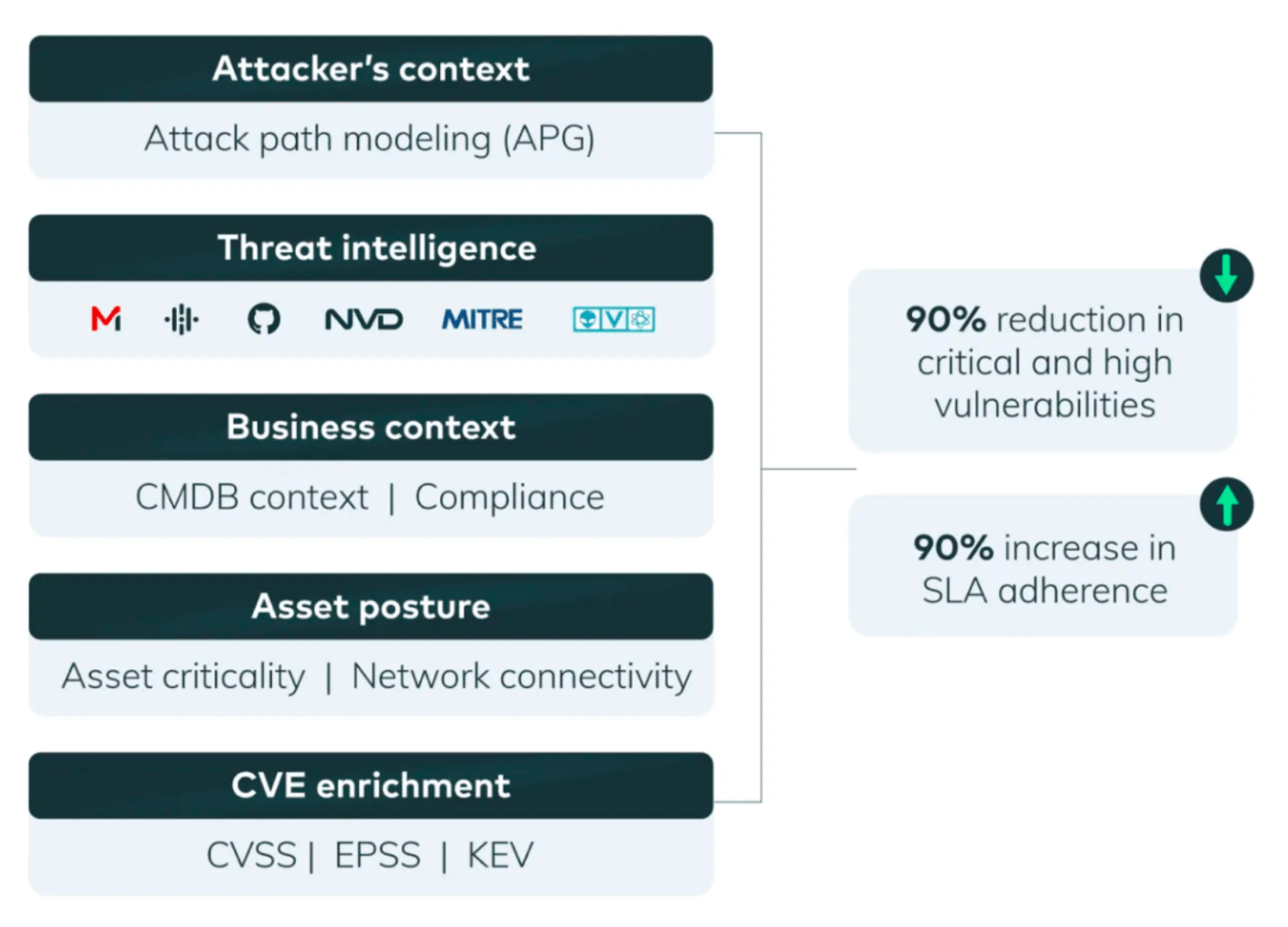
The Vulcan Cyber method for comprehensive vulnerability prioritization
3. Track verified threats
Verified threats should be added to a ticketing system so that all stakeholders see the status of the threat. Once a ticket has been created, you can launch the remediation process by assigning relevant team members and logging comments as more information becomes known.
Creating tickets for risks also expands access to non-security team members. Developers, business teams, and customers won’t necessarily have access to your risk management solution, for example, but may still need to track updates on detected threats.
Vulcan supports integrations with ticketing tools including JIRA and ServiceNow. You can automatically open JIRA issues for new vulnerabilities, then use JIRA to address those threats. Similarly, the ServiceNow integration lets you add threat resolution steps to your existing IT workflows, enabling consistent responses that meet your compliance requirements while retaining Vulcan as the source of truth for your overall security posture.
4. Provide actionable alerts and resolutions
Detected risks must be easily actionable. Merely having visibility into vulnerability data isn’t useful, because those vulnerabilities need to be quickly resolved to mitigate the risk for your products and customers.
Hence, your cyber risk platform should support integrations with the collaboration, chat, and development tools that your teams are already using. This final data flow ensures users don’t have to go hunting for threat data.
Vulcan Cyber offers real-time alerts for new vulnerabilities and remediation tasks within Slack and Microsoft Teams. Relevant stakeholders can easily access data about new risks as they appear, shortening the time to resolution.
The benefits of managing cyber risk data through a unified platform
Unlike traditional approaches to risk data management—which require multiple tools, user accounts, and remediation processes for every application and service—Vulcan Cyber offers a unified solution that lets you easily detect, triage, track, and respond to threats, all while scaling with you as your asset inventory grows.

Vulcan streamlines vulnerability data management, empowering security teams by offering:
- Complete coverage: Vulnerabilities are collated across all your data sources and attack surfaces—from cloud, infrastructure, and network endpoints to insecure source code and misconfigurations.
- Full visibility: All threats are consolidated, giving you a comprehensive view of your threat landscape and overall security posture.
- Greater consistency: Every threat can be dealt with in the same way, regardless of where it appears or what type of vulnerability it is. This enables more standardization of tools and workflows, in turn streamlining incident response.
- Faster remediation: Your team members are notified of new issues where they are working. All relevant threat information is available within the platform, allowing for faster time to resolution.
- Break down knowledge silos: Threat data is no longer siloed into specific tools or teams. Instead, your security team members can easily access the entire threat catalog for informed risk assessment. Data can be readily distributed to other teams within your organization (e.g. product and business) simply by sharing access to the platform.
Make sense of cyber risk data with Vulcan Cyber
Without a centralized platform, managing cyber risk data—consolidating information from all your analysis tools, tracking the state of each threat, and ensuring swift remediation—can be a real burden for security teams.
The Vulcan Cyber risk management platform gives you deep visibility into threats across your entire attack surface. Vulcan connects to your existing cloud infrastructure and vulnerability management toolstack, with a catalog of over 100 integrations. The built-in connectors cover asset inventory, endpoint security, threat intelligence, cloud, deployment, and application security services. With Vulcan ConnectX, you can also supply your own data from CSVs and spreadsheets.
Once you’ve set up your data connections, you’ll be able to view all your assets and associated risks within the platform to consolidate your security actions and processes in one place. You can correlate vulnerabilities across projects and groups, deduplicate data, and enhance visibility. Automated rule-based strategies, which you can coordinate across teams from your existing collaboration platforms, allow you to prioritize and mitigate relevant risks.
By fully utilizing your vulnerability data, you get improved visibility, greater consistency, and less overhead throughout the security response process.
Start owning vulnerability risk management with Vulcan Cyber by getting your free demo.








