UPDATE: As of 11th March 2024, CISA has confirmed breaches of its systems through Ivanti products. Read more >>
CISA has issued emergency directives to fix two significant vulnerabilities in Ivanti products: CVE-2023-46805 and CVE-2024-21887. These vulnerabilities present critical challenges to network security and have sparked concerns across various sectors.
But as the cyber security industry started to address these issues, two new vulnerabilities were discovered, prompting CISA to issue a further directive to disconnect vulnerable Ivanti products as soon as possible.
Here’s what you need to know:
What are Ivanti’s critical CVEs?
CVE-2023-46805 is a high-severity vulnerability that allows authentication bypass, posing a significant threat to network security. CVE-2024-21887, with its critical severity, enables command injection. Both these vulnerabilities impact Ivanti Connect Secure and Ivanti Policy Secure gateways and are a major concern for users of these products.
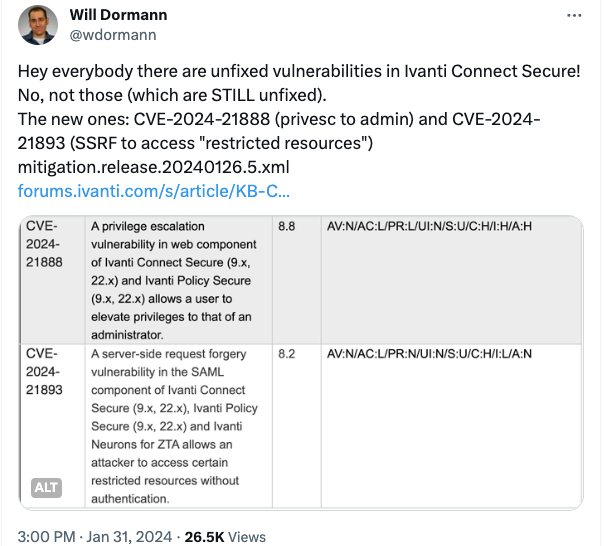
To make matters worse, two new vulnerabilities were found in addition to the above. CVE-2024-21888 is a privilege escalation vulnerability in the web components of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) that allows an attacker to gain administrator-level privileges.
Meanwhile, CVE-2024-21893 a server-side request forgery vulnerability within the SAML component of Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x), and Ivanti Neurons for ZTA, enabling access specific restricted resources without authentication.
Do they affect me?
If you utilize Ivanti Connect Secure or Ivanti Policy Secure in your organization, the vulnerabilities CVE-2023-46805, CVE-2024-21887, CVE-2024-21888 and CVE-2024-21893 could be a concern for you. These vulnerabilities can impact a broad range of sectors due to the widespread use of Ivanti products. It’s crucial to assess whether your systems could be at risk and to understand the implications of these vulnerabilities on your network’s security.
Have Ivanti’s CVEs been actively exploited in the wild?
There have been reports of active exploitation of these vulnerabilities. Attackers have leveraged CVE-2023-46805 and CVE-2024-21887 in various ways, posing a significant threat to organizations that use the affected Ivanti products. The scope and impact of these exploits underline the urgency for immediate and proactive security measures.
Fixing the CVEs
To address these vulnerabilities, it’s crucial to apply the patches provided by Ivanti promptly. Organizations should also review and update their security protocols, including regular security audits and network monitoring, to prevent potential exploits. Staying vigilant and informed about the latest security updates is key to maintaining network integrity.
Next steps
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:








