Over the weekend, the security industry faced two critical zero-days for Apple products. Both CVE-2022-32893 and CVE-2022-32894 could potentially lead to remote code execution on Apple devices and should be urgently addressed.
Let’s explore what we know so far, and the steps you should follow to mitigate the risk.
What are CVE-2022-32893 and CVE-2022-32894?
The two vulnerabilities are CVE-2022-32893 and CVE-2022-32894. There aren’t so many details yet except what Apple provided in their official advisories.
CVE-2022-32893 is a zero-day OOB write vulnerability in WebKit, which is the web browser engine used by Safari and other iOS and MacOS apps.
This CVE can be triggered and leads to arbitrary code execution by the processing of crafted web content.
CVE-2022-32894 is a kernel vulnerability that also arose from an out-of-bound bug write, and which could allow an application to execute an arbitrary piece of code with kernel privileges.
Both vulnerabilities were reported by anonymous researchers.
Do CVE-2022-32893 and CVE-2022-32894 affect me?
The affected products can be found in the security advisories from Apple.
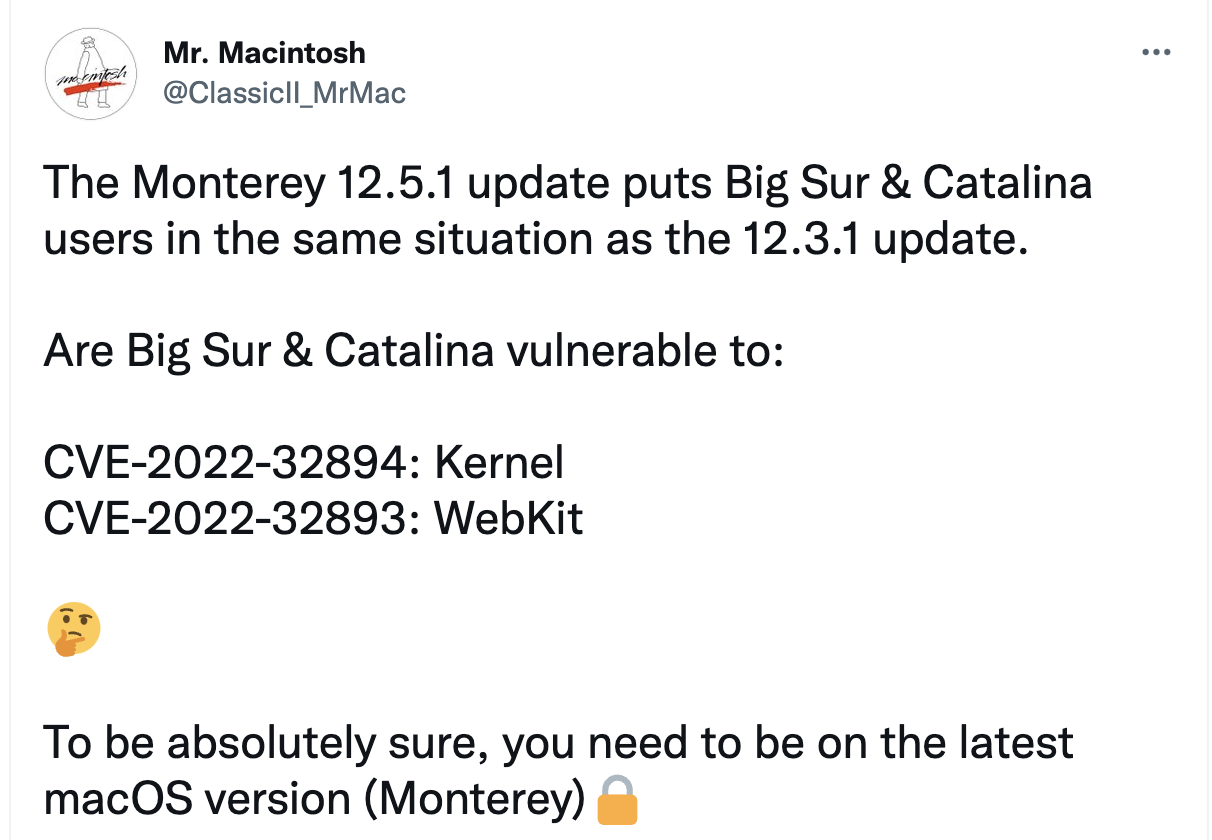
CVE-2022-32893 affects WebKits on almost all Apple products, and two updates were published. One for MacOS (Monterey, Big Sur and Catalina), and the second for iOS / iPadOS 15.6.1.
Although Apple did not confirm it, iOS/iPadOS version 14 probably won’t be supported with security updates anymore, so it’s highly recommended to update to version 15 in general.
CVE-2022-32894 affects the same products, with an interesting exception. A patch for this vulnerability wasn’t enrolled for MacOS Big Sur and Catalina like it was enrolled for Monterey. It is unclear whether those OS versions are not affected by the CVE, or aif n update has simply not been published yet.
Have they actively exploited in the wild?
There are no concrete reports of victims, but if Apple and CISA themselves say there have been exploits, then there’s some cause for concern.
At first, Apple said that they were “aware of a report that this issue may have been actively exploited.”
But, a day later, CISA added the two CVEs to their known exploited vulnerabilties catalog.
Fixing CVE-2022-32893 and CVE-2022-32894
As mentioned, it is essential that users install the latest patches, and that version 14 users update to version 15 as soon as possible.
Next steps
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:
- The most common CVEs (and how to fix them)
- Apple vulnerability trends
- Mapping CVEs to the MITRE ATT&CK Framework
- The Vulcan Cyber community Slack channel
- Vulcan Remedy Cloud
And finally…
Don’t get found out by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your threat environment and lets you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.