A growing number of organizations are adopting multi-cloud strategies to optimize IT infrastructure, reduce costs, and increase efficiency. As companies move workloads and applications to multiple cloud providers, securing these environments becomes a critical priority. Adopting a multi-cloud strategy presents unique challenges and security risks when it comes to protecting an organization’s data, applications, and infrastructure across different cloud environments (including public, private, and hybrid clouds). Organizations must navigate the complexities of managing and securing data across different cloud providers, each with its own policies, standards, and technologies.
Key stat: Statista reports that 86% of companies encounter difficulties in handling data across multi-cloud settings.
In this article, we explore technical considerations and best practices to mitigate these security risks and help ensure the safety of your organization’s valuable data and resources.
Multi-cloud security challenges
Despite the many advantages multi-cloud offers, working in interoperable, diversified environments has its drawbacks:
- Requires individuals skilled in managing multi-cloud environments.
- Integrating multiple cross-platforms can be challenging, even with the help of APIs, since cloud vendors employ different technologies in order to gain a competitive advantage.
- Expanded attack surface as a result of integration of multiple cloud vendors into the environment, making it more difficult to manage and secure the environment.
- Latencies due to data transfers between cross platforms could lead to performance and reliability issues—availability is a key element of security.
There is a misconception that adopting cloud transfers the security responsibilities to the cloud provider. This, however, is not the case. Depending on the cloud service model, the shared responsibilities change. Even if you use IaaS, SaaS, or PaaS, your organization will be fully responsible for your data, accounts, and access management. Thus, responsibility cannot be transferred to the cloud provider completely, and multi-cloud strategies will not reduce the security responsibilities associated with certain cloud components.
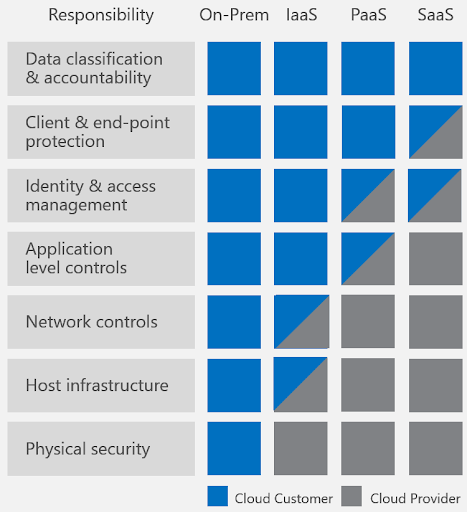
Figure 1: Microsoft cloud shared responsibilities: Vendor vs. customer (Source: Microsoft)
Multi-cloud security best practices
Identity access management
Identity access management (IAM)—a crucial part of multi-cloud security—encompasses the policies, processes, and technologies that help organizations manage, authenticate, and authorize access to their cloud resources. In a multi-cloud environment, understanding how each cloud provider implements IAM is essential for determining the right security approach for your organization.
In a multi-cloud environment, IAM involves the management of user identities, roles, and permissions across different cloud platforms. Every cloud provider has its own IAM system and specific implementation, which may include unique features or security measures. This can make creating a consistent and secure access control policy across multiple cloud environments challenging. Creating granular IAM policies for each cloud provider will help enforce least privilege.
By implementing the following best practices, you can establish a robust and consistent IAM framework that mitigates the risks of managing access to resources in a multi-cloud environment:
Leverage single sign-on (SSO)
SSO creates a streamlined authentication process, granting users access to multiple cloud services with a single set of credentials. Implementing SSO across all cloud environments simplifies user authentication and reduces the chances of unauthorized access due to compromised credentials. By consolidating multiple authentication processes into one secure system, SSO not only enhances the user experience, but also streamlines identity management and minimizes potential attack vectors for cyber criminals.
Add multi-factor authentication (MFA)
Gain an additional layer of security by requiring users to provide multiple forms of identification before granting access to cloud resources. Implementing MFA across all cloud environments strengthens security by adding extra layers of protection, making it more challenging for unauthorized users to gain access, even if they possess valid login information.
Complete regular reviews and audits
It’s a good idea to continuously monitor and review IAM policies and user activities across all cloud providers. Conducting periodic audits to identify and remediate any inconsistencies, outdated permissions, or potential security risks helps you maintain the same level of security across cloud environments.
Data security
Multi-cloud environments can add complexity and broaden the attack surface. When data is stored and processed across various cloud providers, it becomes more challenging to maintain consistent security policies, monitor access, and implement proper encryption. Following best practices for securing sensitive data across multiple cloud environments is therefore key. This should include:
Using data loss prevention (DLP) tools
Identify, monitor, and protect sensitive data across your multi-cloud environment with DLP solutions. Tools like Symantec DLP, McAfee Total Protection for Data Loss Prevention, and Forcepoint DLP can help prevent data leakage, enforce data handling policies, and provide visibility into data usage.
Considering your encryption types
Make sure that all cloud providers support your chosen encryption standards and your encryption keys are secure. Industry-standard encryption protocols (e.g., AES or RSA) are recommended for data in transit and at rest.
Reviewing and auditing data access policies regularly
Emphasize data access governance across all cloud providers by consistently examining and updating data access policies and user activities. Perform regular audits to detect and address any discrepancies, obsolete access permissions, or possible security threats related to data access and usage.
Following these best practices will help secure sensitive data in multi-cloud environments and minimize the risk of breaches or unauthorized access. Data security should be a top priority for organizations adopting a multi-cloud strategy in order to maintain a solid security posture.
Compliance and governance
Failure to comply with GDPR, HIPAA, and PCI DSS regulations can result in serious consequences.
Implementing the best practices listed below will help your organization avoid costly fines and the legal ramifications of compliance violations:
Implement policies and procedures
These policies should cover data handling, storage, processing guidelines, as well as the specific compliance requirements for each cloud provider.
Ensure CSPs adhere to security and compliance standards
Select cloud providers that comply with your organization’s regulatory standards. Conduct due diligence and assess each provider’s security measures and certifications to be certain they meet your compliance needs.
Prioritize visibility
Implement continuous monitoring solutions to detect potential security breaches or non-compliance issues in real time and to allow for visibility into your multi-cloud environment. These tools can help identify unauthorized access, configuration changes, or other activities that could jeopardize compliance or security.
Avoid misconfiguration
Proactively troubleshooting and identifying misconfigurations across your environments will help to reduce the attack surface and maintain a robust multi-cloud security posture.
Compliance and governance are essential aspects of multi-cloud security and are key to protecting your data, reputation, and bottom line.
Business continuity and disaster recovery
Business continuity and disaster recovery (BCDR) planning helps organizations minimize downtime and ensure the availability of services during unexpected events. But the added complexity of multi-cloud environments makes BCDR more challenging, as organizations must account for different cloud providers and their respective backup and recovery solutions. A well-thought-out disaster recovery strategy makes sure operations can be quickly restored in case of a disaster, while a comprehensive business continuity plan guarantees critical services remain available during a disruption.
To maximize uptime and ensure reliability, follow these best practices for BCDR planning across multiple cloud environments:
Diversify your backup strategy
Store backups across multiple cloud providers to minimize the risk of data loss due to provider-specific issues. This approach enables your organization to access its data from another provider, even if one cloud provider experiences an outage or failure.
Employ consistent backup policies
Keep uniform policies across all cloud providers to make sure data is regularly backed up and can be quickly restored during a disaster. Policies should include backup frequency, retention periods, and encryption guidelines.
Regularly test your backup and recovery solutions
Testing is the only way to be sure your solutions work across all cloud providers. Testing regimens should include simulating disaster scenarios in order to verify that your organization can recover data and resume operations.
These best practices will help you remain resilient in the face of unexpected events. Early planning for BCDR protects valuable data and ensures critical services remain available.
Network security
Network security is essential to multi-cloud security, as it helps protect your organization’s data and resources from unauthorized access and potential threats. These are widely accepted best practices to protect networks in a multi-cloud landscape:
Network segmentation
This involves dividing your network into smaller, isolated segments that limit unauthorized access and reduce the impact of a potential breach. Implement network segmentation and access control policies across all cloud providers so that only authorized users and devices can access your multi-cloud resources.
Monitor and manage network traffic
Network monitoring tools and intrusion detection systems (IDS) give you insight into your multi-cloud environment and help identify any suspicious activity or unauthorized access attempts.
Secure the network connections between your cloud providers
Use industry-standard encryption protocols (e.g., TLS and IPsec VPN) so that data being transmitted between cloud environments remains protected and can only be accessed by authorized users.
Network security is a crucial aspect of multi-cloud security, and it must be prioritized in order to protect your organization’s data and resources from potential threats and to maintain a strong overall security posture.
Mastering multi-cloud security
Emphasizing multi-cloud security is essential to the safety and success of your operations. By implementing best practices in key areas, such as identity and access management, data security, compliance and governance, BCDR, and network security, you can develop a robust security posture that spans across multi-cloud environments, safeguarding critical data and resources from potential threats.
Vulcan Cyber® offers a comprehensive solution for managing and addressing emerging vulnerabilities in your cloud environment, helping you navigate the complex multi-cloud security landscape with confidence. Book a demo today.
FAQs
What is an example of multi-cloud?
Multicloud computing involves employing various public cloud services from distinct providers simultaneously within a single architecture. For example, a company could utilize AWS for storing data, Google Cloud Platform for development and testing purposes, and Microsoft Azure for disaster recovery strategies.
What is the downside of multi-cloud?
Managing a multi-cloud environment can become complex owing to challenges like managing multiple vendors, inconsistencies in cloud computing, inefficiencies, and duplicative tasks. Additionally, transferring data across various cloud providers can introduce cost increases and performance slowdowns.
Is security more difficult in a multi-cloud environment?
Ensuring security in a multi-cloud environment demands meticulous planning and the use of suitable tools. The complexity inherent in multi-cloud setups can broaden the potential attack surface and elevate the risk of cyberattacks, thereby introducing a range of security challenges.









