There’s a lot to talk about in the world of vulnerability management these days. The crush of vulnerabilities isn’t slowing, and the bad actors are becoming even more brazen in their attempts to hack and steal. After the recent SunBurst hack, just about everybody in cyber security and IT operations is asking the question, “How do I protect my business from the Russian cyber attack?”
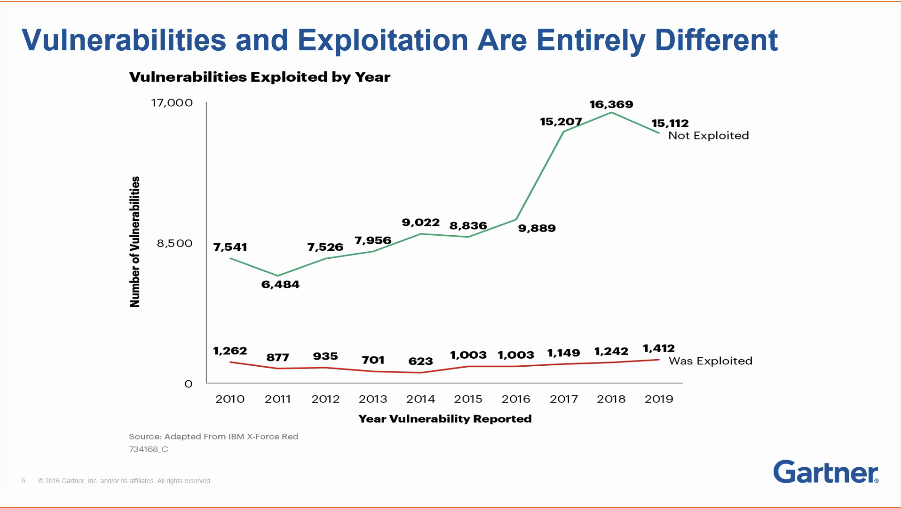
The answer isn’t easy, especially if your teams haven’t kept on top of cyber hygiene and vulnerability remediation best practices. But the good news is there are more known vulnerabilities that have not been exploited, than vulnerabilities that have been, as this data from IBM and Gartner suggests:
But to have your organization be a green-line statistic, instead of a red-line statistic, takes work and a certain level of maturity across both cyber security and IT operations organizations and processes.
I had a great conversation with Mitchell Schneider, Gartner principal analyst, this morning on the topic of vulnerability remediation maturity. Bottom line, despite the recent headlines we are getting better at getting fix done but there is always more work to do. Some shared observations, all of which can be applied to defending against the Russian cyber attack, but are bigger than just this one incident:
- CIOs and CISOs are sharing the burden of cyber hygiene and understand the importance. CFOs expect the security and IT organizations to secure digital business and to combine forces in the effort.
- Business and IT executives need insight into the success of cyber security initiatives which requires a common, shared data set and metrics that measure remediation campaign outcomes.
- Common bridges between security and IT must continue to be built. Effective remediation doesn’t get done without one team or the other. These bridges can be based on shared asset data or a common governance program.
- Risk-based vulnerability management, that includes vulnerability prioritization and asset context, should drive the work of remediation. The question then becomes not if we fix a certain vulnerability, but when. IT operations teams don’t have time to be sent on a wild fix chase by irrelevant vulnerability reports.
- Team success through collaboration must be documented and demonstrated through proof that vulnerabilities have been fixed and risk to the business has been reduced.
Vulcan Cyber recently made Remedy Cloud available to help get fix done collaboratively. Remedy Cloud, a free, searchable library of CVE remedies, helps your security team provide the best, curated fixes with prioritized vulnerabilities, so your IT team has less work and a head start.
The new fixes (workarounds and version updates) for the SolarWinds Orion and SolarWinds Serv-U vulnerabilities are now available on Remedy Cloud here:
Don’t stop at updating only your SolarWinds tools. This was a layered attack. Make sure to remediate the 12 vulnerabilities targeted in the Russian cyber attack as well.
If needed, here is a quick tutorial on how to use Remedy Cloud to fix CVE-2017-14491, the notorious, and long-troublesome dnsmasq vulnerability.
Plan better and take the steps outlined above to mature the vulnerability remediation function at your company. Then when the next Russian cyber attack occurs, your organization will be ready and can skip the scramble to clean up after a bunch of hackers.









