-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
The MITRE ATT&CK framework helps security teams detect avenues of attack and better manage vulnerabilities. Here are the basics.

Managing security vulnerabilities can feel like swatting at flies—one vulnerability may be resolved, but a dozen more can pop up elsewhere.
Traditional security management strategies are struggling to keep up due to their growing complexity and the emergence of modern threats that are adept at evading detection. This has necessitated a shift towards more sophisticated detection methods, such as anomaly-based detection using machine learning and big data analysis.
To navigate these challenges, organizations are turning to comprehensive frameworks like Lockheed Martin’s Cyber Kill Chain, NIST’s Cybersecurity Framework, or the leading MITRE ATT&CK, to establish a more holistic security program. However, the real-world application of these theoretical frameworks requires a practical approach to integrate them with the Common Vulnerabilities and Exposures (CVE) system for a detailed understanding of vulnerabilities.
This blog post delves into the MITRE ATT&CK framework and the CVE system, highlighting the benefits of their integration to enhance organizational security and resilience against cyber threats.
It’s becoming increasingly clear that standard vulnerability management strategies are no longer enough. There are two reasons for this. First, is the growing complexity of traditional techniques. Typical security management techniques such as signatures, suspicious IP address lists, and indicators of compromise (IOCs) have grown increasingly complex and harder to track and manage. Second, is the introduction of modern techniques that increase effectiveness against emerging threats.
While traditional vulnerability and cyber risk management techniques are still effective and important, they may not be sufficient on their own to block modern threats. Today’s threats are more likely to adapt and work actively to evade detection.
Meanwhile, the fast proliferation of new technologies and attack areas across application, network and cloud enivoronments means that teams can no longer depend on traditional methods of detection:
200
Cybersecurity Ventures predicts that global data storage will exceed 200 zettabytes by 2025. This includes data stored on private, public, and utility infrastructures, private and public cloud data centers, personal devices, and IoT (Internet-of-Things) devices.
This has led to the rise of anomaly-based detection, which uses sophisticated methods like machine learning, statistical and other big data analysis to detect atypical, or anomalous, events. This combination of behavior-based and traditional techniques offers more protection.
To simplify cyber risk management and encourage best practices—while also paving the way for new techniques—many organizations are adopting comprehensive frameworks such as Lockheed Martin’s Cyber Kill Chain, NIST’s Cybersecurity Framework, or MITRE ATT&CK.
Today’s leading framework is MITRE ATT&CK, but as with other frameworks, it’s largely theoretical. All of these frameworks are based on a big picture of vulnerability management and prevention, aiming to help organizations establish a more comprehensive security program. But when dealing with vulnerabilities in the real world, a theoretical framework isn’t always enough.
As specific software vulnerabilities emerge, they are classified through the CVE system, also developed by MITRE, to create a common language around vulnerability management.
And in the real world, what would really help organizations plan, prepare, and prevent attack is a system that can bring these two concepts together: identifying the most prevalent attack strategies using the ATT&CK framework, and identifying specific software vulnerabilities using the CVE system.
Recognizing changes sweeping the security industry and the need to pave the way for anomaly-based detection, the nonprofit MITRE corporation released its ATT&CK framework in 2023.
It now dominates the industry—across enterprises, government agencies, and security vendors.
The most important thing to know about ATT&CK is that it takes an “adversarial” approach. This means it classifies activities based on the actions of adversaries in attacking an organization.
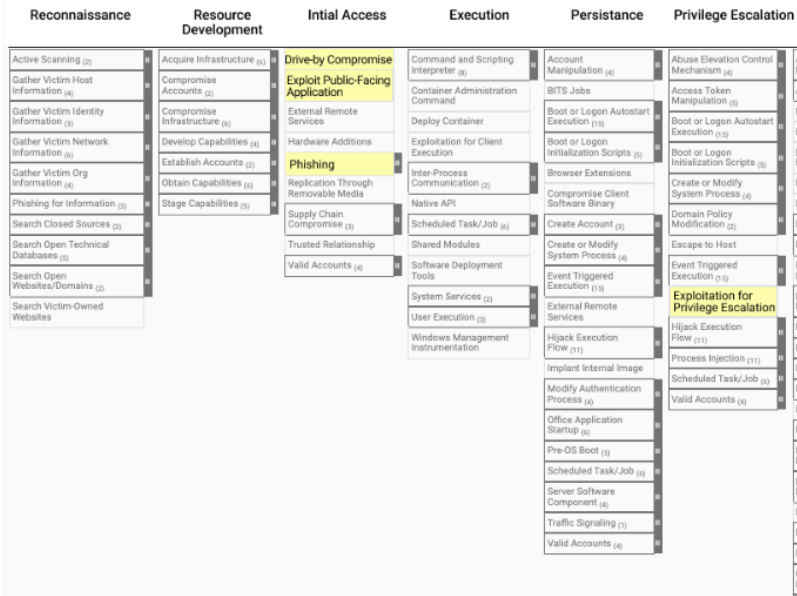
The MITRE ATT&CK framework serves as a comprehensive compendium of adversary tactics, techniques, and procedures (TTPs) employed throughout the intrusion lifecycle. It breaks down each stage in the attack process down into TTPs, as seen in the following example.
In a watering hole attack (also called “waterholing”), hackers compromise websites that a target victim or group (such as employees of a specific company) often visits to gain access to their devices and networks.
Here’s an example of how this would look broken down into TTPs under the ATT&CK framework:
This is just one example of how the ATT&CK framework provides a valuable tool for identifying and mitigating risks. Using the framework can help improve security awareness and training to help organizations protect themselves from cyber threats.
However, it’s clear even from this one small example—describing one very specific attack vector out of hundreds—that the ATT&CK framework is massive and comprehensive. It is also, as mentioned, largely theoretical—helping understand the tactics, techniques, and procedures that attackers will adopt, as well as proposed detections and mitigation mechanisms.
For example, at the bottom of every Technique page, MITRE lists best practices for detection, such as—on this page for drive-by compromise—inspecting URLs for potentially problematic domains and performing reputation-based analytics on websites and resources to stop users from venturing into dangerous territory.
While these mitigation tips are helpful, they underscore the need to reconcile ATT&CK TTPs with actual CVEs that an organization might encounter in order to create the most intelligent possible prioritization along with the most relevant mitigation steps.
The Common Vulnerabilities and Exposures (CVE) system is the most widespread method of tracking and enumerating publicly known weaknesses in software that can be exploited by attackers to gain access to systems or data.
The CVE system was also spearheaded by the MITRE Corporation in the late 1990s to help remedy inconsistent information sharing among organizations around vulnerability identification and classification. The CVE system was designed to be vendor-neutral and to provide a common language for discussing vulnerabilities.
For example, in the SolarWinds hack of 2020, attackers exploited a known vulnerability in the SolarWinds Orion software (enumerated as CVE-2020-10148) to gain access to the networks of multiple government agencies and private companies.
Yet though the CVE system was also created by MITRE, there is little to no innate crossover between ATT&CK TTPs and CVEs. Understanding the relationship between TTPs and CVEs, organizations can better prioritize vulnerability remediation efforts and improve their security posture.

Combining the real-world intelligence behind CVEs with the massive and comprehensive ATT&CK framework could help organizations in a number of ways:
Bringing the MITRE ATT&CK framework and CVE data together offers a great deal of promise to the threat hunting and threat intelligence fields—all of which will help make networks, data, and users safer into the future. But it also poses a number of challenges, making it one of the most fascinating areas of cyber security research today.
Find out more about how the Vulcan Cyber Voyager 18 research team is solving this and other problems to help build its next generation of cyber risk management platforms. Read the full white paper.