Today, teams struggle to manage and mitigate cyber risk, contending with IT environments that sprawl increasingly across siloed teams, tools, and technologies. In short, risk-based security is getting harder.
Traditional vulnerability management was hard enough. Keeping on-premises servers and hosts secure required the sustained efforts of security teams working to prioritize and fix those vulnerabilities that presented the most pertinent risk to their organizations. This was a challenge, but generally a manageable one.
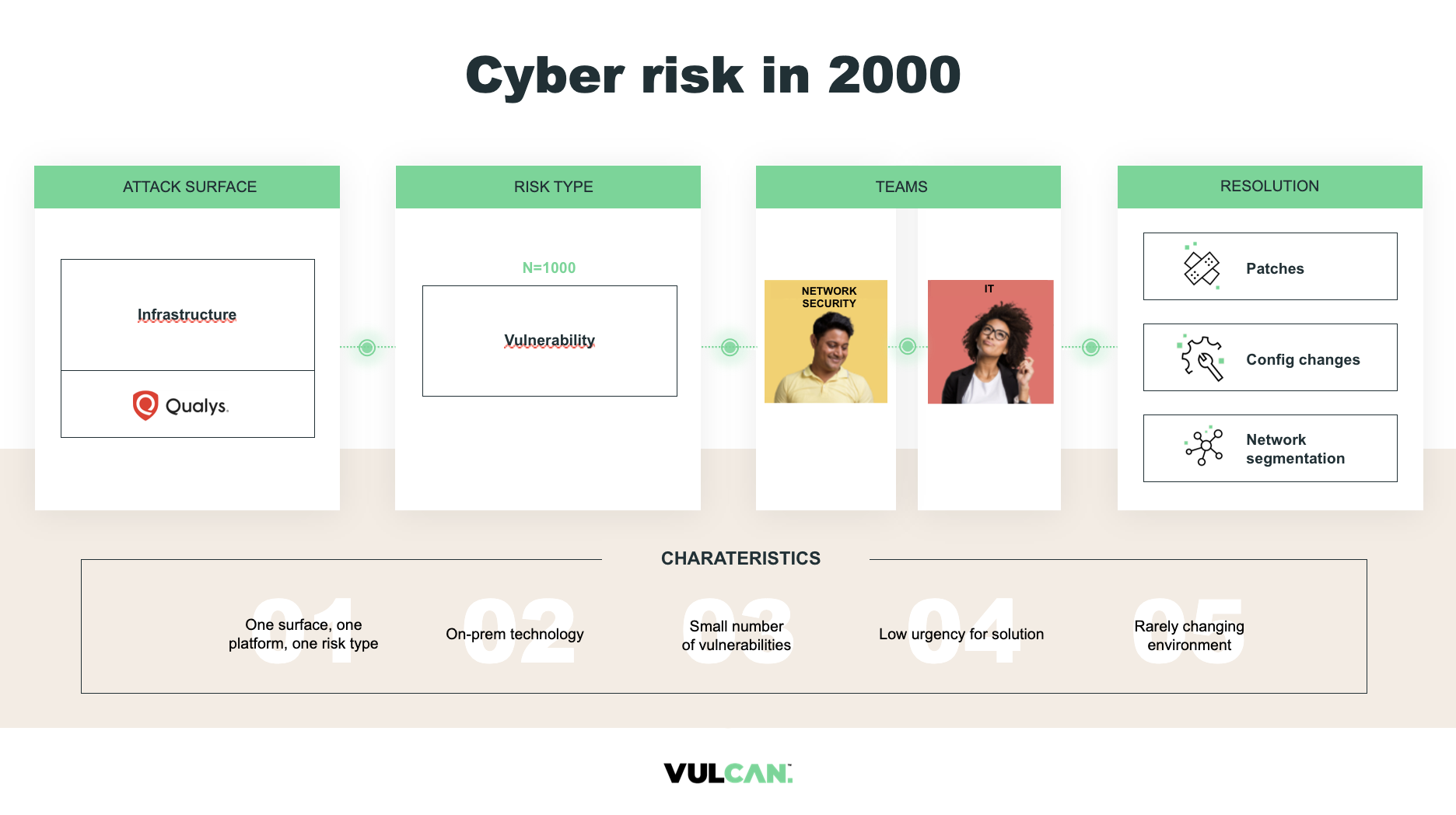
But as organizations have expanded across cloud and application environments, vulnerabilities and exploits have rapidly proliferated at a rate that represents a serious obstacle for security professionals. The success of their efforts to contain those threats depends on the maturity of their cyber risk management program.
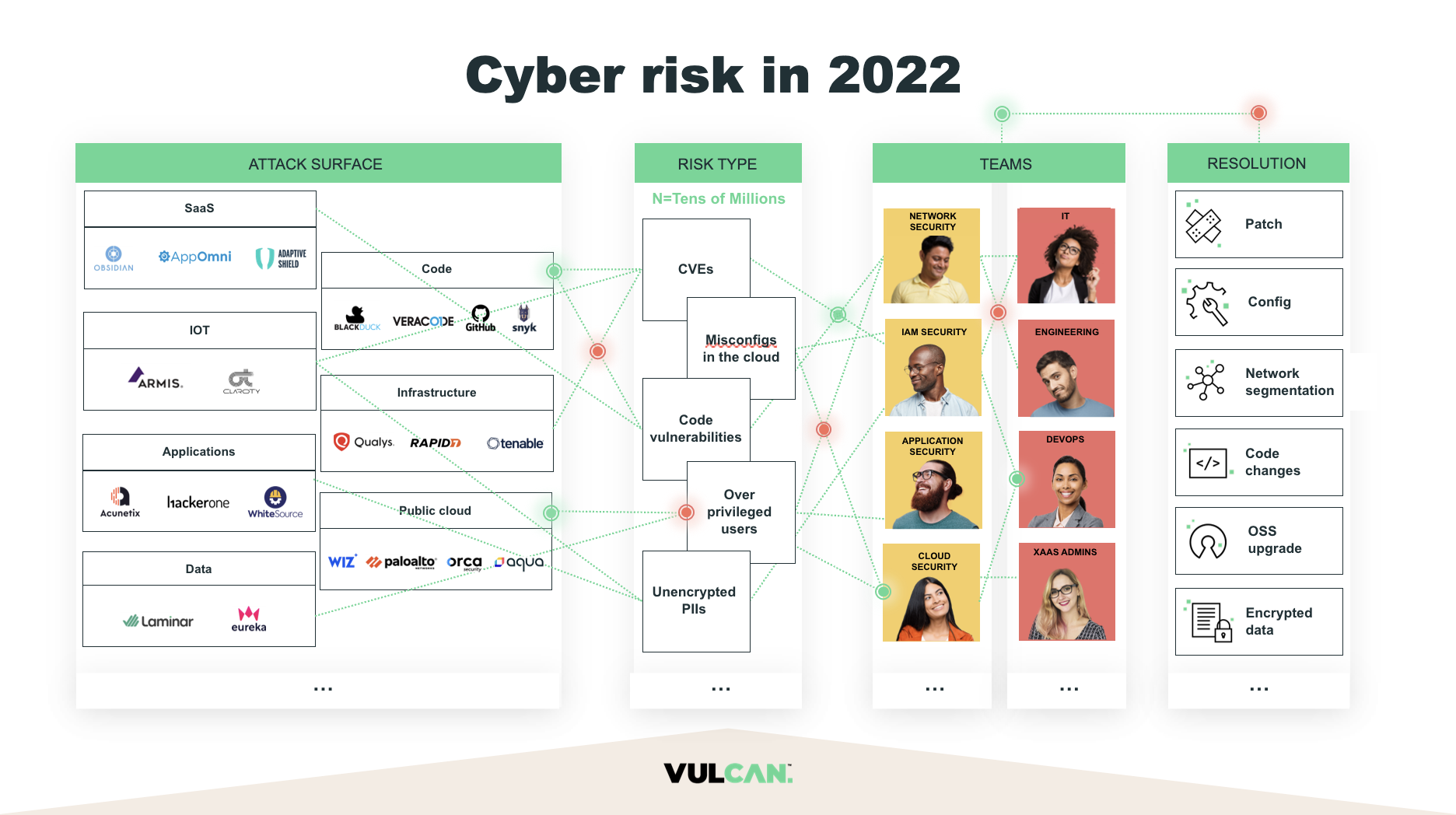
Vulcan Cyber has produced the Step-by-step guide to achieve vulnerability and risk lifecycle management success to describe the four major levels of risk based security maturity that organizations may find themselves in. This blog is an abridged version of the Ebook.
The need for risk based security programs
The following trends are driving the future of the cyber risk management landscape:
- A growing number of vulnerabilities year over year.
- More than 50 CVEs logged every day in 2021 according to Redscan Labs (a record number)
- 90% of all CVEs discovered in 2021 so far can be exploited by attackers with limited technical skills
- CVEs which require no user interaction, such as clicking a link, downloading a file or sharing their credentials, accounted for 61% of the total volume up to now
- 54% of vulnerabilities so far this year are classified as having “high” availability, meaning they are readily accessible/exploitable by attackers
- 60% of breach victims were breached due to a patchable vulnerability
- More than 50 CVEs logged every day in 2021 according to Redscan Labs (a record number)
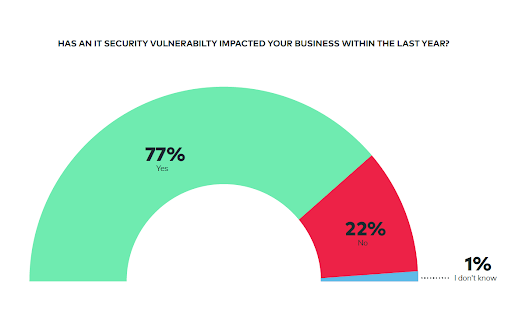
- The inherent complexity and scope of the enterprise environment.
- Cloud Security (State of Cloud Security Report-Cybersecurity Insiders)
- 95% of orgs are concerned about cloud security
- 58% rely on periodic vulnerability and compliance reports
- 90% use 2 or more cloud providers
- Appsec
- 40% have 5,000 or more security vulnerabilities that need to be addressed and that rate has quickly increased over the past 12 months.
- 68% experience a breach in the previous 12 months due to an application vulnerability
- Cloud Security (State of Cloud Security Report-Cybersecurity Insiders)
- There is a massive global shortage in skilled cybersecurity personnel.
- There were 3.5 million unfilled cybersecurity positions in 2021 (Cybersecurity Ventures)
- Only 36% say they have enough staff to patch fast enough to prevent a breach (Ponemon-SNOW infographic)
The clear trajectory is one of growing vulnerabilities and attack surfaces, together with limited resources and personnel. It’s never been more critical for organizations to make the most of their available resources with smart risk based security processes. But too often we see teams languishing in inefficient frameworks, falling into traps of cyber negligence, and failing to meet the growing security demands of their organizations.
The four stages of a successful risk based security program
Vulcan Cyber has analyzed hundreds of enterprise vulnerability management program assessments, including dozens of customers who have their vulnerability and risk lifecycle management practices on our platform. We have developed the Vulnerability and Risk Lifecycle Management Maturity Model to describe the enterprise journey from basic vulnerability management to a transformative risk based security program that turns vulnerability and risk management into an organization-wide program and delivers significant business value and peace of mind.
Stage 1
Reactive – Regularly scan infrastructure assets for vulnerabilities and manage remediation on a case-by-case basis using CSV scoring for basic prioritization.
Stage 2
Data-driven – Centralize vulnerability and risk management lifecycle activities to drive actionable insights prioritized by risk using vulnerability, asset, threat intelligence and remediation data.
Stage 3
Orchestrated – Eliminate inefficient manual processes and institutional operating silos to effectively remediate vulnerabilities and risk at scale and speed.
Stage 4
Transformative – Rally business and product stakeholders around implementing processes that make effective cyber hygiene an organization-wide priority.
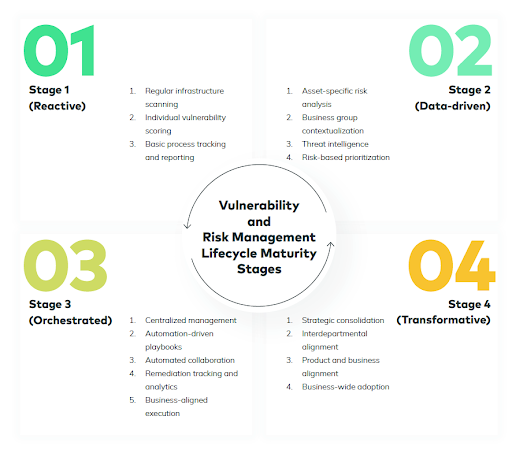
Building for company-wide risk based security transformation
An enterprise’s journey towards transformative vulnerability and risk lifecycle management is an iterative process. It involves a series of incremental programmatic and technology improvements that will eventually lead to enterprise-wide adoption of risk management best practices throughout the organization.
It is critical to recognize the need for security, operations and application development teams to work together, striking the balance between effective collaboration and different priorities and operating procedures. Security teams must identify, prioritize and then communicate the most pressing cyber risk concerns to the other teams involved in keeping the orgaization secure.
While remediation may be the final objective, risk based security is a process comprising several foundations that must all be built upon. Asset consolidation, prioritization of vulnerabilities, collaboration and automation are all key aspects of an effective cyber hygiene program.
The Vulcan Cyber cyber risk management platform has been built from the ground up to deliver transformative outcome-driven vulnerability and risk lifecycle management. Vulcan Cyber integrates all of the relevant teams and their native tools to make vulnerability and risk management processes a seamless collaborative effort with high levels of automation and orchestration. Highly contextual, risk based vulnerability prioritization and remediation intelligence ensure that an enterprise’s risk management efforts provide maximum business impact.
See how Vulcan Cyber can accelerate your company’s vulnerability and risk management maturity. Request a demo










