-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Cyber security compliance requires organizations large and small to prepare a minimum level of protection for their systems and sensitive data. In this guide, we will define the importance of managing your cyber risk and compliance, noting key laws and frameworks, risks, and challenges, and providing insight into the best solutions.
Cyber security compliance refers to the practice of ensuring that an organization adheres to rules, regulations, standards, and laws designed to protect information and data. These guidelines are established by various governing bodies and organizations, and they may be applicable at the local, national, or international level.
Compliance requirements vary based on factors like the type of data handled by the organization, its size, the industry in which it operates, and the jurisdictions within which it operates. Non-compliance can result in penalties, including fines, loss of customers, damage to reputation, or even legal consequences.
Organizations struggle to keep pace with the constant rise of new cyber threats and the high expectations of regulators. They often minimize the consequences of falling out of compliance. However, there can be severe repercussions, including:
In 2022 alone, more than 48 million individuals were affected by data breaches in healthcare, from over 590 organizations.
Meanwhile, 66% of CISOs in 2023 plan to increase investment in cyber security, according to the Wall Street Journal.
Cyber attacks catch unprepared businesses off guard, regardless of their industry or size. For instance, Oklahoma State University’s Center for Health Sciences settled its case in 2018 for $850,000 when its noncompliance caused the impermissible disclosure of 279,865 individuals’ personal health information (PHI), along with delayed reporting and its failure to evaluate their security.
Some cyber security compliance standards differ from one country to the next, but if you violate terms in another jurisdiction, you may still pay for noncompliant behavior. Amazon, for example, was forced to pay $886.6 million for violating the EU’s General Data Protection Regulation (GDPR) rules when processing personal data.
Cyber security compliance refers to the adherence to regulatory guidelines, standards, and laws that relate to an organization’s cyber security policies and procedures. The responsibilities associated with cyber security compliance can vary based on the specific regulations or standards an organization must adhere to. However, some general responsibilities include:
Risk Assessment: Regularly evaluate and identify vulnerabilities and threats to the organization’s information systems.
Policy Development: Create, maintain, and enforce cyber security policies and procedures that align with compliance requirements.
Training and Awareness: Ensure that employees, contractors, and other relevant stakeholders are aware of and trained on cyber security policies and best practices.
Incident Response: Develop and maintain an incident response plan to address potential security breaches or cyberattacks.
Regular Audits: Conduct periodic audits to ensure that cyber security practices align with compliance requirements and to identify areas of improvement.
Data Protection: Implement measures to protect sensitive and personal data, including encryption, access controls, and data classification.
Access Control: Ensure that only authorized individuals have access to sensitive data and systems, and regularly review and update access controls.
Patch Management: Regularly update and patch software, hardware, and applications to address known vulnerabilities.
Vendor Management: Ensure that third-party vendors and partners also adhere to required cyber security standards.
Documentation: Maintain detailed records of all cyber security efforts, including risk assessments, incident response activities, and training sessions.
Reporting: Report any breaches or potential security incidents to relevant stakeholders, including regulatory bodies, as required by compliance standards.
Continuous Monitoring: Implement tools and processes to continuously monitor the organization’s IT environment for potential threats or vulnerabilities.
Physical Security: Ensure that physical access to critical infrastructure, such as data centers, is restricted and monitored.
Backup and Recovery: Implement and regularly test backup and recovery procedures to ensure data integrity and availability in case of incidents.
Stay Updated: Keep abreast of changes in compliance requirements and adjust policies and procedures accordingly.
Legal and Regulatory Adherence: Understand and adhere to all local, national, and international cyber security laws and regulations relevant to the organization’s industry and operations.
Stakeholder Communication: Regularly communicate with stakeholders, including the board of directors, about the organization’s cyber security posture and compliance status.
It’s important to note that specific responsibilities can vary based on the industry, country, and specific regulations an organization is subject to (e.g., GDPR, HIPAA, PCI-DSS, etc.). Organizations often have dedicated compliance teams or officers to ensure that they meet all these responsibilities and remain compliant with relevant regulations.
While the purpose of compliance is always to provide guidance to companies on the best security practices, there’s an important distinction between mandatory and voluntary compliance.
Mandatory compliance is required by national or international laws or regulations, whereas voluntary compliance is a set of standards to help organizations maintain secure systems.
Even if a company isn’t breaking a regulatory requirement, there’s potential for legal action and public scrutiny if a breach occurs.
On-demand webinar: Risk-based Vulnerability Management for Continuous Compliance
The following are some of the most significant laws and regulations regarding the handling of cyber security risk and compliance.
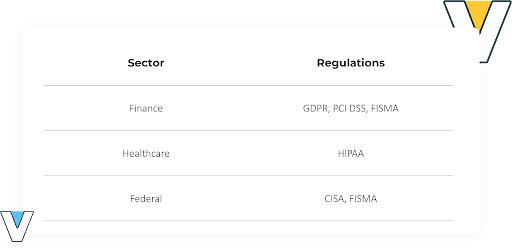
This US federal law protects consumers from the misuse of their nonpublic personal information (NPI) like addresses and social security numbers (SSN) by financial institutions that offer financing, loans, insurance, and investment advice.
Fines for mishandling user NPI can range from $5,000 to $1 million per day.
HIPAA is a US federal statute to protect patient healthcare data. It’s a mandatory patient privacy compliance for HMOs, their subcontractors, and partners.
The HIPAA Office of Civil Rights (OCR) has investigated more than 296,419 complaints. In cases where the OCR finds negligence, fines or penalties are based on civil and criminal tiers rated on unintentional or willful neglect, and whether disclosures occurred with or without false pretenses or malicious intent.
CISA is a federal law governing how cyber threat data is to be shared between governmental agencies and the private sector. CISA is unique, in that it does not enforce compliance with penalties. Rather, it provides the necessary guardrails to help organizations share data about threats and their best resolutions.
CISA is controversial because sharing details of specific cyber threats in itself can lead to compromised data, but the risks can be greater if institutions and companies aren’t warned of potential threats and their handling.
This is a federal law that requires federal agencies to protect the confidentiality of their data systems and the data stored on them. Penalties for failing to maintain standards can range from disciplinary actions to criminal charges.
GDPR is a regulation for the EU that directly impacts all US organizations that handle the personal data of EU-based users. GDPR requires security measures in dealing with personal user data. Failure to protect user data can result in fines of up to 4% of an organization’s annual global revenue or €20 million.
Read report: Vulcan Cyber named a leader by Forrester for Vulnerability Risk Management
In Europe, separate compliance standards have been established to reflect the unique requirements and challenges of the region.
The Digital Operational Resilience Act (DORA) and Network and Information Systems Directive (NIS2) are essential EU regulations designed to enhance cyber resilience across financial and critical sectors. These frameworks mandate robust cyber security practices, including risk management, incident reporting, resilience testing, and third-party risk monitoring. Together, DORA and NIS2 aim to safeguard vital industries against digital disruptions, ensuring that organizations can effectively manage and mitigate cyber risks while maintaining compliance with EU standards.
Laws and regulations are put in place to ensure organizations follow standards to help keep data safe. They can be effective when the incentive to take proper precautions is greater than the impact of fines and legal actions.
Frameworks are effective in helping to define the right cyber risk management and compliance practices companies should follow. Frameworks provide three main benefits:
Compliance frameworks help provide a clear path organizations should take.
Frameworks help companies follow a system to recognize and assess risks.
Frameworks provide the steps organizations need to take to avoid the negative legal fallout of bad cyber security practices.
The following frameworks are viewed as the standard for institutions to follow.
NIST is a non-regulatory agency focused on fostering innovation and protecting intellectual property. The NIST cyber security framework is a seven-step cyber security framework that is mandatory for US government agencies and many of their direct contractors, but voluntary for all non-governmental organizations.
PCI DSS is a set of minimum standards developed by Visa, MasterCard, Discover, JCB, and American Express, for storing, processing, and transmitting user data, including primary account numbers (PANs) and service codes (CVVs).
It’s not a law or an act formed by governments, but it’s mandatory for all entities using these payment services, and has been made a law in some jurisdictions. Penalties can range from $5,000–$100,000 per month.
The ISMS includes various ISO-designated information standards for protecting information assets: specifically, it provides detailed frameworks for protecting sensitive internal organizational data.
FedRAMP is a set of standards for government agencies used in assessing and monitoring cloud-based systems. This is based on NIST 800-53.
As the name suggests, HICP is the design of the Department of Health and Human Services, providing a framework for protecting data in the healthcare industry.
On-demand webinar: How to Achieve Complete Cyber Risk Management
The ever-evolving compliance landscape and the lack of resources are two of the biggest hurdles companies face when trying to remain compliant. Below, we explore these challenges in detail.
Many organizations lack the financial resources and talent they need to research vulnerabilities and use attack path modeling to identify potential threats.
Many organizations are simply overwhelmed by integrating safety checks, updating software patches, and constantly checking their systems while trying to maintain their daily workflow.
Organizations may be required to comply with numerous regulations and separate guidelines. This includes practices, but also reporting.
The landscape of attacks, infrastructure, and compliance is constantly changing. Responding to threats with the right remediation is slow and confusing.
The more complex an organization is, the more challenging it can become to exercise adequate attack surface management.
Throughout the software development and optimization lifecycle, cyber security becomes a trade-off between time and resource efficiency.
Cloud data storage and computing may provide an added layer of security depending on your agreement with your provider. That said, it can also add a layer of complexity. With cloud data storage, you must remain aware of what data is in the cloud, what laws regulate that data, and how best to implement real-time protections.
White paper: Cloud security blind spots (and how to avoid them)
The following are five ways organizations can achieve cyber security compliance and actively protect their systems.
Analyze your systems and data to uncover potential cyber threats and prioritize how to go about mitigating risks.
Conducting a risk assessment is a proactive way to demonstrate your intentional pathway to compliance, identify risks and vulnerabilities, and document them.
Create a system for implementing your organization’s safeguards, including access controls, network administration rights, and data encryption.
Establish clear security protocols that all employees and contractors must follow.
Increase company-wide awareness and uphold accountability by training employees to recognize phishing emails, social engineering, and other effective threats. Teach the importance and effectiveness of password security and incident reporting.
Proper ongoing training is an opportunity to monitor compliance and progress and identify areas for improvement.
Company-wide security controls can include rules for information access, data encryption, and network server segmentation. Develop plans for backup and recovery in case of an incident.
Running scheduled scans can instill a false sense of security when cyber attacks become increasingly sophisticated every day. Today’s cyber security is best managed when organizations implement continuous real-time detection like those provided by Vulcan Cyber.
The volatile nature of cyber crimes requires organizations to take proactive measures to protect their systems while also maintaining compliance with laws and regulations.
Cyber security best practices to follow include:
Above all, the best way to remain compliant is to have a comprehensive platform that assists end-to-end, from diagnosis to remediation and mitigation.
Vulcan Cyber provides a single platform that simultaneously handles your vulnerability management and compliance with all regulatory standards. Vulcan Cyber empowers your organization to:
Ready to take control of your cyber security compliance? Get in touch with one of our experts today and try Vulcan for free!
Cyber Security Governance and Risk Management involves overseeing adherence to established cyber security protocols and handling the evaluation and control of associated risks. At an entry-level position, the responsibilities encompass a diverse range of tasks centered on the practical aspects of risk management, including the creation of policies.
The objective of security compliance management is to establish a strong security framework that meets industry benchmarks and is in harmony with company policies and regulatory requirements.
Cyber compliance is about adhering to regulatory standards to fulfill contractual obligations or third-party regulatory demands. On the other hand, security focuses on deploying appropriate technical measures to safeguard digital assets against cyber threats.
The ISO/IEC 27001 standard provides a framework for organizations to create an information security management system, allowing them to implement a risk management process tailored to their specific size and requirements. This system can be scaled and adjusted as the organization’s needs and size change over time.