With remote work, cloud migration, and reliance on third-party software all playing a part, security teams are facing a multi-directional challenge to protect company data. While vulnerability management processes are growing more mature as we head into 2024 – especially when it comes to automated vulnerability remediation – many organizations continue to struggle with the sheer volume of information.
In this blog, we’ll explore the case for automation in vulnerability remediation and management, drawing upon our learnings from our report with SANS: Vulnerability Management Survey 2022, as well as research for 2023.
What is automated vulnerability management?
Automated vulnerability management is a process in the field of cyber security where vulnerabilities in software or systems are identified and fixed automatically, without the need for manual intervention. This process is crucial in maintaining the security of systems and protecting them against potential threats and exploits. Here’s how automated vulnerability management typically works:
Vulnerability Detection
The first step is identifying vulnerabilities. This can be done using various methods, such as vulnerability scanners, which scan the network and systems to find known vulnerabilities.
Assessment and Prioritization
Once vulnerabilities are detected, they are assessed and prioritized based on the level of risk they pose. This step often involves analyzing the severity of the vulnerability, the potential impact of an exploit, and the likelihood of an attack.
Automated vulnerability remediation
After the assessment, the system automatically applies patches or configuration changes to fix the vulnerabilities. This step might involve updating software to the latest version, applying security patches, or changing settings to secure the system.
Verification
After remediation, the system often re-scans to verify that the vulnerabilities have been successfully addressed.
Continuous monitoring
Automated systems continuously monitor for new vulnerabilities, keeping the systems secure over time.
The advantages of automated vulnerability remediation include:
Speed
It significantly reduces the time to remediate vulnerabilities, which is crucial in mitigating risks.
Efficiency
Automating repetitive tasks allows IT staff to focus on more strategic initiatives.
Consistency
It ensures that all vulnerabilities are addressed in a consistent manner.
Scalability
It can easily scale to cover large networks and numerous devices.
However, it’s important to note that while automated remediation is highly effective for certain types of vulnerabilities, it might not be suitable for all scenarios. Complex vulnerabilities might require manual review and remediation to ensure that the fixes do not disrupt system functionality or business operations.
Organizations are increasingly turning to automation
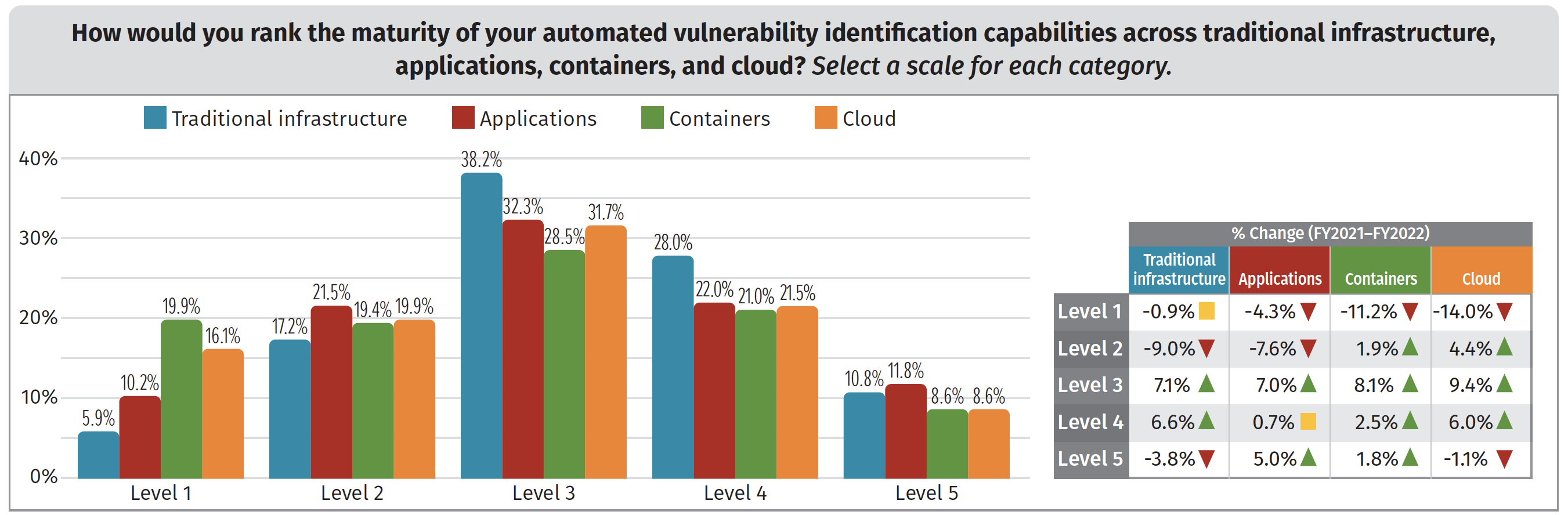
Compared to last year, organizations are more mature when it comes to automated discovery or scanning for vulnerabilities, with improvements in this area seen across all environments, including a particularly impressive increase when it comes to the cloud. In 2022, automated vulnerability identification was seeing at least some adoption by most organizations.
Now, as we close out 2023, the benefits of automation in vulnerability management workflows are clear.
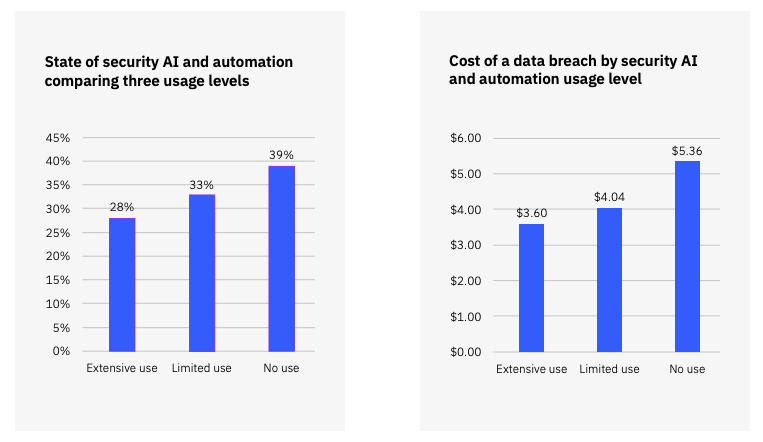
According to IBM, while less than a third of surveyed security professionals reported extensive use of AI and automation, the cost of a data breach fell drastically with increased employment of automation.
Other cyber risk management trends to look out for
API security a growing concern
As enterprise environments grow, reliance on APIs has increased. At the same time, the security threat has proliferated.
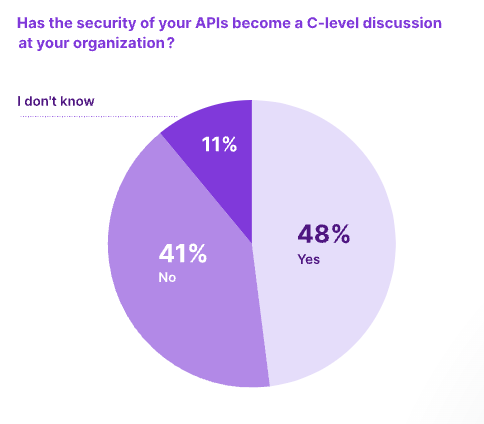
According to a survey from Salt Security, 48% of respondents say API security is now a C-level issue:
With more and more technologies adopted, we can expect the attack surface to expand, and for API to become an even greater target.
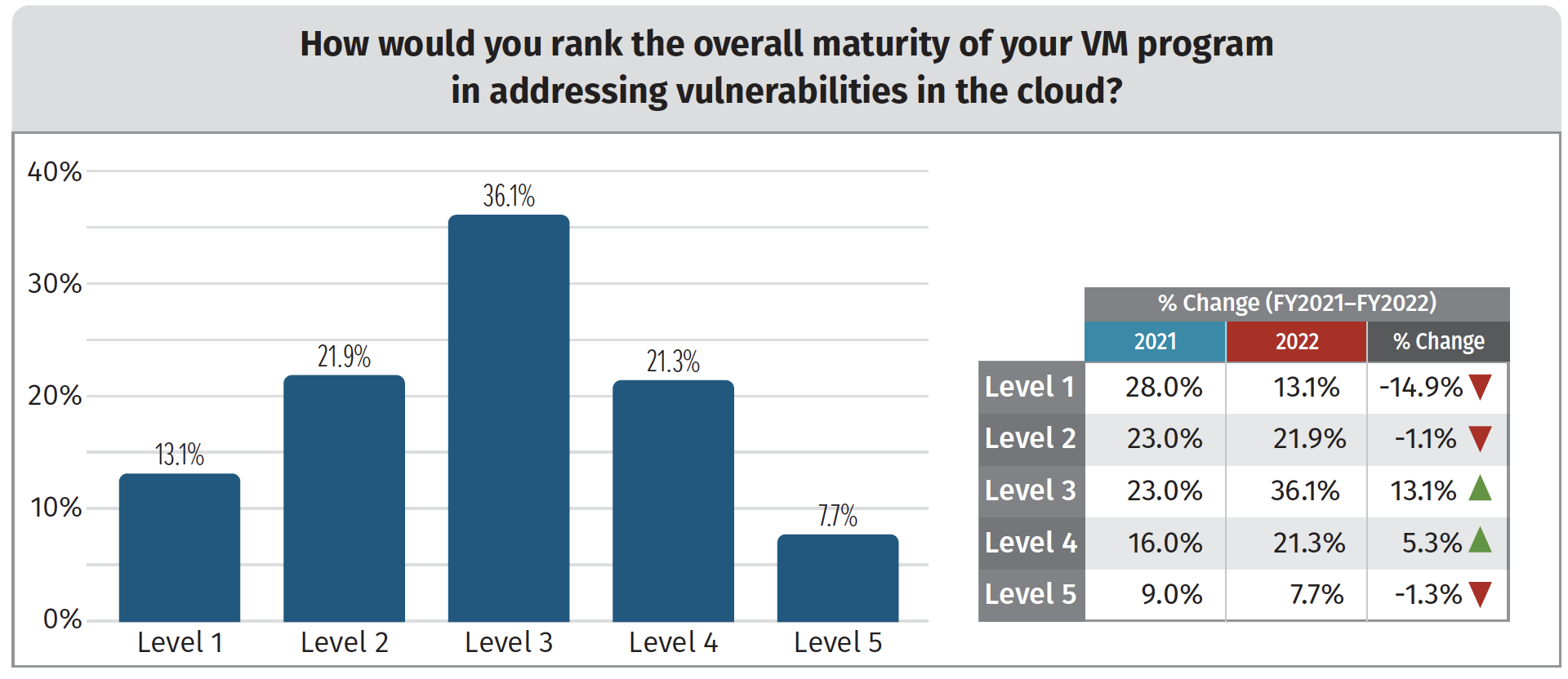
Cloud vulnerability management maturity is increasing – but problems remain
As organizations grow more reliant on cloud environments, it makes sense that IT security teams are becoming more comfortable with vulnerability management programs in the cloud.
In general, organizations in 2022 were rating themselves much higher for their cloud vulnerability management capabilities than in 2021.
While this is encouraging, research from Astra Security found that 79% of companies are looking for a more efficient cloud security assessment process.
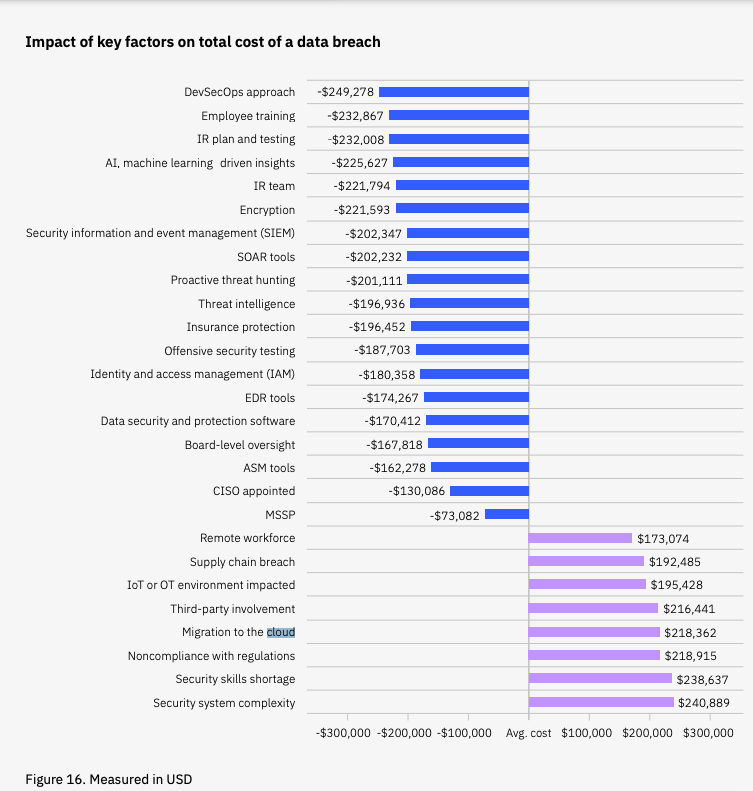
Meanwhile, 2023 still saw migration to the cloud as one of the biggest factors impacting the cost of a data breach:
Automated vulnerability remediation and more – the bottom line
Risk-based vulnerability management today must keep up with the pace and scale of cyber attacks growing in sophistication. Automation plays a big part here, with automated vulnerability remediation presenting significant benefits when it comes to time saved on manual tasks and preventing data breaches.
As we head in 2024 and technologies change and attack surfaces emerge and grow, IT security practitioners must be proactive about managing the vulnerability management lifecycle. To learn more about the Vulcan Cyber risk management platform, you can get a demo today.