-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Vulnerability aggregation
Vulnerability and risk data consolidation from application, cloud and infrastructure assets, in a single operational view.






01
Dast, sast, cloud and infrastructure scanners, threat intelligence, cmdbs, edrs and dozens of other sources deliver critical visibility necessary to understand risk, but hard to manage.
02
Rapid application development, constantly shifting devops processes, hybrid cloud infrastructures, and highly distributed environments create broken cyber risk management programs.
03
Enormous volume of scan data creates duplicated data, dramatically increasing the number of inputs for cyber risk posture and leaving organizations flying blind as they try to coordinate and efficiently manage real cyber risk
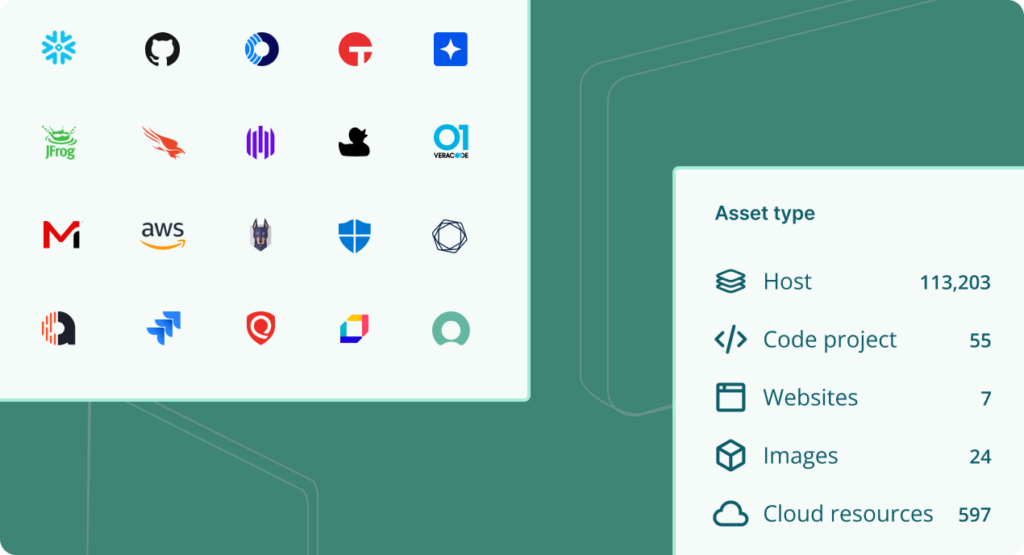
Vulcan Cyber consolidates vulnerability and risk data across all your attack surfaces, putting all your application, cloud and infrastructure assets in a single operational view to paint a clear picture of security risk posture.
Vulcan Cyber integrates with your vulnerability scanners, paired with your asset management tools and external feeds such as threat intelligence, to show actual risk to your business, across all attack surfaces.
Vulcan cyber helps you move beyond basic centralization by consolidating scan data from multiple sources into a single stream so you can manage your vulnerability and cyber risk efficiently.








you are here
Collaborate
you are here
Report
We use cookies to personalise content and ads, to provide social media features and to analyse our traffic. We also share information about your use of our site with our social media, advertising and analytics partners.
View more