In 2023, security issues have increased in cloud assets, leading to more data breaches involving cloud environments. But, despite the growing threats and attached cyber risk, organizations are undeterred in migrating to the cloud with greater acceleration than ever before.
But is the greater exposure to cyber risk matched by organizations taking the steps to improve the security around and within their cloud environments?
Exploring the findings from SANS’ 2022 report on cloud security risks, and recent 2023 trends, here are just some of the lessons we learned about cloud security as we head into 2024.
Multi-cloud environments are becoming more commonplace
2022 again saw a steady increase in organizations taking advantage of multi-cloud environments:
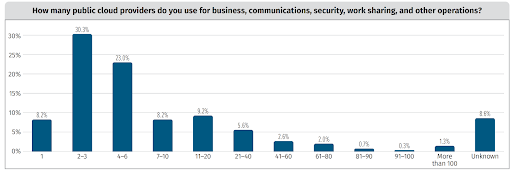
The number of organizations using 11-20 cloud providers, for example, increased from 3% in 2021 to 9% in 2022.
And in 2023, 76% of organizations have adopted a multi-cloud strategy, with this number expected to grow to 86% in 2024.
But as teams grow bolder in their harnessing of cloud technologies, they must scale up and optimize their security efforts to counter the attached cyber risk. Multi-cloud environments mean a wider attack surface. Threats inevitably rise and mitigating that risk requires robust security controls tailored to this unique new threatscape.
Teams are taking care of cloud security basics – but it’s not enough
As cloud grows, teams are growing more confident in the basics of locking down their cloud environments against the types of threats that were big areas of concern in the past. The number of DDoS attacks, for example, has continued its downward trend from 2021, involving just 25% of the attacks covered in this survey.
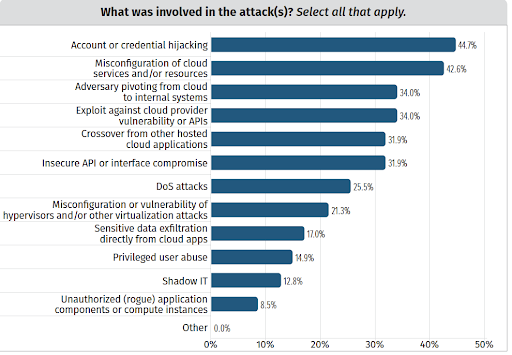
But there remain big security concerns that have increased in risk in 2022. Misconfigurations and operational and workflow failings are big contributors to the major breaches of the past year:
And according to a 2023 report by Checkpoint, 59% of respondents saw misconfiguration as the biggest threat to cloud security:
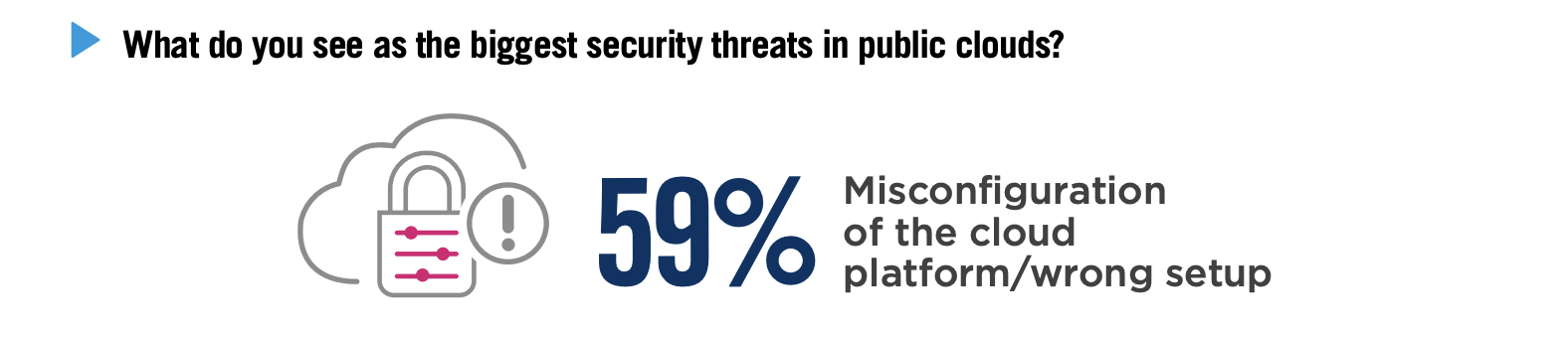
The biggest issues stem from the wrong configurations, personnel inefficiencies and a lack of resources, rather than outright unauthorized access. In contrast, in the years before 2022 unauthorized access was the biggest concern for organizations.
This shift is important. Protecting against obvious threats is just a part of maintaining good security posture. Inefficient processes, flawed workflows, and untrained personnel all contribute to and have significant effects on cyber hygiene. For a threat actor, every minor configuration is an opportunity to cause chaos.
Cloud configuration and security policy management in 2023
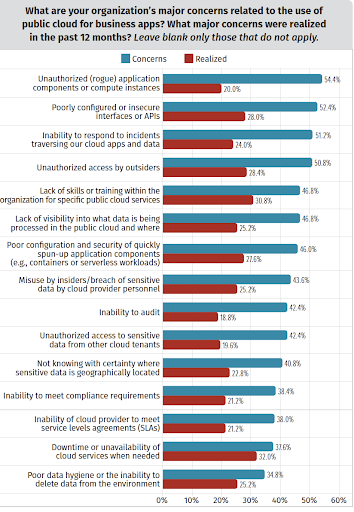
According to the same Checkpoint report from above, a majority of respondents in 2023 use cloud-native tools or CSPM solutions for management but face issues with multiple security solutions and policies.
Diving deeper, 62% of organizations predominantly rely on cloud-native tools. Meanwhile, 29% opt for specialized CSPM (Cloud Security Posture Management) solutions. A notable challenge surfaces with 72% of users needing to navigate through three or more distinct security solutions to set up their cloud policies, leading to complexities in both cloud management and security.
The same report finds that 37% of organizations have implemented DevSecOps practices, 40% incorporate Cloud Infrastructure Entitlement Management (CIEM) within their Cloud Security Posture Management (CSPM) strategies, and a significant 90% show a preference for managing their cloud security through a unified platform.
The potential and pitfalls of the cloud
In 2023, the benefits of migrating to a cloud environment are clear to see. The speed, ease of use, and convenience of cloud computing make it a tempting proposition – and organizations are lining up to take advantage. This trend will only continue as teams adjust to hybrid working models. But as cloud migration increases, so does the level of cyber risk. It’s important for organizations to acknowledge and address proactively the cyber security ramifications of a new environment that has emerged as a major attack surface in recent years.
Cloud security requires customized tools and processes. Teams must be trained and given the resources and instruction to become active parts of the cyber risk management lifecycle. This is true of all cyber security efforts, but with every connected device having potentially easy access to sensitive data stored on the cloud, the need for a shared responsibility approach to security has never been more pronounced.
Cyber risk is always evolving. Organizations need to recognize it, understand what it means to them specifically, and take the necessary steps to address it. This is a process of processes – the responsibilities split across different teams with different workflows and levels of understanding when it comes to security. Meanwhile, the risk isn’t waiting for you to figure it out.
The Vulcan Cyber risk management platform gives you end-to-end visibility of the entire cyber security lifecycle – from uncomfortably vulnerable to comfortably secure. To learn how you can stay ahead of cyber risk, book a demo today.