“My Microsoft Word got hacked” might have been a good way to get out of doing homework growing up, but Follina – the new zero-day MSDT vulnerability affecting the word processor – is no laughing matter.
Here’s everything you need to know about CVE-2022-30190.
What is the Follina MSDT vulnerability?
Follina uses the Word remote template feature to fetch code from a remote server and execute it using MSDT (Microsoft Diagnostic Tool).
The vulnerability works by embedding an external link to a remote server and utilizing the ms-msdt protocol in order to run PowerShell code. The vulnerability has received the name Follina and has been tagged as CVE-2022-30190 with a score of 7.8 out of 10.
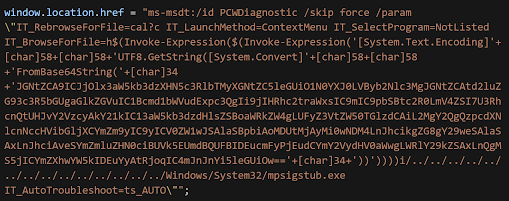
Obfuscated payload code, source: nao_sec
Does it affect me?
By default, Microsoft Word opens in “protected view” mode to alert and prevent reaching potentially unsafe locations, but it can easily be bypassed by saving the document as an RTF (Rich Text Format) file. By doing so, the file can be executed by selecting it in Windows directory explorer alone, thanks to the preview pane:
Source: Microsoft TechNet
Has CVE-2022-30190 been actively exploited in the wild?
The vulnerability was first discovered by a security research team named nao_sec while searching for wild exploitations of CVE-2021-40444. The domain related to the original exploitation is not available anymore, but it is safe to assume that there are more exploitations out there.
Fixing the Follina MSDT vulnerability
Because of the way in which the vulnerability works, the Word document itself does not hold the malicious payload, which makes it harder to detect infected documents.
However, there are a few actions you can take to prevent exploitations inside your organization:
- Since the vulnerability is using MSDT in order to run the malware, you can prevent Word documents from creating a child process of “msdt.exe” using a rule-based anti-virus.
- You can disable the preview pane in windows explorer, but it will not prevent the payload to run when entering the document itself:
- Open file explorer.
- Click on the View tab.
- Click on the preview pane button to hide it
- You can disable msdt completely by running removing it from the registry, as published by Will Dormann, a vulnerability analyst at the CERT/CC:
-
- Create a new text file called disable_ms-msdt.reg
- Paste the text from the github repository.
- Double click the .reg file, if you are prompted by Windows UAC, select Yes
-
Next steps
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:
- https://vulcan.io/blog/the-most-common-cves-and-how-to-fix-them/
- https://vulcan.io/blog/print-spooler-and-more-the-most-popular-windows-cves/
- https://mitremapper.voyager18.io/
- https://cyber-risk-community.slack.com
- https://vulcan.io/remedy-cloud/
And finally…
Don’t get found out by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your threat environment and lets you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.










