Contributor: Yair Divinsky
In today’s rapidly evolving digital landscape, the security of software supply chains has become a critical concern for organizations worldwide. With the increasing prevalence of software supply chain attacks, where vulnerabilities within the supply chain are exploited to gain unauthorized access or compromise software integrity, it is paramount to evaluate the risks associated with these vulnerabilities.
KEY STAT: By 2025, Gartner predicts that cyber security risks will play a significant role in conducting third-party transactions and business engagements for 60 percent of supply chain organizations, according to the perspective of their chief supply chain officers.
Understanding the potential attack paths that can be leveraged by malicious actors is crucial for prioritizing risk mitigation efforts and safeguarding the security and trustworthiness of software products. In this article, we will delve into the intricacies of evaluating vulnerability risks within the software supply chain and propose a better approach using attack path analysis.
By connecting the dots between vulnerabilities, their origins in the supply chain, and potential attack paths, organizations can gain valuable insights to fortify their defenses and ensure the integrity of their software products throughout their lifecycle.
Scanning the software supply chain
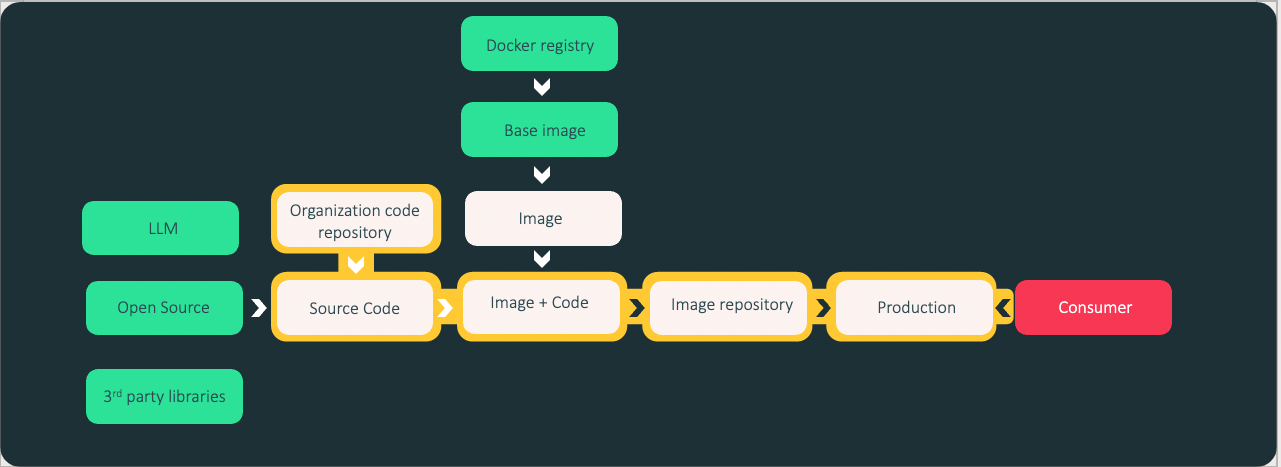
The cloud software supply chain
Here’s a step-by-step breakdown of the cloud software supply chain and its components, starting from coding to building images and running containers, along with examples of tools and platforms used in each step:
Step 1: Coding and development: At the beginning of the cloud software supply chain, developers write code to create the software applications.
Security Scanners:
- Static Application Security Testing (SAST) tools: These tools analyze the source code for security vulnerabilities and coding errors. Examples include, Snyk, WhiteSource, Checkmarx, and Fortify.
Step 2: Continuous Integration and Delivery (CI/CD) pipelines: These enable DevOps teams to automate the process of integrating code changes, building software, running tests, and deploying it to the cloud.
Security Scanners:
- Software Composition Analysis (SCA) tools: These tools scan the dependencies used in the codebase and identify any known vulnerabilities. Examples include OWASP Dependency-Check, Black Duck, and WhiteSource.
Step 3: Building Images and Containers: In the cloud software supply chain, developers build container images that encapsulate the application and its dependencies. Popular containerization technologies include Docker and container orchestration platforms like Kubernetes.
Security Scanners:
- Container Security Scanners: These tools scan container images for vulnerabilities and configuration issues. Examples include Anchore, Clair, and Twistlock.
Step 4: Infrastructure as Code (IaC): This enables the provisioning and management of cloud infrastructure using declarative code. Tools like Terraform and CloudFormation allow developers to define infrastructure resources as code.
Security Scanners:
- Infrastructure Security Scanners: These tools assess the security of infrastructure-as-code templates and identify potential misconfigurations or vulnerabilities. Examples include tfsec and Checkov.
Step 5: Deployment and Management: Once the infrastructure is provisioned, the containers or images are deployed to the cloud environment. Container orchestration platforms like Kubernetes manage the deployment, scaling, and monitoring of containers.
Security Scanners:
- Runtime Security Monitoring: These tools monitor the deployed containers and their runtime behavior for any malicious activities or deviations from normal behavior. Examples include Wiz, Orca, Tenable and Aqua Security.
Lastly, security teams play a crucial role in identifying vulnerabilities impact, implementing security measures, and monitoring for any potential risks or breaches. Security teams work closely with other stakeholders in the software supply chain to ensure that security is a top priority at every stage.
Threat scenarios
In recent years, known software supply chains including the BitCoin wallet attack, CodevCov , SolerWinds and others have been discussed in excruciating detail but, if we generalized them, we could identify additional potential attack scenarios to consider:
- An adversary compromising a CI/CD environment by:
- Injecting a malicious or vulnerable dependency or publishing poisoned packages that can be generated by LLMs
- Modifying CI/CD configurations files.
- Injecting code to IaC configuration
- Injecting code into source codes
- An adversary acquiring a developer’s credential to access a repository service (e.g., stolen personal token, SSH key, browser cookie, or login password).
- An adversary compromising an application container image in a CI/CD pipeline that leads to a vulnerability that later can be exploited in the production environment.
The question then arises: How can the different scanners deployed across the software supply chain put these threat scenarios on our radar?
Vulnerabilities, vulnerabilities, vulnerabilities
A single vulnerability in a component can have far-reaching implications for the overall security and stability of the chain. Once the scanners mentioned above are deployed, the security team is almost certain to receive an extensive list of vulnerabilities. Each scanner ranks the criticality of vulnerabilities using a different framework. For instance, a DAST tool may employ the OWASP Top 10 vulnerability framework to assess risks.
On the other hand, a Cloud scanner might utilize the Common Vulnerability Scoring System (CVSS), considering factors such as the presence of one or more CVEs, the technical aspects of the CVE, its exploitability (Temporal), and the environmental aspects, which many organizations overlook. Some organizations incorporate Exploit Prediction Scoring System (EPSS) into the equation for better results, but EPSS scores are only available when there is already a complete CVE published on the vulnerability. Consequently, one crucial question becomes challenging to answer: What is the actual risk within my vulnerability list?
For this question an approach the security team can take is by using “Attack Paths”.
Attack paths: connecting the dots
What is an attack path?
An attack path is a visual representation of the ongoing flow that occurs during the exploitation of potential vectors by an attacker. The attack path “connects the dots” and is looking at the entire context of an imposed risk.
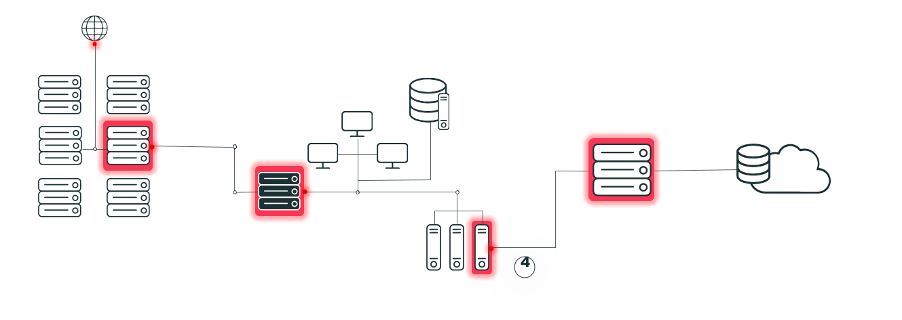
How can we identify attack paths?
Starting from the example of a network exposure, the organization’s web application runs in a container. We can continue to the asset origin, in this case the code project, and the container image and its base image origin. That takes us all the way to the other assets that this asset is connected to, which ultimately includes the organization’s “crown jewels.” These are often the main goal of an attack.
Once we have documented this path, we can use this mapping to identify the vulnerabilities found along each part and identify potential attack scenarios. This can be done using a framework like the MITRE ATT&CK framework, where we now correlate between Vulnerabilities and Techniques that can be used to exploit them.
Once we have successfully mapped as many paths as possible, we gain a view into the overall potential attack paths in our system, all the way from deployment to each component origin in the supply chain. This gives us a deeper and wider perspective for evaluating vulnerabilities with the actual risk they impact.
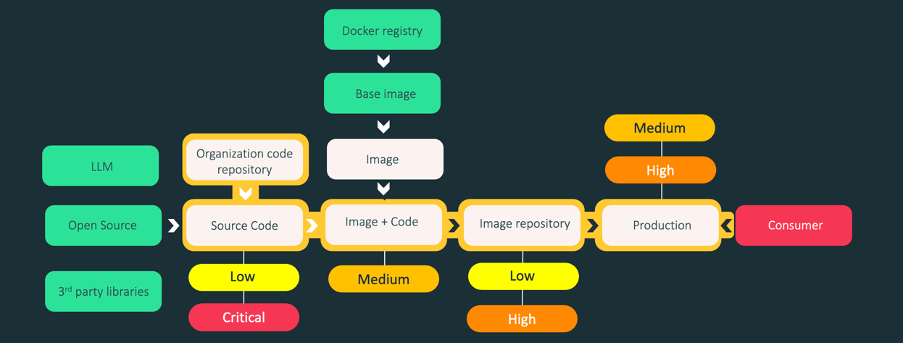
Next steps
Charting the journeys of vulnerabilities leaves us in no doubt of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:
- CVSS v4.0 – what you need to know
- Can you trust ChatGPT’s package recommendations?
- MITRE ATTACK framework – Mapping techniques to CVEs
- Exploit maturity: an introduction
- OWASP Top 10 vulnerabilities 2022: what we learned
And finally…
Don’t get found out by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your threat environment and lets you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.