-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
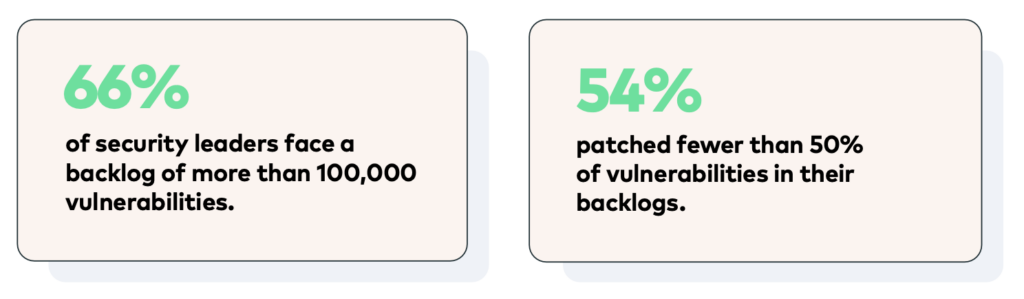
In 2019, Ponemon surveyed organizations that had fallen prey to major security breaches. 60% of these breaches involved known risks with available patches that simply hadn’t been applied. Around 80% of cyberattacks in 2020 were from exploits that were at least three years old. The urgent need to utilize the best modernized tools and methods is at an all-time high, with the cost of a data breach in 2022 a record $4.35 million per incident. With the stakes this high, it’s important that organizations learn and implement the best approaches to vulnerability management. In this article, we’ll address the best procedures for identifying and handling cyber threats.
Vulnerability management is the multi-stage process of handling cyber risk for an organization. Today’s vulnerability management process involves identifying security weaknesses in infrastructure, cloud-based systems, and applications. As we head into 2024, this process is essential in the face of mounting cyber risk for organizations:
Over the years, vulnerability management has gone from a predominantly manual process to more sophisticated, automated procedures. It requires specialized tools to identify and prioritize risks so that proper strategies can be designed and implemented, with the ultimate goal of preventing an IT system security breach.
Vulnerability management follows a procedural system of identifying threats—a framework to prioritize and treat threats, laying a foundation for long-term management specific to every organization’s operations and needs.
In the late 90s and early 2000s, the first vulnerability scanners were released. Relatively speaking, there weren’t a lot of vulnerabilities in those days compared to today. For example, in the year 2000, there were 1,020 disclosed vulnerabilities. In comparison, 2018 saw a staggering 16,555 disclosed vulnerabilities.
The scanning and remediation process in those days was very much a manual process. The scanning software would provide a report of vulnerabilities found, which had to be analyzed for accuracy and validity by someone in the IT department. The report would be sent to IT department heads for review and approval. Then once approved, the System Administrators would remediate vulnerabilities and follow-up with another vulnerability scan to verify the results.
Averaging only about 85 vulnerabilities per month, this manual process was manageable, and there wasn’t a real need to automate vulnerability management. As the number of vulnerabilities increased in subsequent years, and the importance of vulnerability management became more evident to organizations, manual scanning and remediation plans would soon become impracticable.
Fast forward by a decade, and the number of vulnerabilities steadily increased with 4,652 reported in 2010 and 6,447 new vulnerabilities in 2016. However, starting in 2017, an explosion of vulnerabilities began that has continued into 2019.
There’s no doubt that the seemingly never-ending barrage of new vulnerabilities cannot be managed with a manual vulnerability management plan. Manually reviewing and prioritizing known vulnerabilities is unrealistic and just too time-consuming.
Whether your remediation processes resemble the ‘early days’ method or you have implemented more modern tools and processes, it’s crucial that you take a look at your vulnerability process and ask: am I taking the necessary steps to make my environment as secure as possible to meet the modern threat landscape?
An organization’s cyber security team is responsible for protecting its assets against cyberattacks. The Chief Information Security Officer (CISO) typically oversees cyber security operations.
Cyber security teams are responsible for protecting an organization’s information, ensuring employees follow best security practices, and investigating any security incidents that occur.
Without vulnerability management, an organization is an easy target for ransomware, malware, and other cyber attacks that can cause a network’s software and hardware to fail, which can compromise:
Every day, attackers get more sophisticated, carrying out cyber attacks more frequently. Ongoing vulnerability management is necessary to decrease the likelihood of an attack. The following are just a few ways cyberattacks exploit weaknesses in an organization’s network:
A vulnerability is a weakness in an IT system and any device connected to it that can be used as an attack vector. Known vulnerabilities are added to a shared database, requiring security teams to remain aware and vigilant. Identified threats are tracked as Common Vulnerabilities and Exposures (CVEs), providing a nomenclature for known flaws and their definitions.
As technology changes, so do the kinds of vulnerabilities that can attack an organization. Currently, some of the most prevalent vulnerabilities include cloud-based vulnerabilities, application-based vulnerabilities, configuration errors, and other weaknesses.
Cloud computing is transformative in how tech businesses operate, but it does represent new challenges in cyber security. Now, even the most security-conscious organizations face threats that come as a result of operating in an non-isolated system. Poorly configured servers, improper firewall settings, or substandard patching on the cloud server can expose a network to new risks.
Cloud vulnerabilities bring new challenges, where users are unaware of their responsibility for security protections, the skill level required in complex cloud setups, and the hybrid public-private nature of cloud services.
These are known errors in software that can be exploited to breach a network’s security. Unpatched or non-updated software can leave an opening for cyber attacks that not only affect the security of the network but also can attack the system hardware and firmware.
When a network’s systems aren’t properly configured, it can leave them open to cyber attacks. These issues can be as simple as leaving a system’s password at the default setting or a network being set as a public, unprotected login that anyone can access. It’s often the most basic mistakes that are the easiest to exploit.
Even when software has been updated and patched without known errors, there are still potential vulnerabilities. Weaknesses could include a lack of encryption for stored data or data that is imported from an insecure, outside source. Many companies take security seriously but fail to recognize the possibility of their own employees unwittingly introducing a threat from outside the system.
White paper: Cloud security blind spots (and how to avoid them)
Vulnerability management used to be handled with very little automation. This was possible when there were far fewer cyberattacks and known vulnerabilities. Today, it’s inconceivable that threats could be handled without automation.
Much of today’s methodology centers around the need to keep IT information secure and private—often meaning organizations are reluctant to make that information accessible to outside cyber security professionals.
This is a thorough methodology of cyber security in which risks are prioritized and remediated based on the results of deep analysis. RBVM offers a proactive approach that takes the highest threats into account while also prioritizing what is feasible against what is the most costly and time-intensive.
On-demand webinar: Risk-based Vulnerability Management for Continuous Compliance
Most of the cyber security industry treats vulnerability management in five main steps:
The first step in a network’s vulnerability management program is identifying weak points that need to be protected. Identifying vulnerabilities calls for evaluating an organization’s susceptibility to attacks, checking whether any systems have already been breached, and making that information available to teams who need to coordinate an action plan through reports and metrics.
This stage requires scanning every stored file, every app installed, and every hardware device attached to a network. This can be challenging to a group’s workflow, slowing down systems with continuous scans, meaning companies have to develop the best compromise between performance and security. Once the organization’s environment has been scanned, that data must then be consolidated to ensure efficiency of the cyber risk mitigation process.
White paper: The best free and open source tool for cyber risk assessment
At the evaluation stage of vulnerability management, risks are ranked according to a Common Vulnerability Scoring System (CVSS), so they can be organized into a plan of action. More mature vulnerability management programs will also enrich and correlate the risk data and find underlying patterns that might form attack paths across assets and an increasingly large and complex attack surface.
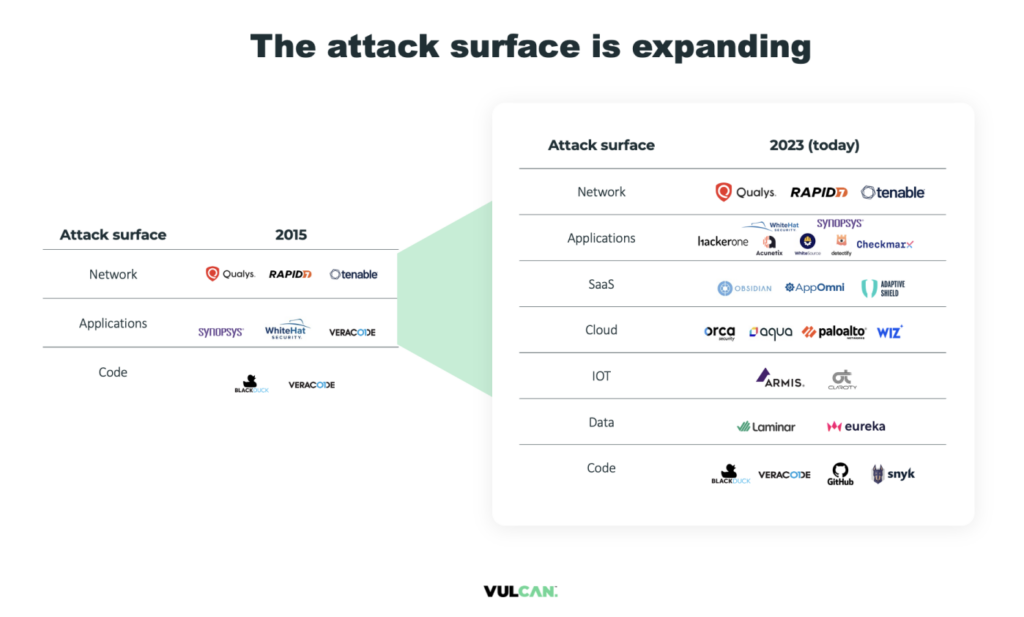
To be the most effective, cyber security experts develop a strategy for handling vulnerability risks. For instance, some threats are more dangerous than others, while other risks may be much more likely to occur. Somewhere in the complex array of possibilities is the right balance of determining the most pressing threats.
Prioritizing vulnerability risks begins with organizing system vulnerabilities according to their CVSS ranking so they can be dealt with in the most efficient and responsible way.
At this stage, the cyber security team can design a strategy for handling vulnerabilities according to their level of risk and immediacy—a process that is always unique to the organization.
For best results, vulnerabilities should be prioritized according to the impact they represent to the organization’s unique environment. What may be a top-level threat for one group may have less of an impact on another company’s day-to-day business. Prioritization considers all of the nuances of risk and impact when designing a strategy.
A comprehensive approach to security means implementing an action plan—treating the diagnosed vulnerabilities. The strategy for treating vulnerabilities can involve numerous processes, including:
Vulcan Cyber® breaks down vulnerabilities into a step-by-step process of remediation and mitigation. Remediation resolves threats when it is possible to remove them completely, while mitigation takes a proactive approach to reduce the likelihood of any impact from a threat that isn’t feasible to prevent.
Reporting vulnerabilities provides the organization with visualization and data on the steps taken to protect their network, along with outlining trends that need continuous monitoring. It also provides data that may be required for compliance and regulatory obligations for financial institutions and healthcare organizations, for instance.
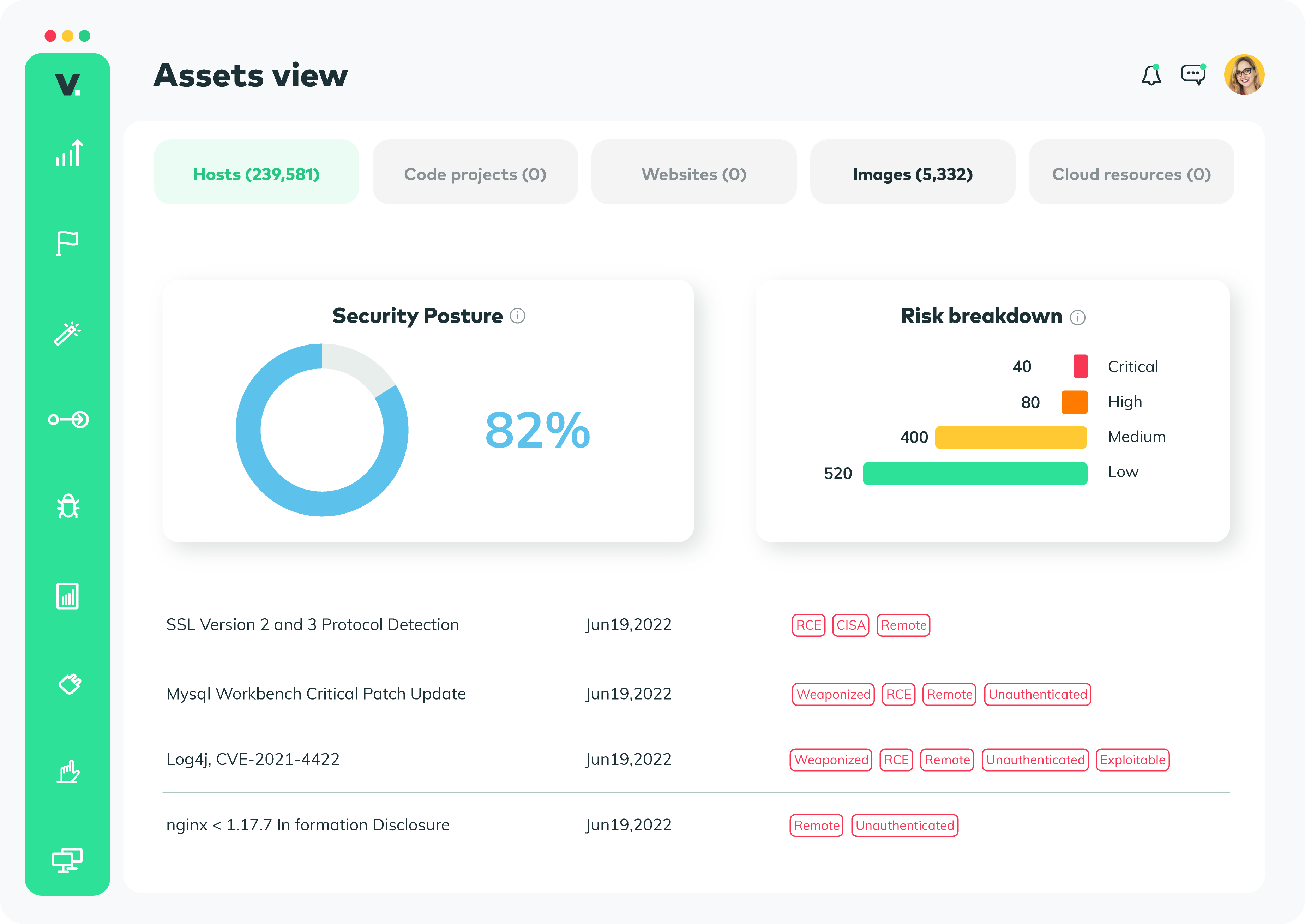
At the evaluation stage of security vulnerability management, risks are ranked according to a CVSS score so they can be organized into a plan of action built around:
The CVSS ranking of vulnerabilities rates the severity of a risk as:
It’s important to note that while the CVSS score can serve as a good starting point, teams must consider the cyber risk posed by each vulnerability, specifically in relation to their organizations.
Vulnerability management is the complete cycle of handling cyber threats by identifying, evaluating, treating, and reporting vulnerabilities. A vulnerability assessment is just one small part of vulnerability management, where cyber security experts scan an organization’s entire system to gather intelligence, such as:
Assessment requires frequent scanning sessions to collect data to develop an action plan, prioritizing risks that need the most urgent action.
Gone are the days of manual system scans and isolated networks. Protection from today’s constant onslaught of cyberattacks requires high-paced, automated scanning of your environment and cloud connections, along with constant live updates of the most current exploit intelligence.
Our goal at Vulcan Cyber is to demystify the cyber risk management lifecycle. Our platform automatically unifies risk data, finds security gaps, and helps security teams make decisions by leveraging data from scanners and other threat intelligence sources. It integrates with all of your existing security tools and fits seamlessly within your existing cyber security ecosystem.
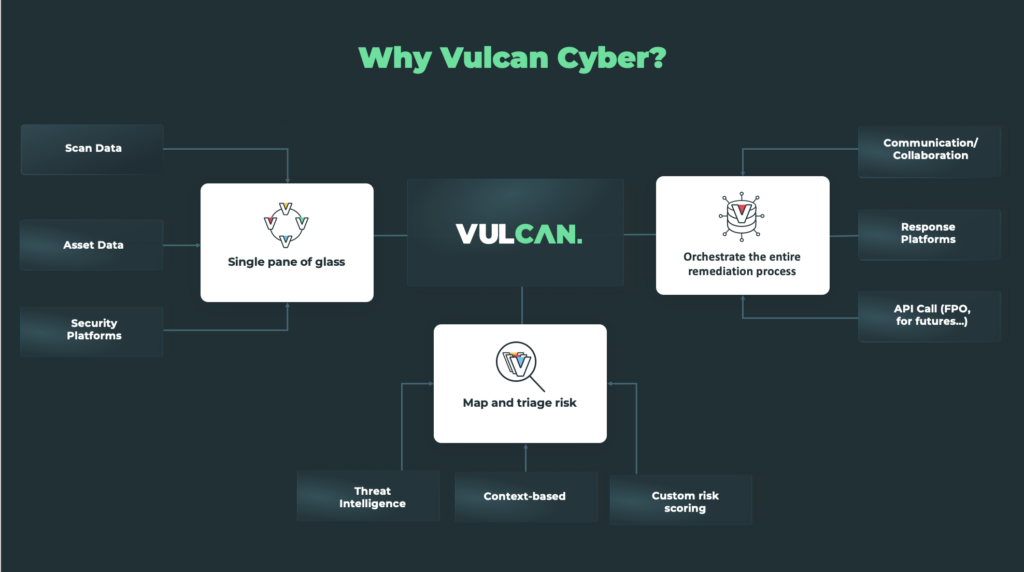
Our platform connects to the best central databases, sharing information about known exploits with organizations, so they can remediate their systems without exposing their internal data.
On-demand webinar: How to Achieve Complete Cyber Risk Management
Vulnerability management is an ongoing, proactive process, frequently automated, designed to protect your computer systems, networks, and enterprise applications from cyberattacks and data breaches by continuously identifying and addressing security vulnerabilities.
The objective of a successful Vulnerability Management Program is to comprehend and gain control of the threat environment with the aim of minimizing the attack surface and mitigating risk.
The initial phase in the vulnerability management process is usually a vulnerability assessment. This step entails employing scanners to collect data from devices and systems within the corporate network and then comparing this data against known vulnerabilities that have been disclosed by software vendors.
Vulnerability management and vulnerability assessment are distinct concepts. Vulnerability management is a continuous process, in contrast to a vulnerability assessment, which is a single-time evaluation of a host or network. While vulnerability assessment forms a component of the vulnerability management process, the reverse is not true.
The Common Vulnerabilities and Exposures (CVE) system is a publicly accessible database that catalogs information security vulnerabilities. Each vulnerability is uniquely identified by a CVE number, distinguishing it from others in the list.
CVSS assigns a severity score ranging from 0 to 10 to each vulnerability, with 0 indicating a less significant vulnerability and 10 representing the most severe. This scoring is applicable when relying solely on the CVSS for vulnerability assessment.

Vulnerability management is all about process, people and tools
Our automation accelerates risk remediation across infrastructure, cloud, and applications. Organizations that are ready to benefit from our comprehensive enterprise management and remediation system can try it free today. If you’re ready to protect your organization with the best cyber risk remediation, schedule a time for us to demonstrate the Vulcan Cyber enterprise solution with specific, customized functions for your security team.