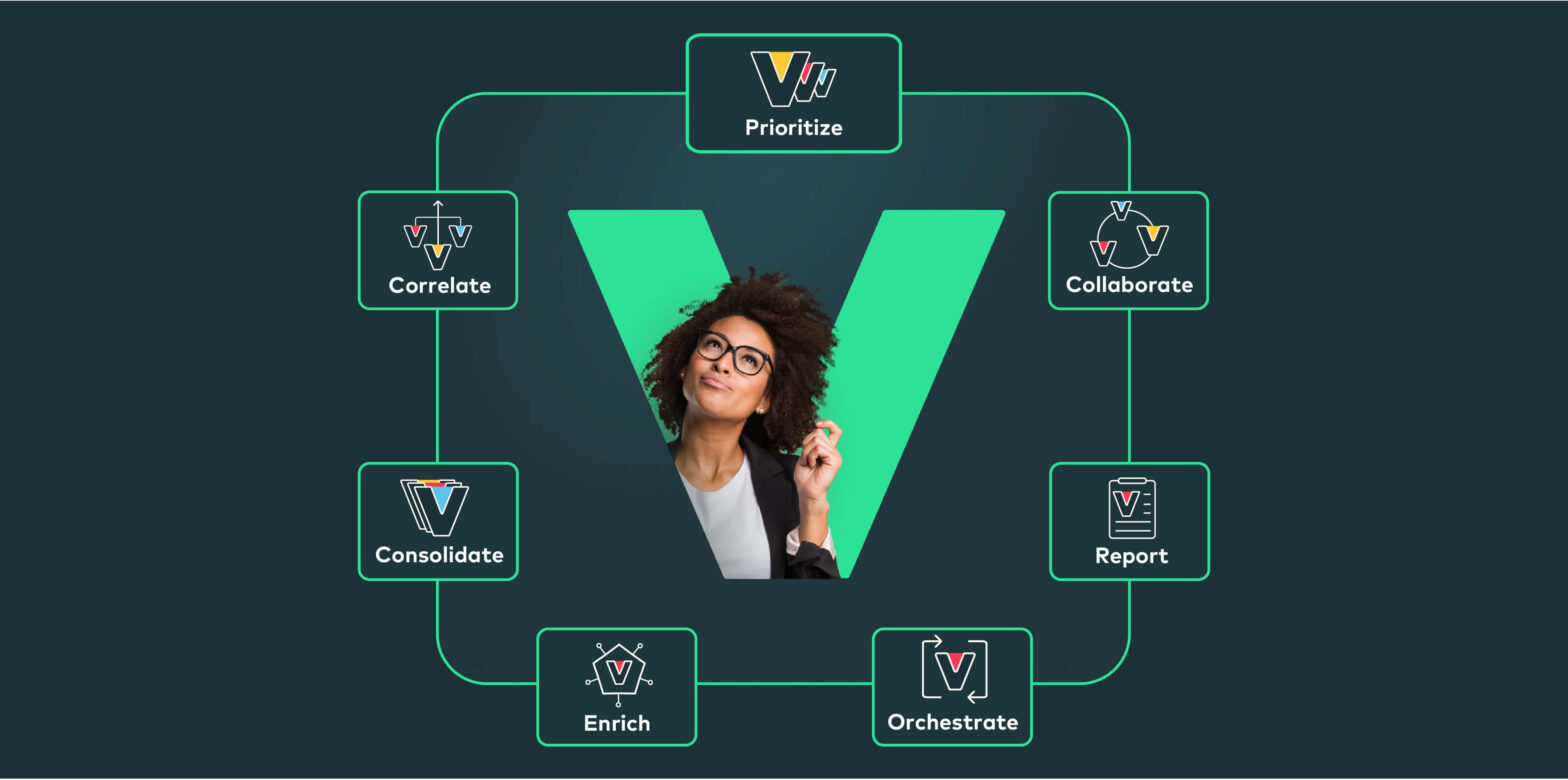
The business of vulnerability management across networks, clouds and applications tends to be a complex process that involves several stakeholders and demands multiple actions such as identifying, prioritizing, managing, and reporting vulnerabilities in your system. Determining the success or failure of a vulnerability management program cannot be based solely on how many vulnerabilities were fixed… Continue reading 7 stages of the vulnerability management lifecycle
7 stages of the vulnerability management lifecycle