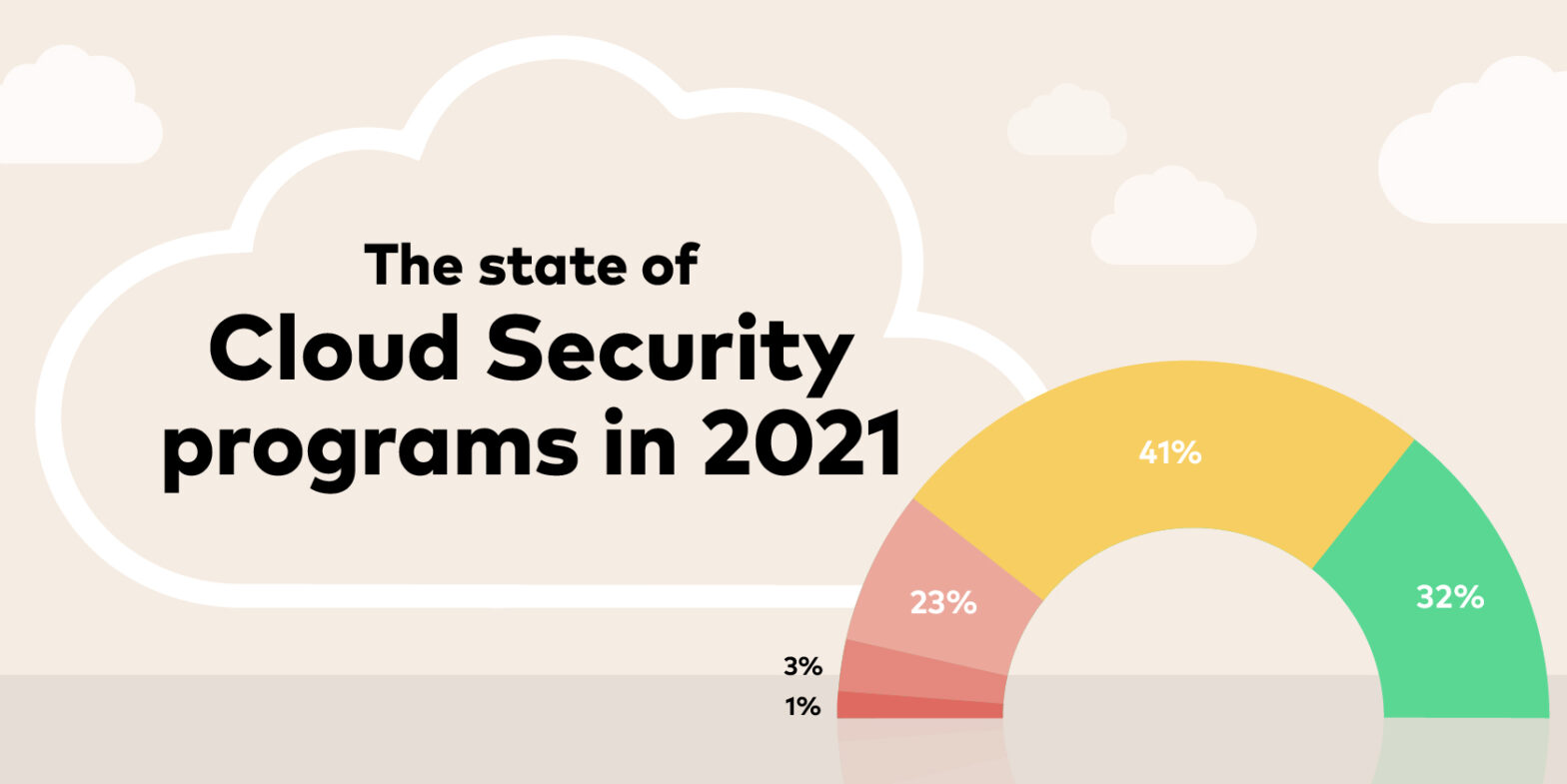
It’s no surprise that 2021 saw a record number of vulnerabilities. It reflects a worrying trend of an expanding attack surface and limited security resources. But even the best-equipped IT security teams are faced with the issue of not fully understanding their risk when it comes to vulnerability management. With data from Gartner, other industry… Continue reading The state of vulnerability management programs in 2021
The state of vulnerability management programs in 2021