Spend any time in cyber security, and you’ll know how deep the vulnerability rabbit hole goes. Log4j. Spring4shell. Follina. The list goes on and on and on. Security researchers and bug bounty hunters trawl the sprawling wild west of application, network, and cloud environments, in search of the critical openings that might let an attacker in. It’s tireless work. It needs to be.
At Vulcan Cyber, we empower organizations to finally gain full control of their cyber risk. And a huge part of our work is having our finger on the pulse of emerging vulnerability trends, so that our community is never caught by surprise.
That’s why we’re officially introducing Voyager18 – our in-house team of expert researchers dedicated to uncovering all the patterns, threats, and mitigation actions before theoretical breaches become very real problems.
Recently, the team mapped out the MITRE ATT&CK framework to CVEs, highlights of which you can read below. The full white paper was written by Lior Ben-Dayan, and supported by the Voyager18 team (see the team bios below).
What you’ll learn
What is the MITRE ATT&CK framework?
The MITRE ATT&CK framework is a dictionary that centralizes techniques used by threat actors along with cyber attacks, categorized as “milestones” for attackers to reach before arriving at their end goal. Mapping offensive techniques to CVEs allows defenders to follow the “flow” of a CVE, breaking down the steps and actions taken during its exploitation, and identifying what can be achieved (Impact) following successful exploitation.
Mapping CVEs to MITRE
While many have tried to map ATT&CK techniques to CVEs, these efforts have largely proved ineffective. MITRE also released its own community-driven methodology for mapping, but – while promising – it has not been updated recently and so is limited in its usefulness.
The Voyager18 approach uses the MITRE methodology as a basis for its own project. Using CVE descriptions, CWE data, and CVSS vector information – alongside text analysis and machine learning processes – the team was able to map relevant techniques to each CVE:
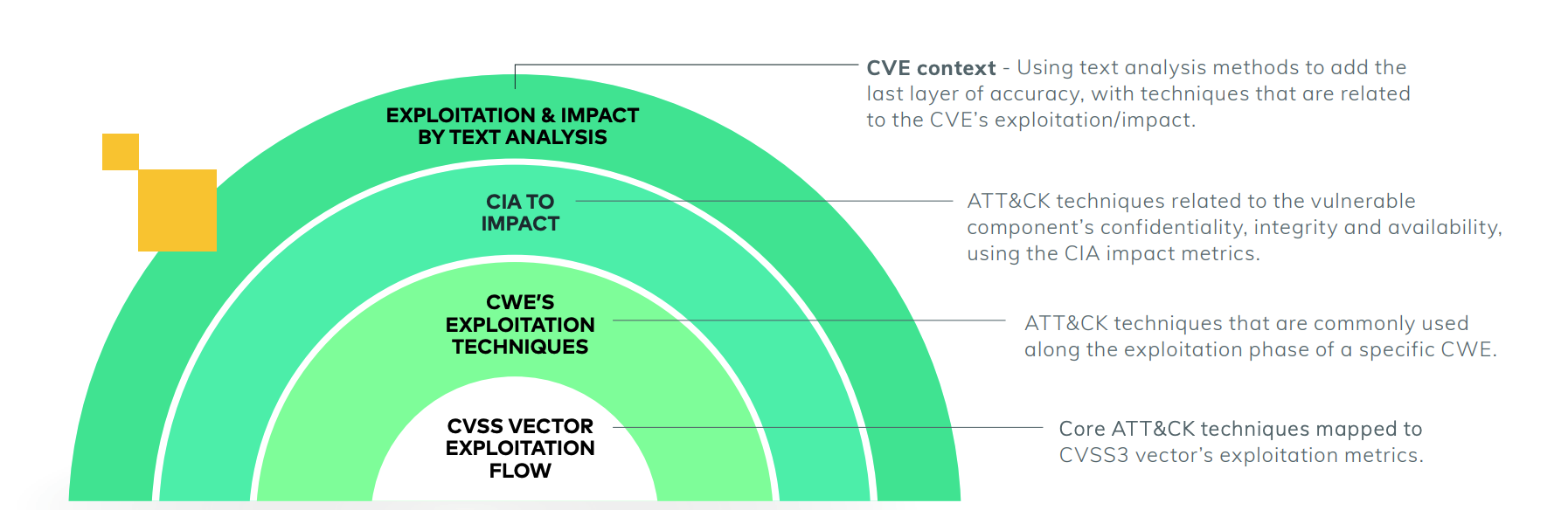
CVSS3 Vector
The CVSS vector of a vulnerability gives us an overall insight, regarding the requirements and behavior of a vulnerability’s exploitation flow. For instance, we can infer whether the exploitation requires a phishing campaign against the victim, or whether the attacker has to be granted privileges prior to the exploitation.
CWE
The CWE of a vulnerability tells us the weaknesses under the hood. By knowing the weakness, or vulnerability type of a CVE, we can sometimes automatically map relevant techniques to the CVE.
CIA
Confidentiality, integrity and availability of a CVE might help us infer the impact of a vulnerability, which could be reading local data, destruction of data, loss of availability etc.
Text Analysis
Finally, though we initially avoided textual analysis, we found it difficult to map ATT&CK techniques to CVEs solely using patterns of CWEs and CVSS3 vectors. In order to overcome these difficulties, we added to the mapping process some text analysis methods. We started by extracting phrases from CVE descriptions using the RAKE (Rapid Automatic Keyword Extraction) algorithm. Then we manually selected meaningful phrases for each CWE and grouped them into groups with similar or close semantic meanings that characterize the CWE.
Each phase of the mapping process comes together to form a powerful tool for identifying patterns in the MITRE ATT&CK framework:
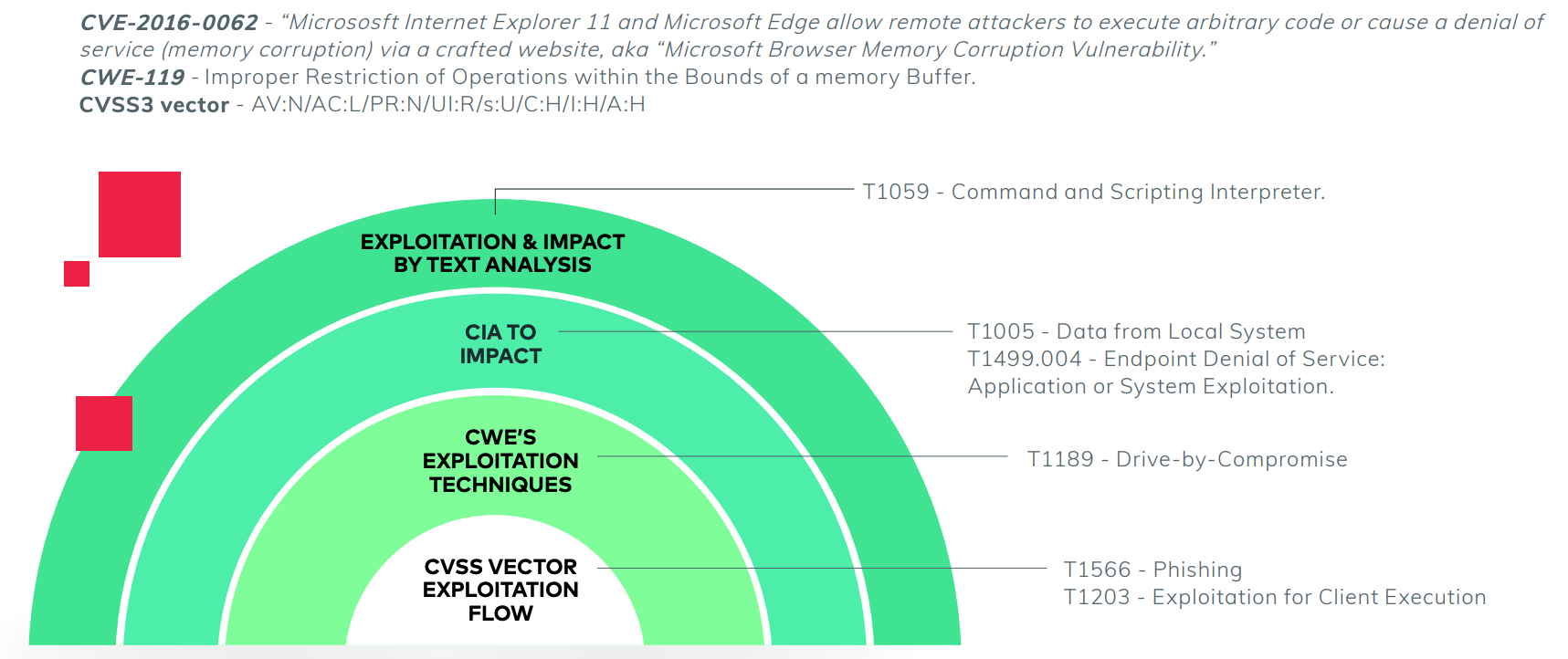
Next steps
We’re only at the beginning of our research and there are still many directions we can take. Distinguishing between different types of CPEs and using that understanding to better map ATT&CK techniques, “inheritance” between CWEs, and finding an efficient way to deal with CVEs with poor descriptions, are all areas which will be explored.
When it comes to textual analysis, the next step is to extract keywords also from ATT&CK techniques, tagging them to the semantic groups we created with the CWE keywords for matching CWEs and ATT&CK techniques.
Finally, we can research isolating phrases that are unique per CWE and map them to ATT&CK techniques, and find overlapping phrases between CWEs, in order to apply known mapped techniques of one CVE to another.
Meet the team
Ortal Keizman – Head of research
Lior Ben-Dayan – Security researcher

Bar Lanyado – Security researcher
Karin Weinberg – Research software engineer
Moti Shakuri – Backend engineer
Yiftah Szoke – Data analyst
The MITRE ATT&CK mapping project is part of our wider commitment to providing comprehensive resources and tools to our community for better understanding, prioritizing and reducing cyber risk. Get all of our updates and be part of the conversation by joining our Slack channel.













