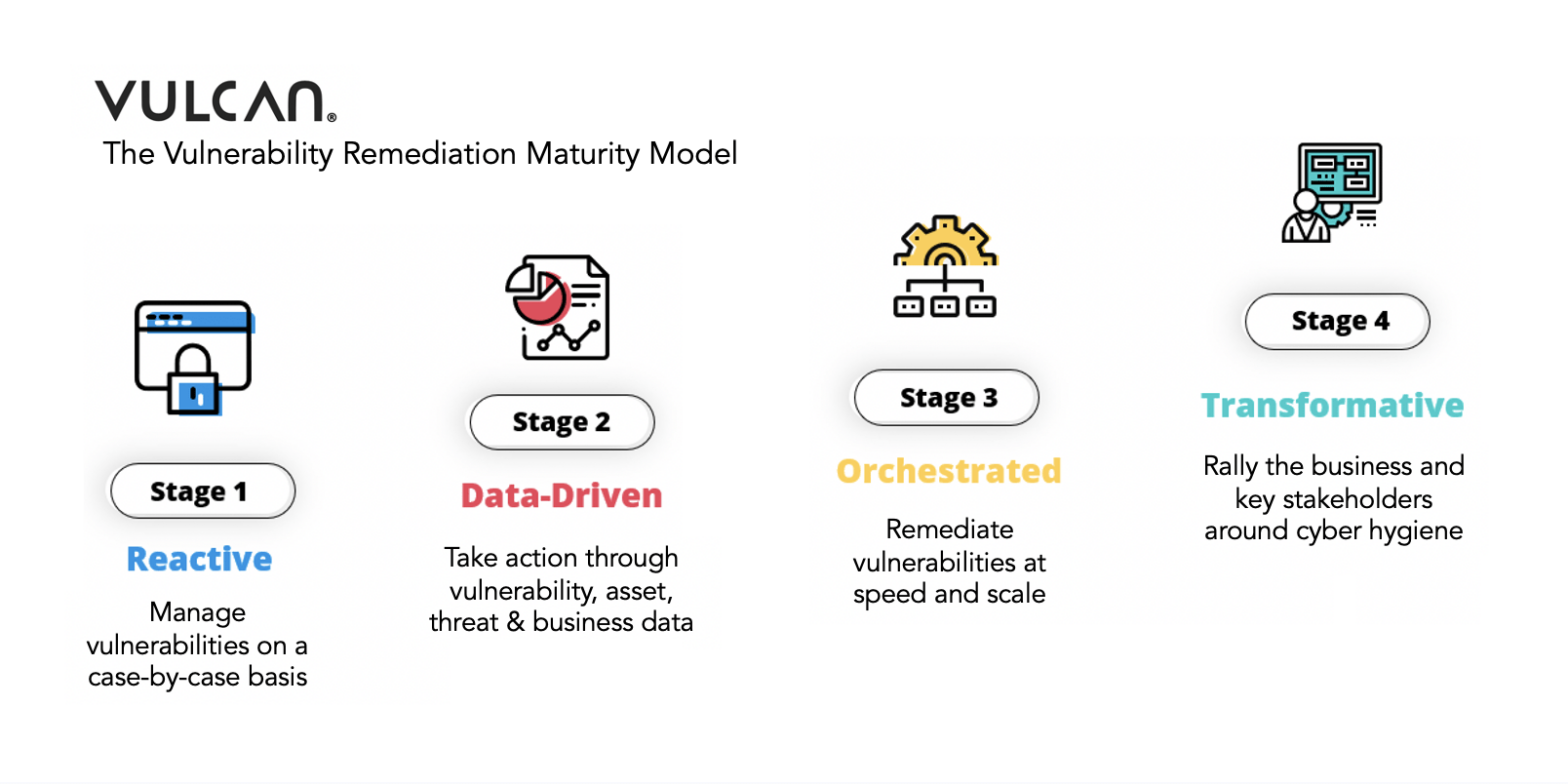
Patch management—the process businesses use to apply fixes or patches to software—sounds straightforward. But in reality, it’s a complex and high-stakes task, especially in a production environment. Complicating factors include the volume of patches, the prioritization of patches, and the choice of when to patch. Streamlining the process with patch management best practices reduces risks… Continue reading Patch management mastery: 8 essential best practices for better security
Patch management mastery: 8 essential best practices for better security